why is this not working for my plus membership
Answers
Answer:
The overwhelming main cause for PlayStation Plus subscriptions not being recognised is because of PlayStation server maintenance which prevents your PS4 from communicating with Sony and discovering that you are a paid up PS Plus subscriber.
Related Questions
我对汉语的兴趣 làm đoạn văn theo đề trên
Answers
Answer:
which language is this
Explanation:
Chinese or Korea
any device that performs single conversion is ____
Answers
Answer:
modulator
Explanation:
A modulator is a device that performs modulation.
(Single conversation)
What if is a forecasting game, below are actions on your document and all you have to do is predict what will happen after the action is taken. Write your answer on a separate sheet of paper. 1. Triple click on the paragraph 2. Pressing Ctrl + A 3. Double click within the word 4. Pressing key combinations Shift + arrow key 5. Pressing key combinations Ctrl + End
Help me please
Answers
Answer:
Where is the question
Explanation:
HOPE IT'S USEFUL
The attenuation of a signal is -10 dB. What is the final signal power if it was originally
5 W?
Answers
Answer:
P₂ = 0.5 W
Explanation:
It is given that,
The attenuation of a signal is -10 dB.
We need to find the final signal power if it was originally 5 W.
Using attenuation for signal :
\(dB=10\text{log}_{10}(\dfrac{P_2}{P_1})\)
Put dB = -10, P₁ = 5 W
Put all the values,
\(-10=10\text{log}_{10}(\dfrac{P_2}{5})\\\\-1=\text{log}_{10}(\dfrac{P_2}{5})\\\\0.1=\dfrac{P_2}{5}\\\\P_2=5\times 0.1\\\\P_2=0.5\ W\)
So, the final signal power is 0.5 W.
The final signal power if it was originally 5W is; 0.5 W
Signal PowerWe are given;
Attenuation signal; dB = -10 dBOriginal signal power; P1 = 5 WFormula for attenuation signal is;
dB = 10log_10_ (P2/P1)
Where P2 is final signal power
Thus;
-10 = 10log_10_(P2/5)
-10/-10 = log_10_(P2/5)
-1 = log_10_(P2/5)
0.1 = P2/5
P2 = 0.1 × 5
P2 = 0.5 W
Read more about signal power at; https://brainly.com/question/13315405
UGC approved by sikkim manipal university approved by UGC or not?
Answers
The UGC approved by sikkim manipal university is approved approved
How to determine that is is approvedSikkim Manipal University (SMU) is a recognized university approved by the University Grants Commission (UGC). However, it's important to note that accreditation and recognition of universities can change over time.
To get the most up-to-date and accurate information about the current status of SMU's approval by UGC, I recommend contacting the university directly or visiting the UGC website for the latest list of recognized universities.
Read more on universities here:https://brainly.com/question/1086066
#SPJ1
Write a java program to do the following :

Answers
A Java program that accomplishes the tasks you described is given below.
How to explain the informationclass ShapePanel extends JPanel {
private static final int PANEL_WIDTH = 500;
private static final int PANEL_HEIGHT = 500;
private static final int X_OFFSET = 20;
private static final int Y_OFFSET = 20;
private static final Point[] originalPoints = {
new Point(160, 130),
new Point(220, 130),
new Point(220, 160),
new Point(190, 180),
new Point(160, 160)
};
private static final int REFLECTION_LINE = -1;
private static final int REFLECTION_LINE_OFFSET = 500;
private static final int SHAPE_SIZE = 50;
private static final int NUM_SHAPES = 8;
private static final int SHAPE_SPACING = 70;
private static final double ANGLE = 90;
protected void paintComponent(Graphics g) {
super.paintComponent(g);
Graphics2D g2d = (Graphics2D) g;
// Draw original shape
g2d.setColor(Color.RED);
drawShape(g2d, originalPoints);
// Reflect shape about the line Y = -X + 500
Point[] reflectedPoints = reflectPoints(originalPoints, REFLECTION_LINE, REFLECTION_LINE_OFFSET);
g2d.setColor(Color.BLUE);
drawShape(g2d, reflectedPoints);
// Draw shapes using loops and methods
g2d.setColor(Color.GREEN);
int startX = X_OFFSET;
int startY = Y_OFFSET;
private Point[] createShape(int startX, int startY) {
Point[] shape = new Point[4];
shape[0] = new Point(startX, startY);
shape[1] = new Point(startX + SHAPE_SIZE, startY);
shape[2] = new Point
Learn more about program on
https://brainly.com/question/23275071
#SPJ1
Write a Python 3 script in PyCharm that will simulate the game of "Rock, Paper, Scissors": Display a header and the simple rules of RPS Prompt player_1 for their move To make sure player_2 can't see what player_1's move was, insert: print('*** NO CHEATING ***\n\n' * 20) Prompt player_2 for their move Design and develop an IF-ELSE structure to play the game IF player_1's move equivalent to player_2's move, "It's a tie" "rock" beats "scissors" "scissors" beats "paper" "paper" beats "rock" Make sure you test for valid input!!
