Write a basic
to solve
30x10
Answers
Answer:
30x10
Explanation:
3 times 10 = 30
30 times 10 = 300
Answer:
30x10=300
Explanation:
3x10=30
30x10= 300
(just add another zero, if that makes sense)
Related Questions
True or False: On a form, the text box and its label would be considered two different controls.
Answers
The given statement, "The text box and its label are separate controls on a form," is true because the label is used to identify and provide context for the text box.
In graphical user interface (GUI) design, a form is typically composed of various controls or components that allow users to input data or interact with the application. A text box is a control used to input or display textual information, while a label is a control used to provide descriptive text or captions for other controls.
The text box and its label are separate controls with distinct functionalities. The label is used to provide a clear description or prompt for the associated text box, helping users understand the purpose or expected input of the text box. The text box itself is where users can enter or view the actual text or data.
By separating the label and the text box as separate controls, it allows for better organization, clarity, and flexibility in the form design. Each control can have its own properties, such as font, size, alignment, and events, which can be set independently to meet specific design and functional requirements.
Learn more about text box:
https://brainly.com/question/29752050
#SPJ11
I NEED HELP!! THIS IS 3D COMPUTER MODELING COURSE IN CONNEXUS
the coordinate's that determine the position of an element in space are expressed as. Different shapes, 1,2, and 3/ x,y,z/l,t,p
refer to the pictures




Answers
6. x, y, and z (x is right, z is forward, and y is up)
7. true
8. plane
9. Cartesian grid
10. They describe a location using the angle and distance from the original.
11. effects that alter the look of an object.
12. true
13. true
14. (not sure, but I would go with conceptual)
15. 3-D elements
Hope this helps! Please let me know if you need more help, or if you think my answer is incorrect. Brainliest would be MUCH appreciated. Have a great day!
Stay Brainy!
what are the tyoe of typical application of mainframe computer
Answers
Explanation:
customer order processingfinancial transactions production and inventory control payrollhope it is helpful to you
Ginny is about to rent a movie online and is trying to decide which resolution will give her the best viewing experience. She plans to watch the video on her laptop, which offers a display resolution of up to 1920 x 1080. Which video resolution should Ginny select
Answers
The resolution Ginny should select is FHD.
What is the video resolution?In technology, the term video resolution refers to the number of pixels per frame. This is important because the number of pixels affects how clear and detailed images are in the video. More common video resolutions are:
HD8K4K720 pHow to select the best resolution?The resolution you select for the video should match the resolution the display offers. In the case of Ginny, a 1920 x 1080 resolution matches an FHD or Full High Definition resolution that has exactly the same values, so this is the best resolution Ginny can choose.
Learn more about Full High Definition in: https://brainly.com/question/5641128
which type of attack is carried out by threat actors against a network to determine which ip addresses, protocols, and ports are allowed by acls?
Answers
The type of attack carried out by threat actors against a network to determine which IP addresses, protocols, and ports are allowed by ACLs is called a Reconnaissance Attack.
A reconnaissance attack involves the collection of information about a target network without necessarily compromising it. Threat actors use various tools and techniques to scan the network for open ports, IP addresses, and protocols allowed by ACLs. They gather this information to identify vulnerabilities and plan their subsequent attacks. This type of attack is considered the first step in the cyber attack lifecycle, as it helps attackers to create a detailed map of the target network for a successful intrusion.
In summary, a reconnaissance attack is the method employed by threat actors to gather crucial information about a network's IP addresses, protocols, and ports allowed by ACLs, enabling them to identify potential vulnerabilities and plan their attacks effectively.
To know more about cyber attack visit:
https://brainly.com/question/29997377
#SPJ11
which of the following cannot be coprighted (1 point)
A.books
B.inventions
C.videos
D.music
Answers
Design an email based on what you learned about email etiquette in this week’s lecture. Include all elements you think are appropriate for a professional email.
