what is the purpose of a test program? group of answer choices the test program confirms that the java compiler is correct. the test program checks the syntax of each object's methods. the test program enforces that the types between arguments match correctly. the test program verifies that methods have been implemented correctly.
Answers
The purpose of a test program is it verifies that methods have been implemented correctly.
What is testing?Making unbiased assessments of how well a system (device) satisfies, surpasses, or fails to satisfy stated objectives is the process of testing.Both the agency and the integrator/supplier can benefit from a good testing program; it typically marks the conclusion of the project's "development" phase, specifies the standards for project approval, and marks the beginning of the warranty period.Verifying procurement standards and minimizing risk are the two main goals of testing. The purpose of testing is to confirm that the product (or system) complies with the functional, performance, design, and implementation requirements outlined in the procurement specifications. Testing is first about confirming that what was described is what was delivered.Second, testing is about risk management for the vendor, developer, and integrator of the system as well as the acquiring agency. The testing program is used to determine whether the work has been "finished" in order to conclude the contract, pay the vendor, and move the system into the project's warranty and maintenance phase.Hence, The purpose of a test program is it verifies that methods have been implemented correctly.
To learn more about test program refer to:
https://brainly.com/question/3405319
#SPJ4
Related Questions
what lkm rootkit method remaps system utility calls? remote execution execute redirection real-time process hiding promiscuous mode hiding
Answers
The method used by lkm rootkit to remap system utility calls is known as the "execute redirection."
LKM rootkits are some of the most difficult to detect rootkits, as they are inserted into the kernel of the operating system. This makes it extremely difficult to detect them with traditional anti-malware tools. The execute redirection method is a technique used by lkm rootkits to avoid detection.
This method redirects system utility calls to another location that has been compromised by the attacker. This allows them to execute their own code, which can be used to gain access to the system or to steal sensitive information.The execute redirection method is just one of the many methods used by lkm rootkits to avoid detection. Other methods include real-time process hiding, remote execution, and promiscuous mode hiding. Overall, these methods make it extremely difficult to detect and remove these rootkits from an infected system.
Learn more about system: https://brainly.com/question/1763761
#SPJ11
Choose the correct answer
1. Which of the variable names given below, is invalid?
O Goodluck
O
d2420
O input
O Abcd
Answers
not valid bro so u check again
what is the correct hierarchy of elements for a database schema (overall design / organization) ?
Answers
The correct hierarchy for a database schema is: Database -> Tables -> Fields (Columns) -> Records (Rows) -> Constraints.
The correct hierarchy of elements for a database schema is as follows:
1. Database: The top-level container that holds all the other elements.
2. Tables: Consist of rows and columns that store data.
3. Fields (Columns): Individual pieces of data that represent specific attributes within a table.
4. Records (Rows): A complete set of related data containing values for each field in a table.
5. Constraints: Rules applied to fields or tables to ensure data consistency and integrity.
These elements work together to create a structured and organized database schema, allowing for efficient storage and retrieval of information.
Learn more about Database here;
https://brainly.com/question/30634903
#SPJ11
When you insert a Quick table, you cannot format it true or false
Answers
Answer:
True
Explanation:
Format the table the way you want — e.g. borders, shading, row height, alignment, emphasis, font size, etc. for the heading row and the table rows. You can use manual formatting, or one of the built-in table designs
you are designing a wireless network for a client. your client would like to implement the highest speed possible. which 802.11 standard will work best in this situation? answer 802.11g 802.11b 802.11a 802.11n 802.11ac
Answers
802.11 standard that will work best in this situation is 802.11n. Wi-Fi became much quicker and more dependable with the adoption of the 802.11n standard.
Wi-Fi became much quicker and more dependable with the adoption of the 802.11n standard. It could theoretically transfer data at a speed of 300 Mbps (and could reach up to 450 Mbps when using three antennae).
You should always try to use channel 1, 6, or 11 on a non-MIMO system (802.11 a, b, or g). Stick to channels 1, 6, and 11 while using 802.11n with 20MHz channels; if you want to utilize 40MHz channels, be aware that the airwaves may be crowded, unless you reside in a detached house in a remote location.
