When one SQL query is embedded in another SQL query, the first SQL query can still contain an SQL ________ clause
Answers
When one SQL query is embedded in another SQL query, the first SQL query can still contain an SQL WHERE clause.
When embedding one SQL query inside another SQL query, it's known as a subquery. The subquery can appear in different parts of the main query, such as the SELECT clause, FROM clause, or WHERE clause. The WHERE clause is used to filter rows based on a specific condition. In the case of a subquery, the WHERE clause in the outer query can be used to filter the results returned by the subquery. This is useful when the subquery returns a large number of rows, and you want to filter them down to a smaller set of rows that meet a specific condition. Overall, the WHERE clause is a crucial part of SQL that helps to refine and narrow down query results.
learn more about SQL here:
https://brainly.com/question/13068613
#SPJ11
Related Questions
What is keyboard,how many keys are there?
Answers
Answer:
A keyboard is a device used to input data into a computer or other electronic device. It typically consists of a set of keys, buttons, or characters that are used to enter data into the device. The number of keys on a keyboard varies depending on the model, but most standard keyboards have around 104 keys. These include the alphanumeric keys (letters and numbers), as well as special keys such as the Shift and Control keys. There may also be additional keys such as multimedia keys, page navigation keys, and function keys.
Answer:
A keyboard is an input device that is used to enter characters and commands into a computer or other electronic device. It typically consists of a set of keys, each of which corresponds to a specific character, symbol, or function.
The standard keyboard layout for modern computers typically consists of 104 keys, although some specialized keyboards may have fewer or additional keys. These keys can be grouped into several categories:
Alphanumeric keys: These are the standard letter and number keys that make up the bulk of the keyboard.
Function keys: These are the 12 keys at the top of the keyboard (F1 through F12) that perform various system functions in different programs.
Modifier keys: These are the keys that modify the behavior of other keys, such as Shift, Ctrl, Alt, and the Windows or Command key.
Navigation keys: These are the keys used for moving the cursor or selection around the screen, such as the arrow keys, Home, End, Page Up, and Page Down.
Editing keys: These are the keys used for editing text or other content, such as Backspace, Delete, and Enter.
Numeric keypad: This is a set of 17 keys on the right side of the keyboard that can be used for numeric input or as a calculator.
Which type of mic is durable, versatile and does not rely on power?
Dynamic
B.
Decibals
C.
Ribbon
D.
Condenser
Answers
Answer:
Dynamic
Explanation:
Dynamic Mics are the workhorses of the microphone world. They're cheap, durable and sound fantastic on some of the most common sources in recording.
Hope this helps! :)
Answer:
Dynamic
Explanation:
They are cheap, versatile, durable, and doesnt rely on power
a file that serves as a starting point for a new document
Answers
Answer:
The appropriate response is "Template".
Explanation:
A template would be a document that might open new opportunities for such a new folder. Because once you launch a framework, that's already pre-formatted sometimes in a manner. This same template will indeed presumably have such identification and phone number environment throughout the upper left, a person receiving identify location somewhat below something on the opposite side, a response body location further below, as well as a signature, identify at either the lower part.you are the it administrator for a small corporate network. you have installed the windows server 2019 operating system on a server named corpserver2. during this installation, you created a single partition that took up the entire first disk. you would like to add fault tolerance to the system volume and create an additional fault tolerant volume for storing data. four additional, uninitialized hard disks have been installed in the server for this purpose. in this lab, your task is to complete the following: to add fault tolerance for the system (c:) volume, create a mirrored volume using disk 1. create a new volume that provides both fault tolerance and improved performance using the following settings: disks: disk 2, disk 3, and disk 4 volume size: 2048000 mb (2 tb) drive letter: r format: ntfs volume label: data
Answers
To add fault tolerance to the system volume (C:) and create a mirrored volume using Disk 1, follow these steps:
1. Log in to the Windows Server 2019 operating system on "corpserver2" as an administrator.
2. Press the Windows key on your keyboard, type Disk Management, and open the Disk Management application.
3. In Disk Management, you should see the list of disks installed in the server. Locate Disk 1, which will be used for creating the mirrored volume.
