What is the name of the command for combining multiple selected cells into a single cell?
A. Combine Cells
B. Distribute Cells
C. Merge Cells
D. Split Cells
Answers
Related Questions
Choose the best option to answer each question. Which output device allows a user to create a copy of what is on the screen? printer speakers earphones display or monitor
Answers
Answer: printer
Explanation:
1. The type of browser that allows you to access audio and video content is known as A). Graphic based browser B) Graphic browser Text browser based browser Text
Answers
The type of browser that allows you to access audio and video content is known as Text browser.
What is web browser in HTML?The web browser is known to be a kind of an application software that is made to look through www (World Wide Web).
It is one that helps to give an interface between the server as well as the client and often make requests to the server for web documents.
Therefore, The type of browser that allows you to access audio and video content is known as Text browser.
Learn more about Web Browser? from
https://brainly.com/question/22650550
#SPJ1
Question 18 of 50
A value inventory is a self-assessment test that measures the importance of certain values in order to guide an individual
his/her career path.
True
False
Answers
Answer:
true trust
explanation trust
The final stages of the data science methodology are an iterative cycle between Modelling, Evaluation, Deployment, and Feedback.
a. True
b. False
Answers
Answer: True
Explanation:
The Data Science Methodology is simply referred to as an iterative and continuous methods that is required by data scientists to guide them on the approach that they'll use to tackle and solve problems typically through a number of steps.
It should be noted that the final stages of the data science methodology are an iterative cycle between Modelling, Evaluation, Deployment, and Feedback. The main aspects involves:
• Problem
• Approach;
• Requirements
• Collection
• Understanding
• Preparation
• Modelling
• Evaluation
• Deployment
• Feedback.
Therefore, the above statement is true.
Which statement correctly explains why televisions became less bulky?
Answers
Answer:
The old cathode Ray tube technology was replaced by the less bulkier and more modern liquid crystal display and LED technology.
Explanation:
The old cathode ray tube uses the principle of electrical discharge in gas. Electrons moving through the gas, and deflected by magnetic fields, strike the screen, producing images and a small amount of X-rays. The tube required more space, and consumed more electricity, and was very bulky. The modern technologies are more compact and consume less power, and can been designed to be sleek and less bulky.
A network security analyst received an alert about a potential malware threat on a user’s computer. What can the analyst review to get detailed information about this compromise? Check all that apply
Answers
Complete Question:
A network security analyst received an alert about a potential malware threat on a user’s computer. What can the analyst review to get detailed information about this compromise? Check all that apply.
A. Logs.
B. Full Disk Encryption (FDE).
C. Binary whitelisting software.
D. Security Information and Event Management (SIEM) system.
Answer:
A. Logs.
D. Security Information and Event Management (SIEM) system.
Explanation:
If a network security analyst received an alert about a potential malware threat on a user’s computer. In order to get a detailed information about this compromise, the analyst should review both the logs and Security Information and Event Management (SIEM) system.
In Computer science, logs can be defined as records of events triggered by a user, operating system and other software applications running on a computer. Log files are used to gather information stored on a computer such as user activities, system performance and software program.
Security Information and Event Management (SIEM) system is the process of gathering and integration of all the logs generated by a computer from various software application, service, process, or security tool.
These logs collected through the SIEM are shown in a format that is readable by the security analyst and this help in real-time detection of threats.
Hence, logs and SIEM systems are important tools for network security analyst for detection of threats in real-time and event management functions.
The dealer’s cost of a car is 85% of the listed price. The dealer would accept any offer that is at least $500 over the dealer’s cost. Design an algorithm that prompts the user to input the list price of the car and print the least amount that the dealer would accept for the car. C++
Answers
Here is an algorithm in C++ that prompts the user to input the list price of the car and prints the least amount that the dealer would accept for the car:
#include <iostream>
using namespace std;
int main() {
double list_price, dealer_cost, min_accepted_price;
const double DEALER_COST_PERCENTAGE = 0.85;
const double MIN_ACCEPTED_PRICE_OVER_COST = 500;
cout << "Enter the list price of the car: ";
cin >> list_price;
dealer_cost = list_price * DEALER_COST_PERCENTAGE;
min_accepted_price = dealer_cost + MIN_ACCEPTED_PRICE_OVER_COST;
cout << "The least amount the dealer would accept for the car is: $" << min_accepted_price << endl;
return 0;
}
The algorithm starts by including the library iostream and declaring the namespaces. Then it declares the variables that will be used in the program (list_price, dealer_cost, min_accepted_price) and the constants that will be used (DEALER_COST_PERCENTAGE and MIN_ACCEPTED_PRICE_OVER_COST). Then it prompts the user to enter the list price of the car. Next, it calculates the dealer's cost by multiplying the list price by the dealer cost percentage and the minimum amount the dealer would accept by adding the dealer's cost to the minimum accepted price over cost. Finally, it prints the least amount the dealer would accept for the car.
