Why do you believe that even errors and small details were copied (e. G. , repair patch, wing hole, paint color) by the Soviets?
Answers
The Soviets copied even errors and small details such as repair patches, wing holes, and paint colors in their espionage efforts to precisely replicate advanced technology and minimize discrepancies that could lead to performance issues or detection.
During the Cold War, the Soviet Union was engaged in a technology race with the United States and other Western countries. In order to close the technological gap, they often resorted to espionage to acquire valuable information and technology. By copying even the smallest details and errors, the Soviets aimed to ensure the accuracy and effectiveness of their replicated technology.
This attention to detail also helped them avoid detection, as any differences could potentially raise suspicion among their adversaries. Furthermore, some seemingly insignificant details might have had an impact on the overall performance of the technology, so it was essential for the Soviets to replicate these elements as accurately as possible.
To know more about advanced technology visit:
https://brainly.com/question/8798227
#SPJ11
Related Questions
A threat vector is an item of code on a distributed device that reports the condition of the device to a central server.
a. true
b. false
Answers
Answer:
A threat vector is an item of code on a distributed device that reports the condition of the device to a central server.
a. true
It is true that a threat vector is an item of code on a distributed device that reports the condition of the device to a central server. The correct option is a.
What is a threat vector?The total number of attack vectors that an attacker can use to manipulate a network or computer system or extract data is referred to as the attack surface.
Threat vector and attack vector are interchangeable terms that describe the various ways a hacker can gain access to data or other confidential information.
The methods used by adversaries to breach or infiltrate your network are referred to as attack vectors.
Malware and ransomware, as well as man-in-the-middle attacks, compromised credentials, and phishing, are all examples of attack vectors.
A threat vector is a piece of code on a distributed device that reports the device's status to a central server.
Thus, the correct option is a.
For more details regarding a threat vector, visit:
https://brainly.com/question/28558110
#SPJ2
(T/F) A wide range of tech adoption and investments exist. Third-party analytics tools far outpace other tech adoptions and the Cloud is the least adopted tech.
True
False
Answers
False. A wide range of tech adoption and investments indeed exists, encompassing various technologies such as cloud computing, analytics tools, artificial intelligence, and more. However, the statement that third-party analytics tools far outpace other tech adoptions and the Cloud being the least adopted tech is not accurate.
In reality, cloud computing has become one of the most widely adopted technologies in recent years, with many businesses and organizations leveraging cloud-based solutions for storage, data processing, and software delivery. The widespread adoption of cloud technology can be attributed to its numerous advantages, including scalability, cost-efficiency, and accessibility.
On the other hand, while third-party analytics tools are popular and have seen significant growth, they may not necessarily outpace other technology adoptions. The adoption rate of a specific technology varies based on factors like industry, company size, and business requirements. It is essential to consider these factors when evaluating the adoption of various technologies.
In conclusion, while there is a wide range of tech adoption and investments, it is not accurate to claim that third-party analytics tools far outpace other tech adoptions and that the Cloud is the least adopted technology. Each technology has its unique adoption rate depending on various factors, and cloud computing is now among the most widely adopted technologies.
Learn more about adoption here:
https://brainly.com/question/18223114
#SPJ11
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future
Answers
Answer:
The organization could make it so that specific websutes that seem fake/unsafe are not accessible to the users. For example, downloading an extension into all the devices, that blocks these malicious websites (uBlock Origin)
You are working as a project manager. One of the web developers regularly creates dynamic pages with a half dozen parameters. Another developer regularly complains that this will harm the project’s search rankings. How would you handle this dispute?
Answers
From the planning stage up to the deployment of such initiatives live online, web project managers oversee their creation.They oversee teams that build websites, work with stakeholders to determine the scope of web-based projects, and produce project status report.
What techniques are used to raise search rankings?
If you follow these suggestions, your website will become more search engine optimized and will rank better in search engine results (SEO).Publish Knowledgeable, Useful Content.Update Your Content Frequently.facts about facts.possess a link-worthy website.Use alt tags.Workplace Conflict Resolution Techniques.Talk about it with the other person.Pay more attention to events and behavior than to individuals.Take note of everything.Determine the points of agreement and disagreement.Prioritize the problem areas first.Make a plan to resolve each issue.Put your plan into action and profit from your victory.Project managers are in charge of overseeing the planning, execution, monitoring, control, and closure of projects.They are accountable for the project's overall scope, team and resources, budget, and success or failure at the end of the process.Due to the agility of the Agile methodology, projects are broken into cycles or sprints.This enables development leads to design challenging launches by dividing various project life cycle stages while taking on a significant quantity of additional labor.We can use CSS to change the page's background color each time a user clicks a button.Using JavaScript, we can ask the user for their name, and the website will then dynamically display it.A dynamic list page: This page functions as a menu from which users can access the product pages and presents a list of all your products.It appears as "Collection Name" in your website's Pages section.To learn more about search rankings. refer
https://brainly.com/question/14024902
#SPJ1
Which of the following best describes the average amount of stored data per user for the first eight years of the application existence
Answers
The option that best describes the average amount of stored data per user for the first eight years of the application existence is memory.