4. Right-click on the System (C:) volume and select Add Mirror. This will initiate the process of adding fault tolerance to the system volume.
5. In the Add Mirror dialog box, you should see a list of available disks. Select Disk 1 from the list and click Add Mirror.
6. Windows will start the process of mirroring the system volume to Disk 1. This may take some time depending on the size of the volume.
7. Once the mirroring process is complete, you will see the System (C:) volume with a mirrored icon next to it in Disk Management. The mirrored volume now provides fault tolerance for the system volume.
To create a new volume that provides both fault tolerance and improved performance using Disk 2, Disk 3, and Disk 4, follow these steps:
1. In Disk Management, locate the uninitialized disks: Disk 2, Disk 3, and Disk 4.
2. Right-click on Disk 2 and select New Mirrored Volume.
3. The New Mirrored Volume Wizard will open. Click Next to proceed.
4. In the **Select Disks** step, select both Disk 2, Disk 3, and Disk 4. Click Next.
5. Specify the volume size as 2048000 MB (2 TB). Click Next.
6. Assign the drive letter "R" to the volume. Select the file system as "NTFS" and enter the volume label as "Data". Click Next.
7. Review the settings on the **Completing the New Mirrored Volume Wizard** page. Ensure that everything is as desired and click Finish.
8. Windows will create the mirrored volume using Disk 2, Disk 3, and Disk 4. This process may take some time.
9. Once the creation process is complete, you will see the new mirrored volume labeled as "Data" with the drive letter "R" in Disk Management.
You have now added fault tolerance to the system volume (C:) by creating a mirrored volume using Disk 1. Additionally, you have created a new volume with fault tolerance and improved performance using Disk 2, Disk 3, and Disk 4, with a size of 2048000 MB (2 TB) and the drive letter "R". The volume is formatted as NTFS and labeled as "Data".
Learn more about fault tolerance:
brainly.com/question/29427474
#SPJ11
WILL GIVE BRAIINLIEST AND WATER ICE FROM RITA'S!!!!!!!!!
Checking baggage and traveling to the destination are parts to this section of the transportation system:
Answers
Answer:
When you purchase a connecting flight, checked baggage is usually forwarded to your final destination, and will change planes when you do. ... In some cases if you purchased multiple tickets that are not all on the same carrier you may need to recheck your baggage
Explanation:
What is the biggest difference between Blender, Autodesk Maya, and 3DS Max? (1 point)
Answers
Answer: Maya and Max are the products of AutoDesk, while Blender is a product of the Blender Foundation.
Explanation: The most basic difference between Maya, Max, and Blender is that Maya and Max are the products of AutoDesk, while Blender is a product of the Blender Foundation. Maya was originally a 3D animation and texturing software, and the modeling feature was later added to it.
which function can be used to easily return the fifth biggest number from a set of eighty numbers?
Answers
To get the nth largest value in a set of data, you can use the LARGE function in excel.
Simply provide a range and a rank number to activate the totally automatic LARGE function. "Array" and "k" are the formal names for these arguments. To get the fifth largest large, we can utilize LARGE. taken down from the formula in F5. The array's value is the mixed reference cells. Rows are not locked, however notice that the columns are. This enables for the updating of the rows as the formula is transferred down but inhibits the updating of the columns as the formula is copied across. Another mixed reference is used in the k (n) value that is presented. The row is locked in this instance to prevent alteration when the formula is copied down.
Learn more about Large Function in Excel here:
https://brainly.com/question/14915166
#SPJ4
Three actions you can perform on a touch screen,that you cannot perform with a traditional pointing device such as a mouse
Answers
Answer:
Pinch and Zoom: One of the most common actions performed on touchscreens is pinch and zoom. With a traditional pointing device such as a mouse, you cannot perform this action. With a touchscreen, users can use two fingers to zoom in and out on text, images, and other content on the screen.