Answers
Answer:
'''
Rock, Paper, Scissors:
The Rules:
If player1's move equivalent to player2's move, "It's a tie".
"rock" beats "scissors", "scissors" beats "paper", and "paper" beats "rock"
'''
player_1 = input("Player 1's move: ")
print('*** NO CHEATING ***' * 20)
player_2 = input("Player 2's move: ")
if player_1 or player_2 not in ["rock", "paper", "scissors"]:
print("Invalid input!")
if player_1 == player_2:
print("It's a tie")
else:
if player_1 == "rock":
if player_2 == "scissors":
print("Player 1 won")
elif player_2 == "paper":
print("Player 2 won")
elif player_1 == "scissors":
if player_2 == "paper":
print("Player 1 won")
elif player_2 == "rock":
print("Player 2 won")
elif player_1 == "paper":
if player_2 == "rock":
print("Player 1 won")
elif player_2 == "scissors":
print("Player 2 won")
Explanation:
In the comment part, put the header and the rules of the game
Ask the user to enter the player1's move
Print the asterisks
Ask the user to enter the player2's move
If any of the input is not "rock", "paper", "scissors", state that the input is invalid
Check the inputs. If they are equal, print that it is a tie. Otherwise:
If player1's move is rock. Check player2's move. If it is "scissors", player1 wins. If it is "paper", player2 wins
If player1's move is scissors. Check player2's move. If it is "paper", player1 wins. If it is "rock", player2 wins
If player1's move is paper. Check player2's move. If it is "rock", player1 wins. If it is "scissors", player2 wins
Explain the schema to be followed when solving a dp problem
Answers
Answer:
Every Dynamic Programming problem has a schema to be followed: Show that the problem can be broken down into optimal sub-problems. Recursively define the value of the solution by expressing it in terms of optimal solutions for smaller sub-problems. Compute the value of the optimal solution in bottom-up fashion.
asumme the input amalog voltage is changing between -5 to 5V;using a10bit A/D cconverter.calculate the number of quantization levels.calculate the voltage resolution
Answers
Answer:
0.0098 V or 9.8 mV.
Explanation:
A 10-bit ADC can convert an analog input voltage into one of 1024 discrete values. The formulas to find the number of discrete values and the voltage resolution are:
- Number of discrete values = 2^n, where n is the bit depth of the ADC. For a 10-bit ADC, n = 10, so the number of discrete values is 2^10 = 1024.
- Voltage resolution = (Vmax - Vmin) / (Number of discrete values - 1), where Vmax and Vmin are the highest and lowest voltages of the analog input. For an analog input range of -5V to 5V, Vmax = 5V and Vmin = -5V, so the voltage resolution is (5 - (-5)) / (1024 - 1) = 0.0098 V or 9.8 mV.
how do artificial intelligence ,machine learning ,and deep learning differ from each other?
Answers
Answer:
Artificial Intelligence is the concept of creating smart intelligent machines. Machine Learning is a subset of artificial intelligence that helps you build AI-driven applications. Deep Learning is a subset of machine learning that uses vast volumes of data and complex algorithms to train a model.