Wi-Fi is frequently advertised at "theoretical" rates; according to this standard, 802.11ac can do 1300 Mbps, which is the equivalent of 162.5 MB/s (MBps).
To know more about 802.11n click here:
https://brainly.com/question/27990771
#SPJ4
You want to create a set of instructions to teach your dog to walk, to bark on command, and to heal. Such software would similar to _____ software
Answers
Answer:
Programme software
Explanation:
Because you have program the computer to do such activities
A brick has a weight of 23N. The brick is flat and smooth on the side in contact with the floor having measurements ( height= 5cm, length =20cm, width=10cm).
A)Calculate the area of the brick in contact with the floor. Give your answer in cm2.
B)Calculate the pressure of the brick on the floor.
Answers
Answer:
A)Area = 200\(cm^{2}\)
B) Pressure = 0.115 N/\(cm^{2}\)
Explanation:
Assuming that the brick is flat on the floor with its largest face towards the floor and not on its side, then we can calculate the area of that face by multiplying the length by the width like so...
Area = length * width
Area = 20cm * 10cm
Area = 200\(cm^{2}\)
The formula for calculating pressure is force divided by area. Therefore, since we just finished calculating the area and the force is given to us in the question (23N) we can simply plug in these values and solve for the pressure.
Pressure = Force / Area
Pressure = 23N / 200\(cm^{2}\)
Pressure = 0.115 N/\(cm^{2}\)
it is important to project an organization’s growth rate when designing information systems. T/F?
Answers
True. When designing information systems, it is important to project an organization's growth rate.
The information systems should be able to support the organization's current needs, but also be flexible enough to adapt to future growth. By projecting growth rates, the organization can plan for future expansion and ensure that the information systems in place can accommodate the additional needs.
An organization's growth rate refers to the rate at which it is expected to grow in the future. This growth can be measured in terms of revenue, employees, customers, and other metrics depending on the industry. When designing information systems, it is important to project this growth rate because information systems should not only support the current needs of the organization but also be able to adapt to future growth.
To know more about information visit:
https://brainly.com/question/32167362
#SPJ11
give several examples where you need to use clustering instead of classification in business. what do you think the issues are in clustering algorithms? e.g., are they difficult to validate?
Answers
Classification techniques include support vector machines, naive bayes classifiers, and logistic regression. The k-means clustering algorithm, the Gaussian (EM) clustering algorithm, and others are instances of clustering.
Two methods of pattern recognition used in machine learning are classification and clustering. Although there are some parallels between the two processes, clustering discovers similarities between things and groups them according to those features that set them apart from other groups of objects, whereas classification employs predetermined classes to which objects are assigned. "Clusters" are the name for these collections.
Clustering is framed in unsupervised learning in the context of machine learning, a branch of artificial intelligence. For this kind of algorithm, we only have one set of unlabeled input data, about which we must acquire knowledge without knowing what the outcome will be.
Know more about machine learning here:
https://brainly.com/question/16042499
#SPJ4
Jose is preparing a digital slide show for his informative speech. According to your textbook, which type of special effect is the best choice?
- images that fade away after being visible for a few moments
- images that shrink or become larger, depending on their importance
- Jose should avoid using special effects
- images that fly in consistently from the right
Answers
According to the textbook, the best choice for special effects in Jose's digital slide show for his informative speech would be images that fade away after being visible for a few moments.
Fading away images are a subtle and non-distracting special effect that can help maintain the focus on the content of the speech. The gradual disappearance of images after a few moments allows the audience to concentrate on the information being presented without being visually overwhelmed.On the other hand, effects such as images shrinking or becoming larger depending on their importance or flying in consistently from the right may be more suitable for presentations with a creative or visual emphasis. For an informative speech, it is generally recommended to prioritize clarity and minimize unnecessary distractions, hence selecting a simple and understated effect like fading away is a suitable choice.
To learn more about informative click on the link below:
brainly.com/question/17161344
#SPJ11
A 3-ary tree is a tree in which every internal node has exactly 3 children. How many leaf nodes are there in a 3 -ary tree with 6 internal nodes? Pick ONE optionO 10O 23O 17O 13
Answers
Nodes are the points at the endpoints of branches that, at various moments in evolutionary history, represent potential or actual sequences.