Design the logic for a program that allows a user to enter a number. Display the sum of every number from 1 through the entered number. In pseudocode or flow chart.
Answers
Answer:
START
DECLARE total_sum = 0
DISPLAY "Enter a number: "
GET user_input
FOR i from 1 to user_input:
SET total_sum = total_sum + i
END FOR
DISPLAY "The sum of every number from 1 through " + user_input + " is " + total_sum
END
You just figured out the root cause of an application error. You changed some configurations on the affected machines and verified that the users have full functionality. What should you do next?
Answers
After resolving the application error and verifying that users have full functionality,the next step is to document the changes made and the steps taken to resolve the issue.
How is this so?This documentation is crucial for future reference, troubleshooting, and knowledge sharing within the team.
Also, it is important tocommunicate the resolution to the relevant stakeholders,such as users or supervisors, to ensure they are aware of the resolution and can provide f eedback if necessary.
Learn more about application error at:
https://brainly.com/question/30062195
#SPJ1
Write the Python code for a program called MarathonTrain that asks a runner to enter their name, and the maximum running distance (in km) they were able to achieve per year, for 4 years of training. Display the average distance in the end. 4
Answers
C++ PLEASE HELP... I ALREADY HAVE CODE WRITTEN BUT IM NOT GETTING THE CORRECT OUPUT!!!
Write code to read a list of song durations and song names from input. For each line of input, set the duration and name of newSong. Then add newSong to playlist. Input first receives a song duration, then the name of that song (which you can assume is only one word long). Input example: 424 Time
383 Money
-1
"The issue is I keep getting two spaces after '_' instead of just one."
HINTS:
"songDuration is assigned with the first song's duration before the while loop. The while loop checks if songDuration is greater than or equal to zero. If so, the while loop is entered.
The following operations are repeated in the while loop:
songName is assigned with the song's name.
Then, newSong.SetDurationAndName() sets newSong's duration and name data members.