What is RAM memory?The memory of a system is known to bee RAM which is Random Access Memory.
Conclusively, This is known to be a part of system hardware where operating system (OS), and data are saved. The option that best describes the average amount of stored data per user for the first eight years of the application existence is memory.
Learn more about data from
https://brainly.com/question/19243813
#SPJ1
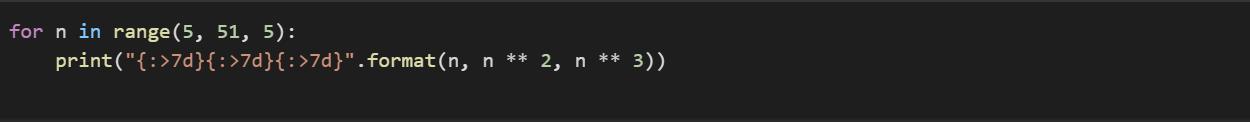
write a python program that uses a for loop with the range function to process the integers from 5 to 50 in increments of 5. see page 182 to learn how to do this with the range function. the loop should also print the square and cube of each integer in a table. the integers column should be centered and 7 characters wide, the squares column should be right-aligned and 8 characters wide, and the cubes column should be right-aligned and 12 characters wide. use an f-string and refer back to pages 70-78 to review formatting. include column headings with the same alignments and display commas for numbers of 1000 or more.
Answers
Using the knowledge in computational language in python it is possible to write the code that uses a for loop with the range function to process the integers from 5 to 50 in increments of 5.
Writing the code:for n in range(5, 51, 5):
print("{:>7d}{:>7d}{:>7d}".format(n, n ** 2, n ** 3))
How do you write a range in Python?The range() function returns a number series in the range sent as an argument. The returned series is an iterable range object and the contained elements will be generated on demand.
It is common to use the range() function with the for loop structure. In this way we have that at each cycle the next element of the sequence will be used in such a way that it is possible to start from a point and go incrementing, decrementing x units.
See more about python at brainly.com/question/18502436
#SPJ1
to properly authenticate, or verify, the identity of authorized users and protect assets from unauthorized users, it is essential to
Answers
To properly authenticate, or verify, the identity of authorized users and protect assets from unauthorized users, it is essential to keep user login.
A person who makes use of a computer or network service is called a user. The system uses a username to identify a user who frequently has a user account (or user name). The phrases handle, which is derived from the same citizens band radio term, login name, screenname (or screen name), account name, nickname (or nick), and screen name are other terms for usernames.
While some software products have no actual end customers, they still provide services to other systems. End users, often known as operators, are the final human consumers of a software product. In contrast to people who support or maintain the product, such system administrators, database administrators, and computer technicians, the end user is not one of these users. The phrase serves to abstractly and clearly separate system creators from users of the software who merely utilize it for their own purposes.
In user-centered design, it also makes a distinction between the software's owner and the customer who pays for its creation as well as other stakeholders who might not use the software directly but contribute to determining its requirements. This abstraction, which refers to a pertinent subset of qualities that the majority of projected consumers would share, is particularly helpful in creating the user interface.
To know more about user click here:
https://brainly.com/question/13122952
#SPJ4
Tricia is managing tasks that have been assigned to her. She needs to enter mileage information in relation to a project which command must she use to access this option?
Answers
Answer:
well she is doing a task
Explanation:
Answer:
task
Explanation:
which two oci virtual cloud network network firewall features can be used to control traffic
Answers
The two OCI virtual cloud network firewall features that can be used to control traffic are Security Lists and Network Security Groups.
Security Lists are used to control traffic at the subnet level, whereas Network Security Groups are used to control traffic at the instance level. Both of these features allow for granular control over traffic flow within the cloud network, helping to ensure the security and integrity of the infrastructure.
Security Lists : Security rules are used to define which types of traffic are allowed to flow in and out of a subnet in a VCN. Security rules are stateful, which means that they allow return traffic that matches the outbound traffic that was allowed. Security rules can be defined based on IP protocol, source and destination IP addresses, source and destination port ranges, and the direction of traffic flow (inbound or outbound).