Swipe: Another action that is unique to touchscreens is swipe. With a traditional pointing device, you cannot swipe across the screen to navigate between pages or screens. With a touchscreen, users can swipe left or right to move between screens or pages, and up or down to scroll through content.
Multi-touch gestures: Touchscreens enable users to perform multi-touch gestures, which cannot be performed with a traditional pointing device. For example, users can use three fingers to swipe between open applications, or use two fingers to rotate an image or document. These multi-touch gestures are becoming increasingly common in modern touch screen devices.
Explanation:
4. 8. 5: Calendar code hs
Using an HTML table, make your own calendar for this month.
The table headers should have the name of each day of the week.
Inside the table, write the date of each day in the month.
For example, the calendar for the month of November 2016 would look like this:
November Calendar
BONUS CHALLENGE:
Add events to your calendar by adding lists to specific days in the table. Add friend and family birthdays, holidays, or any other events you can think of!
Answers
Answer:
Here is an HTML code you can use.
If you go to any HTML editor. You will see this clearly works. Hope this helps lad. This also includes your bonus challenge.
<!DOCTYPE html>
<html>
<head>
<title>March Calendar</title>
<style>
table {
border-collapse: collapse;
}
td, th {
border: 1px solid black;
padding: 10px;
text-align: center;
font-size: 20px;
font-weight: bold;
}
th {
background-color: #ddd;
}
td {
height: 100px;
vertical-align: top;
}
</style>
</head>
<body>
<h1>March Calendar</h1>
<table>
<thead>
<tr>
<th>Sun</th>
<th>Mon</th>
<th>Tue</th>
<th>Wed</th>
<th>Thu</th>
<th>Fri</th>
<th>Sat</th>
</tr>
</thead>
<tbody>
<tr>
<td></td>
<td></td>
<td></td>
<td></td>
<td></td>
<td>1</td>
<td>2</td>
</tr>
<tr>
<td>3</td>
<td>4</td>
<td>5</td>
<td>6</td>
<td>7</td>
<td>8</td>
<td>9</td>
</tr>
<tr>
<td>10</td>
<td>11</td>
<td>12</td>
<td>13</td>
<td>14</td>
<td>15</td>
<td>16</td>
</tr>
<tr>
<td>17</td>
<td>18</td>
<td>19</td>
<td>20</td>
<td>21</td>
<td>22</td>
<td>23</td>
</tr>
<tr>
<td>24</td>
<td>25</td>
<td>26</td>
<td>27</td>
<td>28</td>
<td>29</td>
<td>30</td>
</tr>
<tr>
<td>31</td>
<td></td>
<td></td>
<td></td>
<td></td>
<td></td>
<td></td>
</tr>
</tbody>
</table>
<h2>Events:</h2>
<ul>
<li>March 17 - St. Patrick's Day</li>
<li>March 20 - First day of Spring</li>
</ul>
</body>
</html>
The calendar for this month using HTML is mentioned below:
<!DOCTYPE html>
<html>
<head>
<title>Calendar</title>
<style>
table {
border-collapse: collapse;
width: 100%;
}
th, td {
border: 1px solid black;
text-align: center;
padding: 8px;
}
th {
background-color: #ccc;
}
</style>
</head>
<body>
<h2>Calendar</h2>
<table>
<tr>
<th>Sunday</th>
<th>Monday</th>
<th>Tuesday</th>
<th>Wednesday</th>
<th>Thursday</th>
<th>Friday</th>
<th>Saturday</th>
</tr>
<tr>
<td></td>
<td></td>
<td></td>
<td></td>
<td>1</td>
<td>2</td>
<td>3</td>
</tr>
<tr>
<td>4</td>
<td>5</td>
<td>6</td>
<td>7</td>
<td>8</td>
<td>9</td>
<td>10</td>
</tr>
<tr>
<td>11</td>
<td>12</td>
<td>13</td>
<td>14</td>
<td>15</td>
<td>16</td>
<td>17</td>
</tr>
<tr>
<td>18</td>
<td>19</td>
<td>20</td>
<td>21</td>
<td>22</td>
<td>23</td>
<td>24</td>
</tr>
<tr>
<td>25</td>
<td>26</td>
<td>27</td>
<td>28</td>
<td>29</td>
<td>30</td>
<td>31</td>
</tr>
</table>
</body>
</html>
Learn more about HTML, here:
https://brainly.com/question/24065854
#SPJ2
Adele has always worked for a public sector organization. Which job is MOST likely something Adele has performed in the past?