push_back() appends newSong to playlist.
songDuration is assigned with the next song's duration.
The while loop continues to add songs to playlist until songDuration is assigned with a value less than zero."
#include
#include
#include
using namespace std;
class Song {
public:
void SetDurationAndName(int songDuration, string songName) {
duration = songDuration;
name = songName;
}
void PrintSong() const {
cout << duration << " - " << name << endl;
}
int GetDuration() const { return duration; }
string GetName() const { return name; }
private:
int duration;
string name;
};
int main() {
vector playlist;
Song newSong;
int songDuration;
string songName;
unsigned int i;
cin >> songDuration;
while (songDuration >= 0) {
//code goes here
getline(cin, songName);
newSong.SetDurationAndName(songDuration, songName);
playlist.push_back(newSong);
//code ends
cin >> songDuration;
}
for (i = 0; i < playlist.size(); ++i) {
newSong = playlist.at(i);
newSong.PrintSong();
}
return 0;
}
MY OUTPUT:
163 - Breathe
413 - Time
383 - Money
123 - Eclipse
OUTPUT:
163 - Breathe
413 - Time
383 - Money
123 - Eclipse
PLEASE HELP- thank you
Answers
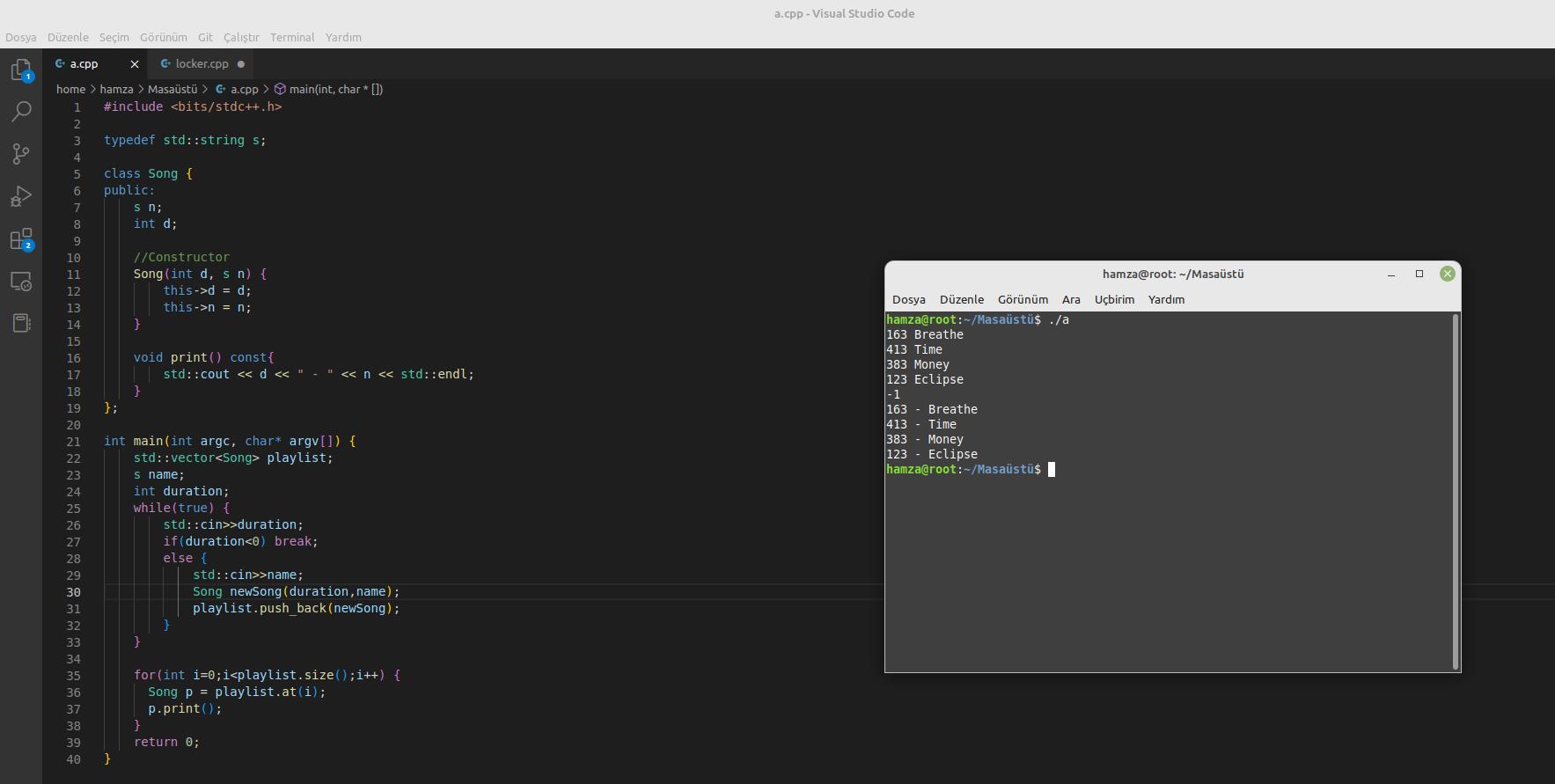
By writing the getter() and setter() methods without using them, you extend the runtime of the program. Also, the -Wunused-variable marker is automatically used by your compiler. I edited your code for you, there is no problem.
#include <bits/stdc++.h>
typedef std::string s;
class Song {
public:
s n;
int d;
//Constructor
Song(int d, s n) {
this->d = d;
this->n = n;
}
void print() const{
std::cout << d << " - " << n << std::endl;
}
};
int main(int argc, char* argv[]) {
std::vector<Song> playlist;
s name;
int duration;
while(true) {
std::cin>>duration;
if(duration<0) break;
else {
std::cin>>name;
Song newSong(duration,name);
playlist.push_back(newSong);
}
}
for(int i=0;i<playlist.size();i++) {
Song p = playlist.at(i);
p.print();
}
return 0;
}
To control costs, a company provides a limited number of users with company phones. One of these users opens a support ticket because the phone no longer allows internet browsing over a cellular connection. The user acknowledges that the phone worked before the user's child streamed several movies using the device. Which of the following describes why the phone cannot browse the internet?