Network Security Groups: Network security groups are used to define a set of security rules that can be applied to one or more resources in a VCN. A network security group acts as a virtual firewall that controls inbound and outbound traffic to and from the resources that are associated with the group. Network security groups are stateful and can be used to restrict traffic based on source and destination IP addresses, source and destination port ranges, and the direction of traffic flow (inbound or outbound).
To know more about OCI, visit:
https://brainly.com/question/31140085
#SPJ11
the security system has detected a downgrade attempt when contacting the 3-part spn
Answers
Text version of LSA Event 40970 When contacting the 3-part SPN, the security system discovered an attempt to downgrade.
What is a three-part SPN?The service class comes first, the host name comes second, and the service name comes third (if it's present). Adding a ":port" or ":instancename" component as a suffix to the host name part is optional.Text version of LSA Event 40970 When contacting the three-part SPN, the security system discovered an attempt to downgrade. The error message reads, "The SAM database on the Windows Server does not have a computer account for the workstation trust relationship (0x0000018b)" An authentication refusal was made.In every domain of an Active Directory, there is a default account called KRBTGT. It serves as the domain controllers' KDC (Key Distribution Centre) service account.To learn more about Security system refer to:
https://brainly.com/question/29037358
#SPJ4
What is the unit of measure for energy
Answers
Answer:
unit measure of energy is joule
Explanation:
List 5 applications for working with text
Answers
Answer:
TTSReader, Go2PDF, Free File Merge, Batch Text File Editor
Explanation:
Which of the following happens during pre-production?
storyboarding
filmmaking
recording
editing
Answers
explain the look of a document which contains several different font sizes and font colors
Answers
Answer:
Colorful and dynamic?
Explanation:
The look of a document that has several different font sizes and font colors is one that has undergone editing to give it a kind of uniqueness.
What is name of the document?A document file name is said to be the name that is given to an electronic file copy of a document.
The document file name is one that can be written in different ways. The HTML style is known to be an element that is often used to add a lot of styles to an element, such as color, font of a document.
Learn more about document from
https://brainly.com/question/16650739
Use the drop-down menus to match each description with the part of a report where it is located.
named moons in the solar system:
page number printed at the bottom of page 1:
page number printed at the bottom of page 20:
group of data titled “Hawks” in a report on species of migrating birds:
report titled “Technology in the Workplace”:
calculation printed beneath a group of data:
date of a report printed at the top of pages 2–100:
Answers
Answer:
1) Detail
2) Report footer
3) Page footer
4) Group Header
5) Report header
6) Group footer
7) Page header
Explanation:
I just did the assignment
Describe the command structure of Cisco IOS software,
Answers
Cisco IOS software uses a hierarchical command structure. Commands are organized into different modes, and each mode has a set of commands associated with it. Modes are typically accessed by entering a command at the router prompt. For example, the enable mode can be accessed by entering the enable command at the router prompt.
What is Cisco IOS?
The Internetworking Operating System (IOS) is a series of proprietary network operating systems used on numerous Cisco Systems router and network switch models. The system consists of a collection of routing, switching, internetworking, and telephony capabilities that are incorporated into a multitasking operating system. Although the IOS code base includes a cooperative multitasking kernel, most IOS capabilities have been ported to other kernels for usage in Cisco products, such as Linux and QNX. IOS is not supported by all Cisco networking products. Some Cisco Catalyst switches that run IOS XE and Cisco ASR routers that run IOS XE or IOS XR, both of which are Linux-based operating systems, are exceptions. Cisco Nexus switches and Cisco MDS switches both run NX-OS, a Linux-based operating system, in data centre environments.
To learn more about Cisco IOS
https://brainly.com/question/28270325
#SPJ13
true or false? ux designers should consider only current internet users when designing user experiences
Answers
UX designers should consider only current internet users when designing user experiences is a false statement.
What does UX design really entail?The method design teams employ to produce products that offer customers meaningful and pertinent experiences is known as user experience (UX) design. UX design includes components of branding, design, usability, and function in the design of the full process of obtaining and integrating the product.
Note that Making a product or service functional, pleasurable, and accessible is the responsibility of the UX designer. Although many businesses create user experiences, the phrase is most frequently connected to digital design for websites and mobile applications.
Therefore, Note also that UX design is a rewarding career, yes. UX Designers are one of the most sought-after jobs in technology since they are involved at so many phases of a project's life cycle.
Learn more about UX designers from
https://brainly.com/question/898119
#SPJ1
You created a two-dimensional array with the following code.