A.
a barista at a local Starbucks
B.
a stock trader at a major Wall Street corporation
C.
a researcher at the Center for Disease Control
D.
a mortgage analyst for Wells Fargo Bank
Answers
The most likely something Adele has performed in the past is a stock trader at a major Wall Street corporation.
What kind of business is deemed to be in the public sector?Public goods and governmental services including the military, law enforcement, infrastructure, public transit, public education, together with health care and those employed by the government itself, such as elected politicians, are all considered to be part of the public sector.In India, there are three major organisational structures employed by public sector businesses. The first is a departmental undertaking, the second is a statutory (or public) corporation, and the third is a government company.employees of public businesses, central and municipal governments, and second employment in the public sector.The public sector often comprises services like the military.
To learn more about public sector organization refer to:
https://brainly.com/question/7876494
#SPJ1
Need answer ASAP
In which phrase does software coding and testing happen in the spiral model?
The spiral model does not have a separate testing phase. Both software coding and testing occurs during the _____ phase.
Answers
both software coding and testing occurs during Engineering phase
A) Write an expression that evaluates to true if the value of the string variable s1 is greater than the value of string variable s2. Instructor Notes: Note that you will need to use the C standard library function strcmp, B) Write an expression that evaluates to true if the value of variable JestName is greater than the string Dexter. C) Assume that an int variable age has been declared and already given a value and assume that a char variable choice has been declaredas well. Assume further that the user has just been presented with the following menu: S: hangar steak, red potatoes, asparagus · T: whole trout, long rice, brussel-sprouts .B: cheddar cheeseburger, steak fries, cole slaw (Yes, this menu really IS a menu) Write some code that reads a single character (S or T or B) into choice. Then the code prints out a recommended accompanying drink as follows: If the yalue of age is 21 or lower, the recommendation is vegetable juice" for steak cranberry juice for trout, and "soda" for the burger. Otherwise, the recommendations are cabernet,chardonnay", and "IPA" for steak, trout, and burger respectively. Regardless of the value of age, your code should print 'invalid menu selection if the character read into choice was not S or T or B.
Answers
A) An expression that evaluates to true if the value of the string variable s1 is greater than the value of string variable s2 is given below:s1>s2 || strcmp(s1,s2)>0
B) An expression that evaluates to true if the value of variable JestName is greater than the string Dexter is given below:
JestName > "Dexter"C) Code that reads a single character (S or T or B) into choice. Then the code prints out a recommended accompanying drink as follows is given below:char choice;int age;scanf("%c", &choice);if(choice == 'S'){ if(age <= 21){ printf("Recommended Accompanying Drink: Vegetable Juice"); } else{ printf("Recommended Accompanying Drink: Cabernet"); } }else if(choice == 'T'){ if(age <= 21){ printf("Recommended Accompanying Drink: Cranberry Juice"); } else{ printf("Recommended Accompanying Drink: Chardonnay"); } }else if(choice == 'B'){ if(age <= 21){ printf("Recommended Accompanying Drink: Soda"); } else{ printf("Recommended Accompanying Drink: IPA"); } }else{ printf("Invalid menu selection.");}Note: Here, in the code, age is already declared and initialized with an integer value and choice is a character variable. scanf function is used to read a single character. Then the nested if-else statements are used to determine the value of the choice variable and if it matches with the given conditions, then it will print the Recommended Accompanying Drink for the respective menu selection. Otherwise, it will print the statement "Invalid menu selection."