I'm trying to figure out how to put this together can anyone help me solve this?

Answers
The if-else statement to describe an integer is given below.
How to illustrate the informationThe if-else statement to describe an integer will be:
#include <stdio.h>
#include <stdbool.h>
int main(void) {
int userNum;
bool isPositive;
bool isEven;
scanf("%d", &userNum);
isPositive = (userNum > 0);
isEven = ((userNum % 2) == 0);
if(isPositive && isEven){
printf("Positive even number");
}
else if(isPositive && !isEven){
printf("Positive number");
}
else{
printf("Not a positive number");
}
printf("\n");
return 0;
}
Learn more about integers on:
https://brainly.com/question/17695139
#SPJ1
TO EXIT WORD YOU CLICK WHAT
Answers
(Or the X in the corner?)
Answer:
To exit Word, you can click on the "File" menu and then click "Exit" or "Close".
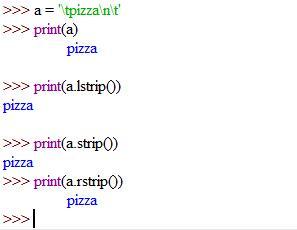
#Question 4: #Use a variable to represent the name of a food. You are then going to print this variable four times. Before you do, Print the food out and include some white space characters at the beginning and end and use "\t" and "\n" a least once. Then print the food once so the white space is displayed. Remember, you may not be able to see the white space on the right hand side. Following the food name print, print the name out three additional times (a total of four times), once normally, and one for each of the three stripping functions lstrip(), rstrip(), and strip().
Answers
Answer:
see the picture
Explanation:
Jessica is concerned about losing data due to a hard disk failure. Her computer will only support a maximum of three disks. To protect her data, she has decided to use RAID (Redundant Array of Independent Disks).
Which of the following RAID types would give Jessica the BEST mirrored data protection?
a. RAID 0
b. RAID 1
c. RAID 5
d. RAID 10
Answers
RAID 1 would provide Jessica with the BEST duplicated data security, according to the query.
An independent disk system with redundancy is what?A technique for duplicating or striping data across numerous low-end disk drives; this improves mean time between failures, throughput, and error correction by copying data across multiple drives.
Why is it vital to have a robust array of independent disks?By archiving the same information on various disk drives and solid-state drives, RAID (distributed array of independent disks) is a way to safeguard data in the case of the a drive failure (SSDs). There are many RAID levels, though, and not every one of them strive to offer redundancy.
To know more about Redundant Array visit:
https://brainly.com/question/13163060
#SPJ4
1. Create a function called numberGuess. Function numberGuess will first choose a random number in the range 1 to 1000. The number that is chosen is what the user is supposed to guess. Following this, your function should then display the following
The player then types a first guess. The function responds with one of the following:
Your function must not stop asking for guesses until the user has provided a correct solution. Your program should keep telling the player Too high or Too low to help them narrow down the answer. Count the number of guesses the player makes. At the end when the user finally guesses correctly, print Either you know the secret or you got lucky! if the number of guesses were 10 or less. If the player guesses the number in 10 tries, then print Ahah! You know the secret! If the player makes more than 10 guesses, then print You should be able to do better!
-
- I already have some code however not sure if its 100% correct
Please review feedback will appreciated, thanks
#include
using namespace std;
int main()
{
int num, guess, tries = 0;
srand(time(0)); //seed random number generator
num = rand() % 1000 + 1; // random number between 1 and 1000
cout << "I have a number between 1 and 1000"< > guess;
tries++;
if (guess > num)
cout << "Too high!\n\n";
}
while(guess < num);
cout << "Too low!\n\n";
if(10<=guess)
cout << "\nCorrect!either you know the secret or you got lucky" << tries << " guesses!" <
{
} if (guess==10){
cout<<" Ahah! You know the secret!"<
}
else
{
cout<< "You should be able to do better! ";
cout<< " Would you like to play again? (Y/N)";
}
}
Answers
You can edit this code whatever you want! Good luck.


If you can answer theses ill give u a brainliest (i think thats how u spell it) but only if u get it right u will get one NOT A SCAM!!