What is Internal node?Drag the name of each type of node to give the various nodes labels in the interactive graphic below. Internal nodes, which appear where two or more branches converge, stand in for the (often assumed) ancestral sequences.
For instance, the internal node denoted by the blue arrow represents the alleged common ancestor of sequences A and B.
The root, which represents the most recent common ancestor of all sequences in the phylogeny, is a crucial internal node. A useful tool for web developers is node.js. It has emerged as a top contender when people are considering tools to employ in web development due to its high level of concurrency.
Therefore, Nodes are the points at the endpoints of branches that, at various moments in evolutionary history, represent potential or actual sequences.
To learn more about node, refer to the link:
https://brainly.com/question/28485562
#SPJ1
In Pseudo code:
A text file holding financial information contains lines with the following structure:
o ID (5 characters)
o Rate (2 digits)
o Taxes (2 digits)
o Each item is separated by a colon":"
Let the user enter an ID to search for and output the rate of the ID, if not found output a message
Answers
Answer:
Explanation:
import java.io.BufferedReader;
import java.io.FileReader;
import java.io.IOException;
import java.util.Scanner;
public class FinancialInfoSearch {
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
System.out.print("Enter ID to search: ");
String searchID = scanner.nextLine();
scanner.close();
try (BufferedReader br = new BufferedReader(new FileReader("financial_info.txt"))) {
String line;
while ((line = br.readLine()) != null) {
String[] data = line.split(":");
if (data[0].equals(searchID)) {
System.out.println("Rate for " + searchID + ": " + data[1]);
return;
}
}
System.out.println("ID not found.");
} catch (IOException e) {
System.err.println("Error reading file: " + e.getMessage());
}
}
}
In this code, the user is prompted to enter the ID to search for. The BufferedReader class is used to read the lines of the file. For each line, the split method is used to split the line into an array of strings using the colon character as a delimiter. The first element of the array is compared to the search ID, and if they match, the rate is outputted. If the end of the file is reached and no match is found, a message is outputted saying that the ID was not found.
thank you
what is workplace procedure?
Answers
Answer:
MY ANSWER
Explanation:
Workplace procedures explain specific action plans for employees when carrying out a policy. Workplace procedures are important because they tell your employees how to deal with a situation and when.14 Mar 2021
Answer:
ksksozozozosmsmsmssoqoqaokanzxbbxjdjsoaoalassbsbsjjajajakakakakanananannan
Which of the following is NOT a method for companies to inform consumers that a product has been recalled?
make a public service announcement on radio
agree for a spokesperson to be interviewed about the recall
provide information on the packaging of the product
provide information on the company website
Answers
Answer: provide information on the packaging of the product
Explanation:
Product recalls usually happens in case of a fault or quality issue that is identified once the product has been delivered to the customer or is in transit. In these cases the company either reach out to the customers to get the product back or recall the products back midway.
This is done through various methods like announcemnts on radio, notification on the website or through some interview with a spokesperson.
As explained above the quality issues are identified later on post the product dispatch and hence no information is listed on the product itself. Also, recalls happen to rectify the mistakes and hence this is not a part of product inforamtion which is listed on the product.
you need to connect a router to a subnet. the subnet uses the ip address 192.168.12.0/26. you are instructed to assign the last ip address on the subnet to the router. which ip address will you use?
Answers
The IP address 192.168.12.62 can be used as per the given scenario.
What is IP address?IP stands for "Internet Protocol," which is a set of rules that governs the format of data sent over the internet or a local network.
In essence, IP addresses are the identifiers that allow information to be sent between devices on a network: they contain location information and make devices available for communication.
The broadcast address is the last IP address in a subnet. You can calculate it by taking the network address (the first address in the subnet), adding the number of addresses in the subnet, and then subtracting one.
Thus, as per the above method, the IP address that can be used is 192.168.12.62.
For more details regarding IP address, visit:
https://brainly.com/question/16011753
#SPJ1
Make a list of symptoms of computer virus and preventive measures from computer virus.
Answers
Answer:
Intrusive pop-ups. Slow performance. Frequent crashes. Unknown login items. Storage space shortage. Missing files.