Know more about string here:
https://brainly.com/question/30779781
#SPJ11
An anchor tag can be coded using which two attributes? href and name src and id href and src name and src
Answers
An anchor tag can be coded using the two attributes such as A: href and name.
Anchor tags are HTML tags used to create hyperlinks. Links and hyperlinks form the basis of web navigation, what you click to move from one page to another on a website. The anchor tag is encoded using two attributes named href and name. For example: <a href="URL name"> AnchorName </a>.
In this, the 'href' attribute indicates the hyperlink's destination, and AnchorName is the name given to the anchor which is shown as the name of the hyperlink.
You can learn more about anchor tag at
https://brainly.com/question/29534530
#SPJ4
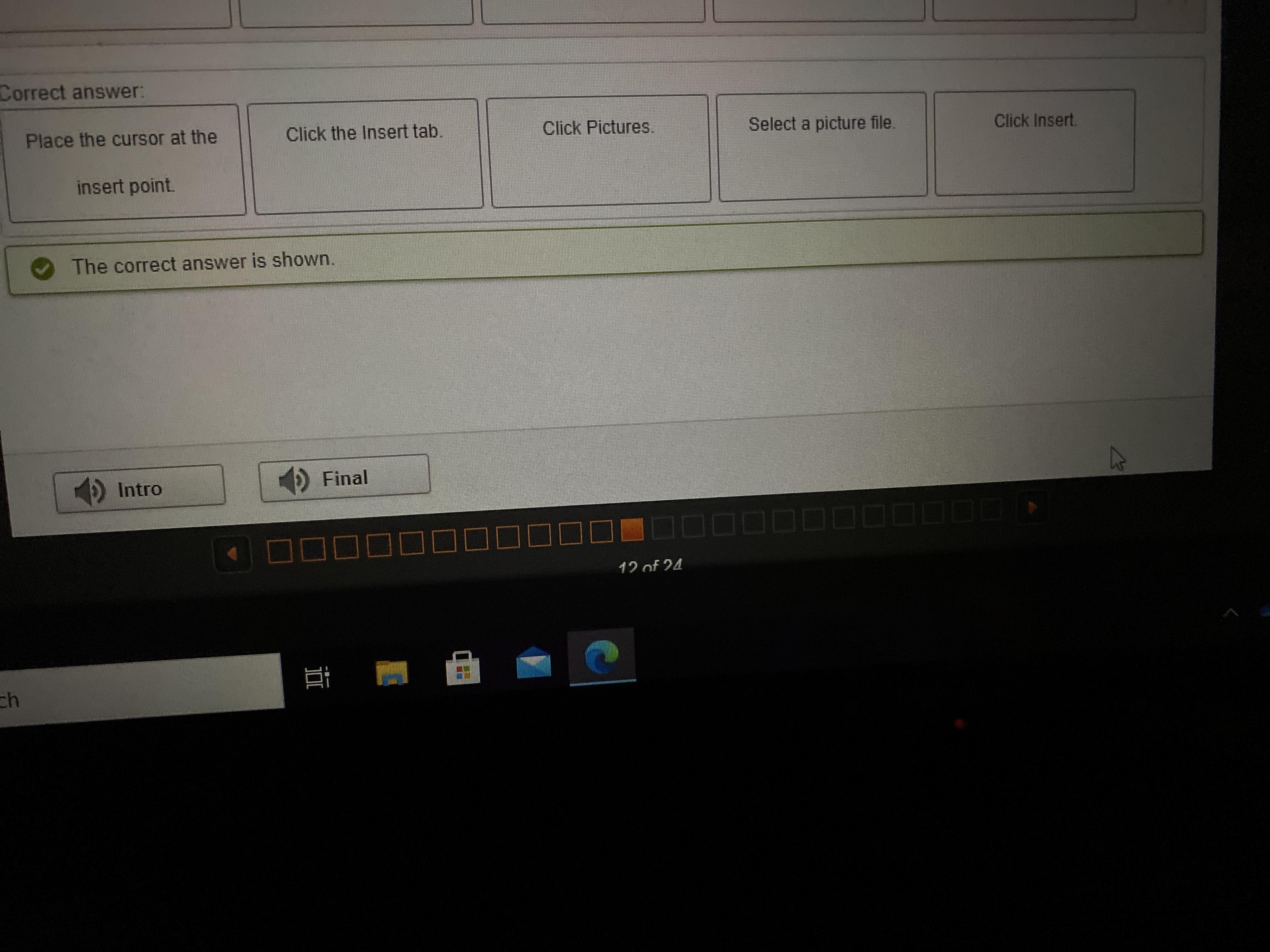
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
i u were to make 1 new animal in the world what would it be? (it can be cross breed)
Answers
Answer:
lizard bird
Explanation:
2) Prompt the user for his/her favorite 2-digit number, and the output is the square root of the number.
Answers
num = int(input("What's your favorite 2-digit number? "))
print("The square root of {} is {}".format(num, (num**0.5)))
I hope this helps!
PLEASE HURRY I WILL GIVE BRANLIEST
Which of the following statements is true concerning cloud computing?
- provides storage and processing capabilities at the user’s location
- provides storage and processing capabilities using computers that are owned and maintained by the user
-reduces the cost of storage and processing, allowing smaller businesses to be more competitive
-can only be accessed during business hours
Answers
Answer:
provides storage and processing capabilities using computers that are owned and maintained by user
The statement which is true regarding cloud computing is Provides storage and processing capabilities using computers that are owned and maintained by user .
What is cloud computing?The on-demand availability of computer system resources, in particular data storage (cloud storage) and processing power, without direct active supervision by the user, is known as cloud computing. Functions in large clouds are frequently dispersed over several sites, each of which is a data center.