Question: In which logical operator at least one condition has to be true?
O or
O None of the above
O not
O and
Question: In which logical operator both conditions must be true?
O and
O or
O not
O None of the above
Answers
Answer:
or / and
Explanation:
i took the quiz at unitek college
Answer:
1. or
2. and
Explanation:
Help me with this digital Circuit please




Answers
A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Thus, These circuits receive input signals in digital form, which are expressed in binary form as 0s and 1s. Logical gates that carry out logical operations, including as AND, OR, NOT, NANAD, NOR, and XOR gates, are used in the construction of these circuits.
This format enables the circuit to change between states for exact output. The fundamental purpose of digital circuit systems is to address the shortcomings of analog systems, which are slower and may produce inaccurate output data.
On a single integrated circuit (IC), a number of logic gates are used to create a digital circuit. Any digital circuit's input consists of "0's" and "1's" in binary form. After processing raw digital data, a precise value is produced.
Thus, A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Learn more about Digital circuit, refer to the link:
https://brainly.com/question/24628790
#SPJ1
The mode of a sequence of numbers is the number or numbers that appear most frequently in the sequence.
Design a program that computes the mode of a sequence of random numbers. The range of the random number is from 1 to 9 inclusively.
Answers
An unpredictable floating-point value between 0 and 1 is the result of the random() function.
What is random random () Python?Create a list of random numbers in Python starting from "start" to "end" with the supplied lower and upper bounds.
Here, we'll generate any random number in Python using a variety of techniques.
One of Python's built-in modules, the Random module, is used to produce random integers.
Since these numbers are not completely random, they are pseudo-random.
Using this module, one can generate random integers, print a random value for a list or string, among other random operations.
Examples:
Number: 10, Start: 20, End: 40
Output: [23, 20, 30, 33, 30, 36, 37, 27, 28, 38]
Explanation: Ten random numbers in the [20, 40] range are included in the result.
Enter the following information: num = 5, start = 10, and end = 15.
Output: [15, 11, 15, 12, 11]
Explanation: The result includes 5 random numbers between [10, 15].
To Learn more About random() function refer To:
https://brainly.com/question/20693552
#SPJ1
In what year was napier bone invented
Answers
The Napier's Bones is a manually-operated calculating device, invented by the Scottish mathematician John Napier in the early 17th century, around the year 1617.
What is Napier bone used for?Napier's Bones, also known as Napier's rods, are used for multiplication, division, and square root calculations. The device consists of a set of rectangular rods or bones with each bone representing a single digit in the multiplication table.
By manipulating the rods, users can quickly perform calculations that would otherwise be time-consuming to complete by hand. The Napier bone is an early example of a calculating device and is considered a predecessor to modern mechanical calculators.
Learn more about Napier bone at:
https://brainly.com/question/24242764
#SPJ1
Performance assessments are conducted periodically and .
Answers
Performance assessments are conducted periodically and systematically.
What are performance assessments ?Periodic and structured evaluations are essential to maintain accurate assessments of performance. These reviews usually occur regularly, such as once or twice a year, and follow a systematic process designed to examine an individual's job-related skills consistently using objective standards.
A typical appraisal procedure generally includes establishing clear aims and goals for the employee, offering regular coaching along with feedback throughout the appraisal term, compiling data related to their task progress, and then conducting a comprehensive review at the end of that period to analyze and assess it thoroughly.
Find out more on performance assessments at https://brainly.com/question/1532968
#SPJ1
Write pseudocode for a new implementation o BFS that uses an adiacencv matrix instead of an aclacency nst.Find the time complexity of this new version and compare it to the version seen in class. Under what circumstances are they equally efficient?
Answers
Pseudocode for the new implementation of BFS using an adjacency matrix:
```
BFS(adjacency_matrix, start_node):
Create a queue and enqueue the start_node
Create a visited array and mark the start_node as visited
While the queue is not empty:
Dequeue a node from the queue
Process the node
For each adjacent node in the adjacency matrix:
If the adjacent node is not visited:
Mark the adjacent node as visited
Enqueue the adjacent node
```
The time complexity of this new version of BFS using an adjacency matrix is O(V^2), where V is the number of vertices. This is because we need to iterate over each element in the adjacency matrix to check the connections between nodes. In the worst case, we may need to visit every entry in the matrix, resulting in a quadratic time complexity.