Explanation:
those are symptoms
i’m failing this class and i’m stuck on this one, this is the code from the last lesson:
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a":4, "b":3, "c":2, "d":1, "f":0}
if weighted == 1 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade])
else:
return"Invalid"
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes, 0 = no) "))))
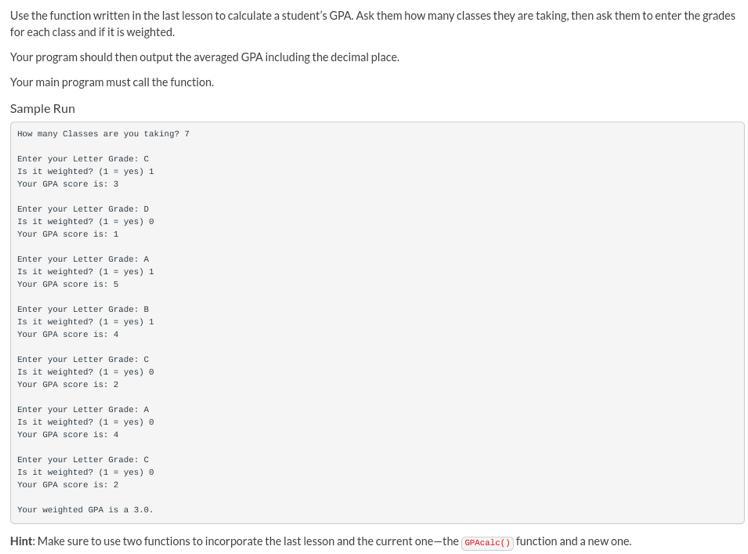
Answers
lst=([])
def avgGPA(lst1):
total = 0
count = 0
for x in lst:
if type(x) == int:
total += x
count += 1
return total/count
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a": 4, "b": 3, "c": 2, "d": 1, "f": 0}
if weighted == 1 and grade in dictionary:
lst.append(dictionary[grade]+1)
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
lst.append(dictionary[grade])
return "Your GPA score is: " + str(dictionary[grade])
else:
lst.append("Invalid")
return "Invalid"
classes = int(input("How many Classes are you taking? "))
i = 0
while i < classes:
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes) "))))
i += 1
print("Your weighted GPA is a "+str(avgGPA(lst)))
If you need me to change any code, I'll do my best. I hope this helps!
If you were referencing an e-book what would be the proper citation format?.
Answers
Answer:
Use the standard in-text citation format of author's surname and year of publication to cite an ebook in your work. Include the author's last name and first initial, the year of publication, the italics title of the book, as well as the retrieval information or DOI number in an APA reference list entry.
Hope this helped you! I would appreciate a Brainliest if you wouldn't mind.
algorithm and flowchart to find the perimeter and area of square
Answers
Answer:
I can give you the perimeter "algorithm" but not the flowchart.
Here you go:
p = w * 4
p = perimiter,
w = width/height
4 = the amount of sides needed.
perimeter = width * 4
to include both width and height, we would instead use:
perimeter = 2(width+height)
This also works with rectangles ^
--------------------------------------------------------------------------
To find an area, it is just width * height. This is also compatible with rectangles.
What is missing in the following program in order to have the output shown? numA = 24 while numA 3: numA = numA - 7 print(numA) OUTPUT: 3
Answers
Answer:
i got >
Explanation:
24 is > 3
Answer:
me too >
Explanation:
24 is greater than 3
I paid for brainly and now it's saying I have to watch ads to get answers? It still says I have my subscription but I don't understand, what am I paying for?
Answers
Answer:
Maybe you are not signed in? I think if you are not signed in then you have to watch videos to get the answer.
What classes should I take in high-school for majoring in computer science?
Answers
Answer:
Computer science are the disciplines that study information, computing and the applications or ecosystems where they are developed. It is a science that comes from applied mathematics and has 3 branches that are quite well known. On the one hand we have software engineering, secondly theory as such (primary study of algorithms and data, etc.) and finally the application of the amalgam of the first two, which end up resulting in disciplines such as big data, cybersecurity or computer security, machine learning, artificial intelligence, etc. However, we are talking about a very broad science with various branches of work. Technological advances that have improved the scope of education, now allow us to develop in specific skills and computer science is one of the macro careers that have benefited the most thanks to the diversity of subjects it encompasses. This is where the on-demand courses available on the edX platform come in. Computer scientists are in one of the best times for their career advancement. We invite you to be part of the technological development and information and computing technologies through online courses.