Cloud computing often uses a "pay as you go" model, which can help reduce capital expenses but may also result in unanticipated running expenses for users.
Cloud computing depends on resource sharing to accomplish coherence. The on-demand, pay-as-you-go delivery of IT resources over the Internet is known as cloud computing.
Therefore, The statement which is true regarding cloud computing is Provides storage and processing capabilities using computers that are owned and maintained by user .
To learn more about cloud computing, refer to the link:
https://brainly.com/question/11973901
#SPJ2
consider a codebase that includes a significant number of string constants, such as those used in flutter text widgets. such an application is not immediately adhering to principles of... group of answer choices adaptivity accessibility internationalization responsiveness
Answers
internationalisation . The application does not instantly follow the internationalisation tenets. Internationalization is the process of creating software that can be readily translated into other languages and cultural contexts.
The internationalisation principles are not immediately followed by the application. The process of internationalising software entails making it easily adaptable to many linguistic and cultural settings. The programme may be difficult to translate to different languages or locations if it uses a large number of string constants since these constants may be hardcoded in the source. Developers should avoid hardcoding strings in the codebase and instead employ localization strategies, such as putting them in resource files, to accomplish internationalisation. This makes it simple to translate the application into other languages and cultural contexts.
learn more about application here:
https://brainly.com/question/31164894
#SPJ4
printer is hardware or software
Answers
Answer:
the printer is hardware
NEED HELP LIKE RIGHT NOW PLS
John has two ATM transactions but only one of them has a fee (Interac). Why?
A. Interac is an out-of-network ATM and First Bank charges customers if they use out-of-network ATMs.
B.First Bank charges customers for using their ATMs.
C.Banks charge fees if you take out less than $100 at an ATM machine.
D.The first ATM transaction is free but all additional ATM transactions have a fee.