OA.
The Child accidentally connected to a neighbor's WLAN.
ОВ
The company's group policy disabled the device.
Oc.
The device has a data cap and has reached that limit.
OD.
The device's plan has been unpaid.
Answers
Several factors could be at play if you are unable to access the internet: The router could be having problems, the firewall could be acting up, the wireless signal can be blocked or too weak to utilise, and there might be IP address conflicts.
What is internet?The Internet, sometimes known as "the Net," is a global system of computer networks. Users at any one computer can access information from any other computer, with permission, through this network of networks, known as the Internet (and sometimes talk directly to users at other computers). Kleinrock's experiment demonstrated the viability of a single network connecting two computers, but TCP/IP, developed by Cerf and Kahn, served as the foundation for a vast network of interconnected networks that was effective and interconnected, hence the name "Internet." A network of networks, the internet has several different varieties. With a wide range of electronic, wireless, and optical networking technologies connecting them, it comprises of public, commercial, academic, business, and government networks with local to worldwide reach.To learn more about internet, refer to:
https://brainly.com/question/2780939
#SPJ1
The phone may have exceeded its monthly data limit, causing the cellular connection to be blocked or throttled.
How to control costs, a company provides a limited number of users with company phones?The phone's SIM card may have been damaged or improperly installed, causing the cellular connection to be lost.The user's child may have accidentally enabled a data-saving feature on the phone, which could be blocking internet browsing over the cellular connection.The phone may have a hardware problem, such as a damaged antenna or a malfunctioning cellular modem, that is preventing the phone from connecting to the internet.The company may have blocked or restricted internet browsing on the phone for security reasons.It could be multiple reasons, but the above are some of the common reasons why a phone cannot browse the internet. To troubleshoot the issue, the support team will need to verify the phone's data usage, check for software updates, check the phone's settings, and possibly run diagnostic tests on the phone's hardware. Ultimately, the root cause of the issue will need to be identified and resolved in order to restore internet browsing on the phone.To learn more about phone refer:
brainly.com/question/23433108
#SPJ1
From which panel can you insert Header and Footer in MS Word?
Answers
Answer:
Insert tap is the answer
the answer is ..
insert tab
Investigate the different types of compact disks
Answers
Answer: the most common ones include CD-Audio, CD-ROM, CD-R, CD-RW, and CD-DA.
Explanation:
Compact Discs (CDs) are optical storage media that have been widely used for audio, data, and video storage. While there are several types of CDs, the most common ones include CD-Audio, CD-ROM, CD-R, CD-RW, and CD-DA.
1. CD-Audio: It is also known as a music CD or audio CD, CD-Audio is primarily used for storing and playing back audio recordings. It can hold up to 74 minutes (or 80 minutes with overburning) of uncompressed audio in the Red Book format. CD-Audio discs can be played on standalone CD players and most computer CD/DVD drives.
2. CD-ROM: CD-ROM stands for Compact Disc Read-Only Memory. These discs contain data that can only be read and not written or modified. CD-ROMs are widely used for distributing software, games, multimedia applications, and other types of data. They can store up to 700 MB (or 80 minutes) of data.
3. CD-R: CD-R (Compact Disc-Recordable) discs are blank discs that can be recorded once using a CD burner or writer. Once the data is written, it becomes permanent and cannot be erased or modified. CD-Rs are commonly used for creating backups, storing music compilations, and archiving data. They also have a capacity of 700 MB (or 80 minutes).
4. CD-RW: CD-RW (Compact Disc-ReWritable) discs are similar to CD-Rs but with the added ability to be erased and rewritten multiple times. This rewritable feature makes CD-RWs suitable for tasks that require frequent data changes or updates. The capacity of CD-RW discs is the same as CD-Rs, i.e., 700 MB (or 80 minutes).