In comparison, the version of BFS seen in class using an adjacency list has a time complexity of O(V + E), where V is the number of vertices and E is the number of edges. This version is more efficient because it only visits the nodes and edges that are present in the graph, rather than iterating over all possible connections as in the adjacency matrix implementation.
The two versions are equally efficient when the graph is dense and the number of edges approaches the maximum possible value of V^2. In this scenario, the time complexity of both implementations becomes similar, as the number of iterations required in the adjacency matrix version is comparable to the number of edges in the adjacency list version. However, in most practical cases, where the graph is sparse (fewer edges compared to the total possible connections), the adjacency list version is more efficient.
For more such answers on Pseudocode
https://brainly.com/question/24953880
#SPJ8
a person who is always and constantly online
Answers
Answer:
These individuals are called "netizens" or "nethead"
In c++, make the output exactly as shown in the example.

Answers
Answer:
Here's a C++ program that takes a positive integer as input, and outputs a string of 1's and 0's representing the integer in reverse binary:
#include <iostream>
#include <string>
std::string reverse_binary(int x) {
std::string result = "";
while (x > 0) {
result += std::to_string(x % 2);
x /= 2;
}
return result;
}
int main() {
int x;
std::cin >> x;
std::cout << reverse_binary(x) << std::endl;
return 0;
}
The reverse_binary function takes an integer x as input, and returns a string of 1's and 0's representing x in reverse binary. The function uses a while loop to repeatedly divide x by 2 and append the remainder (either 0 or 1) to the result string. Once x is zero, the function returns the result string.
In the main function, we simply read in an integer from std::cin, call reverse_binary to get the reverse binary representation as a string, and then output the string to std::cout.
For example, if the user inputs 6, the output will be "011".
Hope this helps!
given a list of distinct integers from 0 to a value max value, write a function to produce a string that describes the ranges of numbers missing from the list. the items in the result should be sorted in ascending order and separated by commas. when a gap spans only one number, the item is the number itself; when a gap is longer, the item comprises the start and the end of the gap, joined with a minus sign.
Answers
Essentially, it is a variant of Insertion Sort. In insertion sort, we only shift items one place forward. Many moves are required when an element must be pushed far ahead.
The goal of Shell Sort is to enable the interchange of distant goods. For a big value of h, we use Shell sort to sort the array. We keep decreasing the value of h until it equals one. If all sub lists of every hitch element are sorted, an array is said to be h-sorted.
SHELL SORT IS A PROCEDURE (ARRAY, N)
WHILE GAP LENGTH(ARRAY) /3: GAP = (INTERVAL * 3) + 1 END WHILE LOOP WHILE GAP > 0: FOR (OUTER = GAP; OUTER LENGTH(ARRAY); OUTER++): INSERTION VALUE = ARRAY[OUTER] INNER = OUTER; WHILE INNER > GAP-1 AND ARRAY[INNER - GAP]
ARRAY[INNER] = ARRAY[INNER - GAP] = INSERTION VALUE
INNER - GAP END = INNER WHILE LOOP
ARRAY[INNER] = INSERTION VALUE END FOR LOOP GAP = (GAP -1) /3; END FOR LOOP GAP = (GAP -1) /3; END
FOR LOOP GAP = (G SHELL SORT WHILE LOOP END
Learn more about ARRAY from here;
https://brainly.com/question/19570024
#SPJ4
James has a USB flash drive that he has used at work. The drive needs to be thrown away, but James wants to make sure that the data is no longer on the drive before he throws it away. What can James use to wipe the data clean?
a. Zero-fill utility
b. Format the drive
c. ATA Secure Erase
d. Smash the USB drive
Answers
Answer:
C. ATA Secure Erase
D. Smash the USB drive
Explanation:
Zero fill utility is a specialized way of formatting a storage device particularly secondary storage such as hard disk, flash drive e.t.c. In this process, the disk contents are overwritten with zeros. Once this has been done, undoing is essentially hard but possible. In most cases, this might just mean that the data content is corrupt and as such might still be recovered, maybe not in its pure entirety.