Answers
Answer:
c answer
Explanation:
Which of the below would provide information using data-collection technology?
Buying a new shirt on an e-commerce site
Visiting a local art museum
Attending your friend's baseball game
Taking photos for the school's yearbook
Answers
The following statement would provide the information by utilising data-collection technology: Buying a new shirt on an e-commerce site.
What is data collection?
The process of obtaining and analysing data on certain variables in an established system is known as data collection or data gathering. This procedure allows one to analyse outcomes and provide answers to pertinent queries. In all academic disciplines, including the physical and social sciences, the humanities, and business, data collecting is a necessary component of research. Although techniques differ depending on the profession, the importance of ensuring accurate and truthful collection does not change. All data gathering efforts should aim to gather high-caliber information that will enable analysis to result in the creation of arguments that are believable and convincing in response to the issues that have been addressed. When conducting a census, data collection and validation takes four processes, while sampling requires seven steps.
To learn more about data collection
https://brainly.com/question/25836560
#SPJ13
Why would someone get a patent for their invention?
1. to sell their idea
2. to make their idea public domain
3. to be able to name the invention after themselves
4. to keep others from reproducing their idea
Answers
Answer:
4.To keep other from reproducing their idea .
Explanation:
It is regard as an exclusive right own on a invention .The inventor must disclosed the technical information about the product to the public before a patent is granted .
It is the legal authorization given to an inventor for sharing his intellectual property to the public this also restrict others from making ,using or selling the invention for a limited .
there are 3 type of patents ,Utility patents design patents and plant patent.
1. What is an AUP? (1 point)
O the abbreviation for the school administrator in an online education environment
a document outlining what is acceptable behavior when using the Internet for schoolwork
a policy outlining the proper formatting to use in Microsoft Office documents for online education
O a short course students can take to understand the school's policies better
Answers
The term AUP is option B: a document outlining what is acceptable behavior when using the Internet for school work.
What is an AUP?An Acceptable Use Policy (AUP) is a set of rules and guidelines that outline the appropriate and responsible use of a school's computer equipment, networks, and other digital resources. It is designed to protect the school's technology infrastructure, as well as the privacy and security of students, teachers, and other users.
An AUP may include guidelines for a variety of activities, such as:
Accessing and using the school's computer networks and equipmentUsing the Internet for schoolwork, research, and communicationProtecting personal privacy and security onlineUsing social media and other online communication toolsDownloading and installing software and appsTherefore, based on the context of the above, i can say that an AUP may also specify the consequences for violating the terms of use, which can include disciplinary action, revocation of access to digital resources, and other penalties.
Learn more about Acceptable Use Policy from
https://brainly.com/question/24951641
#SPJ1
MS Word
6.What adds artistic effects to the picture to make it more look like a sketch or painting.?
7. It improves the brightness, contrast or sharpness of the picture.
Answers
The thing that adds artistic effects to the picture to make it more look like a sketch or painting is:
To add artistic effects to a picture to make it look like a sketch or painting, you can use photo editing software or an app that has filters or effects that mimic the look of a sketch or painting. Some popular options for this include Adobe Photoshop, GIMP, and Prisma.How do one improve brightness?To improve the brightness, contrast, or sharpness of a picture, you can also use photo editing software or an app.
These tools typically have features such as brightness/contrast adjustments, sharpening filters, and other image enhancement tools that allow you to fine-tune the appearance of your photo.
Therefore, Some popular options for this include Adobe Photoshop, GIMP, and Lightroom. You can also use these tools to adjust the color balance, saturation, and other aspects of the image to achieve the desired look.
Learn more about brightness from
https://brainly.com/question/2824108
#SPJ1
submit your 250-word essay, supported by details from atleast two sourced, that expresses wherher you belive the internet is a good or a bad influence on you people

Answers
Note that the above essay is an argumentative essay. See the example given below.
Project: Research and Write: Is the Internet a Bad Influence on Young People?