5. CD-DA: CD-DA (Compact Disc Digital Audio) is another term for CD-Audio, indicating that the disc contains uncompressed audio in the standard Red Book format. CD-DA discs can be played on CD players and CD-ROM drives that support audio playback.
true or false. Two of the main differences between storage and memory is that storage is usually very expensive, but very fast to access.
Answers
Answer:
False. in fact, the two main differences would have to be that memory is violate, meaning that data is lost when the power is turned off and also memory is faster to access than storage.
I need help on 7.4 spinning arcs
Answers
The start angle is the angle of the first point in the arc and is measured in degrees. The significant processing of the start angle and sweep angle of a spinning arc determines the alteration in the starting point and the angle of the arc's sweep.
What is the context of this question?The context of this question is measured through the act of utilizing a standard tool or methodology in order to quantify, assess, or evaluate something. It is one of the methodologies of ascertaining the magnitude, amount, or size of a specific quantity effectively.
An efficacious address to this determination involves the significant utilization of various instruments in your day-to-day life. It typically includes rulers, scales, test tubes, etc. in order to determine the most accurate measurements. It is a fundamental concept in science and engineering and has many practical as well as theoretical applications.
To learn more about Start and sweep angles, refer to the link:
https://brainly.com/question/1598611
#SPJ9
Your question seems incomplete. The most probable complete question is as follows:
I need help on 7.4 spinning arcs, what does it mean to update the startAngle and sweepAngle?
The following equation estimates the average calories burned for a person when exercising, which is based on a scientific journal article (source): Calories = ( (Age x 0.2757) + (Weight x 0.03295) + (Heart Rate x 1.0781) — 75.4991 ) x Time / 8.368 Write a program using inputs age (years), weight (pounds), heart rate (beats per minute), and time (minutes), respectively. Output the average calories burned for a person. Output each floating-point value with two digits after the decimal point, which can be achieved as follows: print('Calories: {:.2f} calories'.format(calories))
Answers
A Python program that calculates the average calories burned based on the provided equation is given below.
Code:
def calculate_calories(age, weight, heart_rate, time):
calories = ((age * 0.2757) + (weight * 0.03295) + (heart_rate * 1.0781) - 75.4991) * time / 8.368
return calories
# Taking inputs from the user
age = float(input("Enter age in years: "))
weight = float(input("Enter weight in pounds: "))
heart_rate = float(input("Enter heart rate in beats per minute: "))
time = float(input("Enter time in minutes: "))
# Calculate and print the average calories burned
calories = calculate_calories(age, weight, heart_rate, time)
print('Calories: {:.2f} calories'.format(calories))
In this program, the calculate_calories function takes the inputs (age, weight, heart rate, and time) and applies the given formula to calculate the average calories burned.
The calculated calories are then returned from the function.
The program prompts the user to enter the required values (age, weight, heart rate, and time) using the input function.
The float function is used to convert the input values from strings to floating-point numbers.
Finally, the program calls the calculate_calories function with the provided inputs and prints the calculated average calories burned using the print function.
The '{:.2f}'.format(calories) syntax is used to format the floating-point value with two digits after the decimal point.
For more questions on Python program
https://brainly.com/question/26497128
#SPJ8
jss 1 computer text book
Answers
Note that the generation of computers that used integrated Circuit are called the Second Generation computers. (Option B)
What about Second Generation computers?Throughout the late 1950s and 1960s, a second-generation computer had circuit boards loaded with individual transistors and magnetic-core memory.
These computers remained the standard design until the late 1960s, when integrated circuits appeared, resulting in the third-generation computer.
It was created in 1947 at Bell Labs by three people: William Shockley, Walter Houser Brattain, and John Bardeen.
Unlike the previous generation of computers, the second generation computers employed assembly language rather than binary machine language.
Learn more about second generation computers at:
https://brainly.com/question/31492021
#SPJ1
Full Question:
Which generation was used integrated Circuit?
answer choices
First Generation
Second Generation
Third Generation
Fourth Generation
6.An organization wants to implement a remote dial-in server to ensure that personnel can connect to the organization's network from remote locations. The authentication protocol must include encryption to prevent hackers from accessing the network. Which protocol should be used
Answers
Answer:
Challenge-Handshake Authentication Protocol (CHAP).