Formatting the drive on another hand does not essentially mean cleaning the drive and wiping off data. It just means that operating systems cannot see those data contents anymore. They are still present in the drive and can be recovered.
ATA Secure Erase is actually a way of completely and permanently erasing the content in a drive. Once the function has been done, undoing is not possible. Both the data content and even the data management table will be completely gone.
Smashing the USB drive is the surest way of cleaning data as that will permanently destroy the working components of the drive such as the memory chip. And once that happens then there's no drive let alone its contents.
Use your own words to discuss the following:
Question One
Using spreadsheets or typical computer-based filing systems looks a reasonable choice for organizing personal data. However, it is not sufficient to use such systems when the amount of data becomes huge. In such case, it may be time to implement a database.”?
Question Two
Define five mini-world Entities and five Relationships for a hospital database system.?
Answers
Answer One:
Spreadsheets or typical computer-based filing systems are useful tools for organizing personal data.
How sufficient are spreadsheets?However, when the volume of data becomes extensive, they may not be sufficient. In such situations, it may be appropriate to use a database to manage and organize data more effectively. Databases provide a more structured approach to data storage and management, making it easier to retrieve and manipulate large amounts of data quickly and efficiently.
Answer Two:
Entities are objects or concepts in a system that we want to store information about. Relationships describe how these entities interact with each other. For a hospital database system, five mini-world entities could be patients, doctors, medical staff, departments, and medical equipment. Five relationships could be:
A patient can be admitted to a department for treatment
A doctor can be assigned to one or more departments
Medical staff can work in one or more departments
Medical equipment can be assigned to a department
A patient can be treated by one or more doctor
Read more about spreadsheets here:
https://brainly.com/question/26919847
#SPJ1
A flashlight bulb uses 2.4 W of power when the current in the bulb is 0.8 A. What is the voltage difference?
Answers
Answer:
3 Volts.
Explanation:
Answer:
3 Volts
Explanation:
Because Power = Voltage x Current, so if you substitute the values into the equation, it would be :
2.4 W = Voltage x 0.8 A
Then if you rearrange the equation, it would be :
2.4 W / 0.8 A = Voltage
Which is :
3 V = Voltage
What is the main difference between structured and unstructured data?
Answers
Answer:
Please mark Brainliest, Look Down
Explanation:
Structured data vs. unstructured data: structured data is comprised of clearly defined data types with patterns that make them easily searchable; while unstructured data – “everything else” – is comprised of data that is usually not as easily searchable, including formats like audio, video, and social media postings.
Answer:
Structured data is data that appears in pre-defined models. It is organized and fits into templates and spreadsheets, making it easy to analyze. In contrast, unstructured data is not predefined and the data has no form or system to follow. It can come in the form of images, videos, text, and audio, and can be challenging to analyze.
Between structured and unstructured data, there is semi-structured data. Semi-structured data is a combination of organized data and unorganized text. For example, email is considered semi-structured because the body within the email can be unstructured but the email itself can be organized into different folders.
Explanation:
A person can only give blood to someone with compatible blood antigens. If a person receives blood from someone with an incompatible blood type, it can cause a life threatening immune system reaction. The blood transfusion will likely fail.
Your program should ask a user’s blood type first, then if she/he want to learn about giving or receiving blood. Based on the blood type and choice of give or receive, your program will print the corresponding compatible blood types.
NOTE, if the blood type or give/receive choice entered doesn’t exist, the program should promote the user to re-enter it again.
Answers
What's language processor?
Answers
Answer:
A language processor is a software program designed or used to perform tasks such as processing program code to machine code. Language processors are found in languages such as Fortran and COBOL.
Compilers, interpreters, translate programs written in high-level languages into machine code that a computer understands. And assemblers translate programs written in low-level or assembly language into machine code.