The impact of the internet on young people is a topic of ongoing debate. On one hand, the internet provides access to vast amounts of information and educational resources, as well as opportunities for social interaction and communication. On the other hand, it can also expose young people to inappropriate content, cyberbullying, and online predators.
However, it is important to note that the internet is not inherently good or bad. Rather, it is the way it is used and the choices that individuals make that determine its impact. Parents and educators have a responsibility to educate young people on how to use the internet safely and responsibly.
In conclusion, the internet can have both positive and negative effects on young people. It is up to individuals and the adults in their lives to ensure that its impact is predominantly positive. This can be achieved through education, monitoring, and setting clear boundaries for internet use.
Learn more about Argumentative Essays:
https://brainly.com/question/27807626
#SPJ1
Match the terms with their explanations.

Answers
Answer:
Zoom helps move the object of view further or closer
White Balance tells the camera what each color should look like
Shutter controls how long light enters the camera
focus provides sharper images by way of a ring at the front of the lens
Explanation:
Took photography classes
Use nested for-loops to have the turtle draw a snowflake of polygons. Use the variable turnamount to turn after each shape and the variable n for the sides of the polygon
Answers
An interlocking loop is referred to as nested loop . These are frequently utilized while working in two dimensions, such as when printing stars in rows and columns.
How do two for loops that are nested work?An inner loop encloses the body of an outer loop, creating a nested loop. In order for this to operate, the inner loop must be triggered by the outer loop's initial pass in order to begin working. The inner loop is then reactivated during the second transit of the outer loop.
The for loop may be nested, right?For loops that are nested are placed inside of one another. With each outer loop iteration, the inner loop is repeated.
To know more about nested for-loops visit :-
https://brainly.com/question/13971698
#SPJ4
what is a communication protocols
Answers
The protocol defines the rules, syntax, semantics and synchronization of communication and possible error recovery methods.
Lab 8 – MongoDB – Array and Aggregation Query
Objective
In this Lab, you learn to query a database in MongoDB to obtain
information using array.
Getting Started
Array operators: $push,$each,$slice
Answers
In this lab, we will be focusing on querying a MongoDB database using array operators. Specifically, we will explore the `$push`, `$each`, and `$slice` operators to manipulate and retrieve data from arrays within MongoDB documents.
The objective of this lab is to gain hands-on experience with array operations and aggregation queries in MongoDB.
To get started with the lab, make sure you have MongoDB installed and running on your machine. Additionally, ensure that you have a sample database with relevant collections and documents to work with.
Lab Tasks:
1. Use the `$push` operator to add an element to an existing array field in a document.
2. Use the `$each` operator to add multiple elements to an array field at once.
3. Use the `$slice` operator to retrieve a subset of elements from an array field.
4. Perform aggregation queries involving array fields, such as grouping and filtering.
Throughout the lab, make sure to document your findings, observations, and any challenges you encounter. This will help you reflect on the concepts learned and ensure a comprehensive understanding of array operations and aggregation queries in MongoDB.
Remember to refer to the MongoDB documentation and resources for further guidance on specific array operators and aggregation queries.
Good luck with your lab!
To find more about databases, click on the below link:
brainly.com/question/13262352
#SPJ11
both arrays and structures are capable of storing multiple values. what is the difference between an array and a structure?
Answers
The main distinction between an array and a structure is that an array allows us to store a group of data items, many of which are the same data type, but a structure allows us to store a variety of data types as a single unit.
Are struct and array the same thing?No, a data structure that may hold variables of many sorts is referred to as a structure. While not supporting different data types, an array is a form of data structure that is used as a container and can only hold variables of the same type.The main distinction between an array and a structure is that an array allows us to store a group of data items, many of which are the same data type, but a structure allows us to store a variety of data types as a single unit.A data structure that may hold variables of many sorts is referred to as a structure.To learn more about Array refer to:
https://brainly.com/question/26104158
#SPJ4