Explanation:
In Computer technology, authentication can be defined as the process of verifying the identity of an individual or electronic device. Authentication work based on the principle (framework) of matching an incoming request from a user or electronic device to a set of uniquely defined credentials.
Basically, authentication ensures a user is truly who he or she claims to be, as well as confirm that an electronic device is valid through the process of verification.
In this scenario, an organization wants to implement a remote dial-in server to ensure that personnel can connect to the organization's network from remote locations. The authentication protocol must include encryption to prevent hackers from accessing the network.
Hence, the protocol which should be used is Challenge-Handshake Authentication Protocol (CHAP).
A Challenge-Handshake Authentication Protocol (CHAP) can be defined as a standard network access control protocol in which a client program dials in to a network access server to receive a random value and identification number that can only be used once.
Create a Python program that prints all the numbers from 0 to 4 except two distinct numbers entered by the user.
Note : Use 'continue' statement.
Answers
Here is a Python program that prints all numbers from 0 to 4, excluding two distinct numbers entered by the user, using the 'continue' statement:
```python
numbers_to_exclude = []
# Get two distinct numbers from the user
for i in range(2):
num = int(input("Enter a number to exclude: "))
numbers_to_exclude.append(num)
# Print numbers from 0 to 4, excluding the user-entered numbers
for i in range(5):
if i in numbers_to_exclude:
continue
print(i)
```
The program first initializes an empty list called `numbers_to_exclude` to store the two distinct numbers entered by the user.
Next, a loop is used to prompt the user to enter two distinct numbers. These numbers are appended to the `numbers_to_exclude` list.
Then, another loop is used to iterate through the numbers from 0 to 4. Inside the loop, an 'if' condition is used to check if the current number is in the `numbers_to_exclude` list. If it is, the 'continue' statement is executed, which skips the current iteration and proceeds to the next iteration of the loop.
If the current number is not in the `numbers_to_exclude` list, the 'print' statement is executed, and the number is printed.
This program ensures that the two distinct numbers entered by the user are excluded from the output, while all other numbers from 0 to 4 are printed.
For more such answers on Python
https://brainly.com/question/26497128
#SPJ8
Why am I constantly getting bombarded with brainly plus ads and how to fix this without paying for it?
(I do not mean faking paying for it I do NOT want to do that.)(Also answer in comments It will really help thx)
Answers
Answer:
there really is no way to fix it. I've tried everything everybody says sorry
Answer:
oop
Explanation:
Let's play Silly Sentences!
Enter a name: Grace
Enter an adjective: stinky
Enter an adjective: blue
Enter an adverb: quietly
Enter a food: soup
Enter another food: bananas
Enter a noun: button
Enter a place: Paris
Enter a verb: jump
Grace was planning a dream vacation to Paris.
Grace was especially looking forward to trying the local
cuisine, including stinky soup and bananas.
Grace will have to practice the language quietly to
make it easier to jump with people.
Grace has a long list of sights to see, including the
button museum and the blue park.
Answers
Answer:
Grace sat quietly in a stinky stadium with her blue jacket
Grace jumped on a plane to Paris.
Grace ate bananas, apples, and guavas quietly while she listened to the news.
Grace is the name of a major character in my favorite novel
Grace was looking so beautiful as she walked to the podium majestically.
Grace looked on angrily at the blue-faced policeman who blocked her way.
A photographer stores digital photographs on her computer. In this case the photographs are considered the data. Each photograph also includes multiple pieces of metadata including:
Date: The date the photograph was taken
Time: The time the photograph was taken
Location: The location where the photograph was taken
Device: Which camera the photo was taken with
Which of the following could the photographer NOT do based on this metadata?
Answers
Answer:D
Explanation:
Answer:
C filter photos to those taken of buildings
Explanation:
she wouldn't be able to tell which pictures are of buildings using that metadata.
Identify the operational level of the Purdue model in which the production management, individual plant monitoring, and control functions are defined.
Layer 1
Layer 2
Layer 3
Layer 4
Answers
The operational level of the Purdue model in which production management, individual plant monitoring, and control functions are defined is: Level 3: Manufacturing Operations Systems Zone" (Option C).