A = [20, 'tennis', 'blue']
B = [15, 'soccer', 'green']
aList = [A, B]
How do you refer to 'green'?
Answers
Answer:
aList[1][2]
Explanation:
One can refer to the 'green' as per the given array, by aList[1][2].
What is an array?An array is a type of data structure used in computer science that contains a set of elements (values or variables), each of which is identified by an array index or key.
An array is stored in a way that allows a mathematical formula to determine each element's position given its index tuple.
Use the new keyword, a space, the type, the number of rows in square brackets, and the number of columns in square brackets to build an array, as in new int[numRows][numCols].
A 2D array has as many elements as its number of rows twice its number of columns.
Thus, aList[1][2] is the way to represent a two-dimensional array.
For more details regarding array, visit:
https://brainly.com/question/13107940
#SPJ2
Adjust the code you wrote for the last problem to allow for sponsored olympic events. Add an amount of prize money for Olympians who won an event as a sponsored athlete.
The Get_Winnings(m, s) function should take two parameters — a string for the number of gold medals and an integer for the sponsored dollar amount. It will return either an integer for the money won or a string Invalid, if the amount is invalid. Olympians can win more than one medal per day.
Sample Run 1
Enter Gold Medals Won: 1
For how many dollars was your event sponsored?: 5000
Your prize money is: 80000
Sample Run 2
Enter Gold Medals Won: 2
For how many dollars was your event sponsored?: 25000
Your prize money is: 175000
Sample Run 3
Enter Gold Medals Won: 3
For how many dollars was your event sponsored?: 15000
Your prize money is: 240000
Sample Run 4
Enter Gold Medals Won: 4
For how many dollars was your event sponsored?: 1
Your prize money is: 300001
Answers
Here's the adjusted code that takes into account sponsored Olympic events and prize money for Olympians who won an event as a sponsored athlete:
The Program
d. ef G e t _ W i n ni n gs(m, s):
if n o t m . i s d i gi t ( ) o r in t ( m) < 0:
return "Invalid"
else:
nu m _ m e d a l s = i n t ( m )
prize_money = 80 00 0 *n u m _ m e dals
if n u m _ m e da l s > 1:
prize_money += 40 0 0 0 * ( n um _ medals-1)
prize_money += s
return prize_money
medals = input("Enter Gold Medals Won: ")
sponsored_amount = int(input("For how many dollars was your event sponsored?: "))
print("Your prize money is:", Get_Winnings(medals, sponsored_amount))
In this adjusted code, the Get_Winnings function takes two parameters: m for the number of gold medals won, and s for the number of dollars sponsored for the event. The prize money is calculated based on the number of medals won and the sponsored amount, using the same formula as in the previous problem.
To include the sponsored amount, the prize_money variable is increased by s. This assumes that the sponsored amount is added to the total prize money won by the athlete, rather than being a separate prize.
The main code block prompts the user for the number of gold medals won and the sponsored amount and then calls the Get_Winnings function with those values. The resulting prize money is printed on the console.
Note that in the sample runs, the prize money seems to be calculated based on the number of gold medals won, rather than the total number of medals won. If that is not the desired behavior, the prize money calculation can be adjusted accordingly.
Read more about programs here:
https://brainly.com/question/26134656
#SPJ1
How do i fix this? ((My computer is on))

Answers
Answer:
the picture is not clear. there could be many reasons of why this is happening. has your computer had any physical damage recently?
Answer:your computer had a Damage by u get it 101 Battery
and if u want to fix it go to laptop shop and tells him to fix this laptop
Explanation:
When a person can present their own ideas without barreling over the other person and their ideas, they are exhibiting
Answers
Answer:
Assertiveness.
Explanation:
Assertiveness can be defined as a social skill and communication style in which an individual expresses his or her feelings, ideas, desires, opinions, needs or even their rights without being disrespectful to the other party.
Basically, an individual who communicates effectively without being aggressive and disrespectful is said to possess an assertive communication skills.
This ultimately implies that, this kind of individual can effectively combine his behavioral, cognitive and emotional traits while communicating with others.
Hence, when a person can present their own ideas without barreling over the other person and their ideas, they are exhibiting assertiveness.
How is the search engine different from web directory and pls within 5 mins
Answers
Answer:
The search engine is different from a web directory because a web directory is a written list of websites to aid in exploring the Web, whilst a search engine finds the best and closest matched websites to what you typed in the search bar to help you with what you searched up.