Explanation:
Select the correct answer.
Which of these are symbols that people use globally (In any part of the world)?
A general symbols
B. all-purpose symbols
C universal symbols
D. common symbols
Answers
Answer:
C. Universal
Explanation:
Which of the following courses would an aspiring film composer most likely take?
A. theories in classical composition
B. John Williams and the movies
C. music of the Renaissance
D. the art of film production
Answers
Answer:
The art and film of production
Explanation:
just took the test on edge
Answer:
B: John Williams and the movies
Explanation:
edg2021
John Williams is a famous composer that composed famous music for movies, such as the Star Wars movies. He is directly correlated with composing and how aspiring composers should act.
Write a function, capitalise, which takes a null-terminated string (char*), and replaces each lower-case letter with its upper-case counterpart.
Answers
// convert a string to uppercase letters void convert(char strng[])
{
int i = 0;
while (strng[1] ! = '\0')
{
strng[i] = ToUpper(strag[i]);
1++;
}
return;
}
char ToUpper (char letter) // convert a character to uppercase
{
if( (letter >='a') & (letter <= '2') )
return (letter - 'a' + 'A');
else
return (letter);
}
Learn more about String here:
https://brainly.com/question/15683939
#SPJ4
When a signal travels, this is called ________. group of answer choices transit end-to-end transmission propagation transport
Answers
When a signal travels, this is called propagation.
Propagation refers to the transmission or spread of a signal through a medium, such as air, water, or a physical medium like a wire or fiber optic cable. It involves the movement of the signal from its source to its destination. During propagation, the signal undergoes various transformations, such as attenuation (weakening), distortion, and delay, depending on the characteristics of the medium and any intervening obstacles or interference. Propagation is a fundamental concept in telecommunications and networking, encompassing the physical transmission of signals across different mediums, including wired and wireless communications. It plays a crucial role in determining the quality, reach, and reliability of communication systems.
Know more about propagation here:
https://brainly.com/question/13266121
#SPJ11
True or false? threat modeling is the practice of identifying and prioritizing potential threats and security mitigations to protect
something of value, such as confidential data or intellectual property.
a true
b false
will give brainlyest
Answers
Threat modeling is the practice of identifying and prioritizing potential threats and security mitigations to protect something of value, such as confidential data or intellectual property,
This statement is True.
Threat modeling is a structured process of analyzing the security of a system or application to identify potential threats and vulnerabilities. The goal of threat modeling is to proactively identify and mitigate potential security risks, in order to better protect valuable assets, such as confidential data or intellectual property.
The process of threat modeling typically involves several steps, including:
Defining the scope of the system or application: This involves identifying the boundaries of the system, what assets it is designed to protect, and what the potential threat sources are.Identifying assets: This involves identifying the valuable data or assets that the system is designed to protect, and understanding their importance to the organization.Identifying potential threats: This involves considering the various types of attacks that could be launched against the system, as well as the motivations behind such attacks.Learn more about threat modeling:
brainly.com/question/29803930
#SPJ4
In the Business world people are often measured by their???
A- soft skills
B- hobbies
C- iq
D- technical skills
Answers
Answer:
D
Explanation:
You need skills to succeed!!
Create code in HTML of a webpage that has an image that opens a page with the Wikipedia website when clicked. (Refer to Image)

Answers
Here is the Code.
you may need to change it a bit
Hopefully it Help you out :-)

Yael would like to pursue a career where she helps design office spaces that are comfortable and help workers avoid injuries. What should she study? plsss help me with this question.
A. ergonomics
B. semantics
C. botany
D. genomics
Answers
The option that that Yael should study is A. Ergonomics.
What is the study about?Ergonomics is the scientific study of designing products, systems, and environments to optimize human comfort and health, including the design of office spaces.
Therefore, Yael could study ergonomics to gain the skills and knowledge necessary to design office spaces that are safe, efficient, and comfortable for workers. An ergonomist might work with architects, interior designers, and other professionals to ensure that the design of an office space takes into account the needs of the workers who will be using it.
Learn more about injuries from
https://brainly.com/question/19573072
#SPJ1