What is the Purdue Model?Purdue Enterprise Reference Architectural is an enterprise architecture reference model established in the 1990s by Theodore J. Williams and participants of the Industry-Purdue University Consortium for Computer-Aided Manufacturing.
The Purdue model, which is part of the Purdue Enterprise Reference Architecture (PERA), was created as a reference model for data flows in computer-integrated manufacturing (CIM), which automates all of a plant's activities.
Learn more about the Purdue model:
https://brainly.com/question/4290673
#SPJ1
The form used by employers to determine how much of your paycheck to withhold is a
Answers
Answer:
w2 / w4b
Explanation:
both are used to withhold federal and state income and social security taxes from an employee's paycheck. An independent contractor uses a 1099 which withholds nothing leaving that responsibility solely to the employee.
Answer:
W-4 Form
Explanation:
I guess and it was right lol
The diagram shows the positions of the Sun, Earth, and Moon during each moon phase. When viewed from Earth, at what point does the Moon appear darkest?

Answers
Answer:
B
Explanation:
when it is on the same side of Earth as the Sun because it appears all black because of the shadow
String[][] arr = {{"Hello,", "Hi,", "Hey,"}, {"it's", "it is", "it really is"}, {"nice", "great", "a pleasure"},
{"to", "to get to", "to finally"}, {"meet", "see", "catch up with"},
{"you", "you again", "you all"}};
for (int j = 0; j < arr.length; j++) {
for (int k = 0; k < arr[0].length; k++) {
if (k == 1) { System.out.print(arr[j][k] + " ");
}
}
}
What, if anything, is printed when the code segment is executed?
Answers
Answer:
Explanation:
The code that will be printed would be the following...
Hi, it is great to get to see you again
This is mainly due to the argument (k==1), this argument is basically stating that it will run the code to print out the value of second element in each array within the arr array. Therefore, it printed out the second element within each sub array to get the above sentence.
When the code segment is executed, the output is "Hi, it is great to get to see you again "
In the code segment, we have the following loop statements
for (int j = 0; j < arr.length; j++) {for (int k = 0; k < arr[0].length; k++) {The first loop iterates through all elements in the array
The second loop also iterates through all the elements of the array.
However, the if statement ensures that only the elements in index 1 are printed, followed by a space
The elements at index 1 are:
"Hi," "it" "is" "great" "to" "get" "to" "see" "you" "again"
Hence, the output of the code segments is "Hi, it is great to get to see you again "
Read more about loops and conditional statements at:
https://brainly.com/question/26098908
Comprehension s best described as the ability to
Answers
Answer:
The ability to understand
Explanation:
Answer:
recognize reading strategies.
Explanation:
Which three statements about RSTP edge ports are true? (Choose three.) Group of answer choices If an edge port receives a BPDU, it becomes a normal spanning-tree port. Edge ports never generate topology change notifications (TCNs) when the port transitions to a disabled or enabled status. Edge ports can have another switch connected to them as long as the link is operating in full duplex. Edge ports immediately transition to learning mode and then forwarding mode when enabled. Edge ports function similarly to UplinkFast ports. Edge ports should never connect to another switch.
Answers
Answer:
Edge ports should never connect to another switch. If an edge port receives a BPDU, it becomes a normal spanning-tree port. Edge ports never generate topology change notifications (TCNs) when the port transitions to a disabled or enabled status.Why is it good for companies like Google to test for possible collisions and related cyber attacks?
Answers
Answer:
Technology companies, like Google, constantly need to carry out tests and evaluations of their products that allow them to corroborate the security of their products, to avoid possible collisions or hacker attacks. This is so because when dealing with computer products, which in many cases store enormous amounts of information from their clients or users, they must guarantee their security to generate the trust of their clients, which in the end will end up being what maximizes their sales and earnings.
In other words, they must guarantee the safety of the user when using their products, which is precisely the reason why the customer purchases the company's product.
Good companies like IT companies that need to carry out the tests to verify their integrity and authenticity. This allows them to collaborate and secure their user and provide possible solutions to their problems.
Encryption is one of the easiest and simplest methods of data protection from the collision of cyber attacks. These can be avoided if cyber security is enhanced by the use of tools and techniques so that threats don't collide.Learn more about the companies like to test for possible.
brainly.com/question/13967762.