Before using the internet to search for information, you need to
A ask a trusted adult
B charge your device
-----the ones that I feel would be right-----
C select your Boolean operators
D think about your keywords
Answers
as this is a school project I would say A ask a trusted adult
hope it helps
WC Full form in computer
Answers
Answer:
word count commonly,operating, machine particular,used for, technology, education, research
what is an example of an absolute cell reference
Answers
Answer:
Absolute cell referencing uses dollar sign with the row number and column name. When any formula with absolute referencing is copied, the cell addresses used remain the same.
Explanation:
true or false? internet of things (iot) devices cannot share and communicate your iot device data to other systems and applications without your authorization or knowledge.
Answers
The statement "internet of things (iot) devices cannot share and communicate your iot device data to other systems and applications without your authorization or knowledge" is false because Internet of Things (IoT) is a broad concept that refers to the networked interconnection of everyday devices.
IoT encompasses all physical devices that have the capacity to connect to the internet or with each other to share data or communicate. IoT gadgets, which are typically connected to a remote server, are used to monitor and regulate their daily activities or environment without human intervention. IoT data sharing and communication are the ways in which an IoT device communicates with other devices to exchange data. IoT devices exchange data through a variety of methods, including Wi-Fi, Bluetooth, cellular, and satellite communication. When connected to the internet, IoT gadgets can easily share data with other devices, including computers, smartphones, and tablets, using internet protocols.
Learn more about internet of things: https://brainly.com/question/29640222
#SPJ11
Which two statements describe a fixed configuration Ethernet switch?(Choose two.)
A. The switch cannot be configured with multiple VLANs.
B. An SVI cannot be configured on the switch.
C. A fixed configuration switch may be stackable.
D. The number of ports on the switch cannot be increased.
E. The port density of the switch is determined by the Cisco IOS.
Answers
A fixed configuration Ethernet switch refers to a switch where the number of ports is pre-determined and cannot be modified. The two statements that describe a fixed configuration switch are:
C. A fixed configuration switch may be stackable - This means that multiple switches can be connected together to form a single logical switch. This is useful when there is a need for more ports than what a single switch can offer.
E. The port density of the switch is determined by the Cisco IOS - Port density refers to the number of ports that a switch can support. In a fixed configuration switch, the port density is determined by the Cisco IOS, which is the operating system that runs on the switch. This means that the maximum number of ports that a switch can have is limited by the capabilities of the IOS.
In summary, a fixed configuration Ethernet switch has a pre-determined number of ports that cannot be modified, and the port density is determined by the Cisco IOS. However, a fixed configuration switch can be stackable, which allows for the creation of larger logical switches.
To learn more about switch click here: brainly.com/question/30675729
#SPJ11
Both instructions and data in a digital
computer are represented as binary
digits. True False
Answers
Answer:
False
Explanation:
insturctions are represented in binary numbers, data are represented in decimal numbers.
Which Information Does a Traditional Stateful Firewall Maintain?
a. A stateful firewall keeps track of all incoming and outgoing traffic and compares it against a set of predefined rules. If the traffic does not match the rules, it is blocked.
b. A stateful firewall can also keep track of different types of traffic, such as UDP or TCP, and allow or deny based on that information.
c. A stateful firewall can keep track of different connections and allow or deny them based on the connection’s state.
Answers
A traditional stateful firewall maintains information about different connections and allows or denies them based on the connection’s state. The correct option is c.
A traditional stateful firewall is a firewall that has the ability to monitor the state of active connections and block those that are deemed dangerous. A stateful firewall maintains information about different connections and allows or denies them based on the connection's state. This type of firewall keeps track of all incoming and outgoing traffic and compares it against a set of predefined rules.A traditional stateful firewall maintains information about different connections and allows or denies them based on the connection’s state. If a packet is accepted, the firewall remembers this and automatically permits all future packets that are part of the same connection. It also filters packets based on source and destination address, source and destination port, and the direction of the packet (inbound or outbound). Stateful firewalls can also monitor the state of active connections and block those that are deemed dangerous.Traditional stateful firewalls offer the following benefits:Stateful inspection: This firewall inspects all data packets that come into and out of the network to ensure they conform to preconfigured security rules. The system recognizes the relationships between packets, and it can thus block potentially dangerous traffic without interrupting legitimate business traffic.Multilayer filtering: These firewalls can filter traffic on many layers of the OSI model, from the network layer to the application layer. The different types of filtering help to protect the network from a wide range of security threats.Easy management: These firewalls are typically simple to set up and manage. They're designed to work out of the box and to require only basic configuration, making them suitable for smaller businesses with less complex needs.Therefore, the correct option is c.Learn more about firewalls: https://brainly.com/question/13693641
#SPJ11