Answers
A professional email should include various elements to adhere to email etiquette. These elements consist of a clear and concise subject line, a formal greeting, a brief and focused message, proper grammar and punctuation, a professional closing, and appropriate attachments if necessary.
When designing a professional email, it is important to consider email etiquette guidelines. Start with a clear and concise subject line that reflects the purpose of the email. Begin the email with a formal greeting, addressing the recipient by their appropriate title and name. Keep the body of the email focused and brief, using proper grammar and punctuation. Use a professional and polite tone throughout the message. Conclude the email with an appropriate closing, such as "Sincerely" or "Best regards," followed by your name and contact information. If there are any necessary attachments, ensure they are properly labeled and referenced in the email. By following these elements, your email will demonstrate professionalism and enhance effective communication.
To learn more about professional email click here : brainly.com/question/30760750
# SPJ11
If you were designing facial recognition software based on machine learning,
how would you avoid algorithmic bias?
O A. Make sure to avoid using any algorithms in the program
O B. Ask the programmers if they are biased against groups of people
O C. Use training images that show a diverse group of people
D. Use photos with people facing in all different directions
Answers
To avoid algorithmic bias, Ask the programmers if they are biased against groups of people.
How do you avoid an algorithm bias?The right step is to avoid this kind of bias is to take a record of inventory of the algorithms. Note that Developers can communicate with stakeholders to know more about about how and when algorithms are being applied.
Once you have known the algorithms, then you can appoint a person to monitor the algorithms, mostly among wide groups.
Learn more about algorithm from
https://brainly.com/question/24953880
Instructions
Write a one-line program to output the following haiku. Keep in mind that for a one-line program, only one print command is used.
Moon and stars wonder
where have all the people gone
alone in hiding.
- Albrecht Classen.
Hint: Remember that the escape sequences \n and \t can be used to create new lines or tabs for extra spacing.
Answers
Answer:
python
Explanation:
print("Moon and stars wonder\nwhere have all the people gone\nalone in hiding.\n- Albrecht Classen.")
In Microsoft Windows 10,

Answers
Answer: Cancel all Print Jobs
Explanation: Whoever gave you this clearly doesn't know how to themselves cause the exact wording to cancel all print jobs is as follows
"Cancel All Documents". if this was a teacher tell them to read up on their technology skills before they give the next test. I'm currently working on my Master's in computer Programming and have been working with Computers for over 15 years. I could put a better multiple choice quiz together in less than 10 mins. I wonder how long it took this idiot to put that quiz together.
4.8 code practice question 1 edhesive
Answers
Answer:
for x in range(5,76,5):
print(x, end=" ")
Explanation:
Hope this helps lovely :)
4.8 code practice question 1 adhesive for x in range(5,76,5): print(x, end="").
What is adhesive?Adhesive is defined as anything that has the ability to functionally hold materials together through surface adhesion that resists separation. PCs and laptops have numerous adhesive applications, primarily for joining electric components. In the construction of laptops, cyanoacrylates, acrylics, epoxies, UV curables, and hybrid adhesives are all utilized.
Code is defined as the collection of rules or instructions that are written in a specific programming language. In general, programming statements written by a programmer using a text editor or visual programming tool and then saved in a file are referred to as source code.
Thus, 4.8 code practice question 1 adhesive for x in range(5,76,5): print(x, end="").
To learn more about adhesive, refer to the link below:
https://brainly.com/question/29061431
#SPJ3
a parcel is thrown downward at a speed of v m/s from an airplane at altitude 11000 m. as it falls, its distance from the ground is given by the formula -4.9t2 - vt 11000, where t is the time in seconds since it was dropped. write a program to output the time it will take to reach the ground. the input to your program is the positive floating-point number v. the required time is given by the quadratic formula
Answers
We are only interested in the positive time it takes for the parcel to reach the ground, we can ignore the negative root. Therefore, the time it will take to reach the ground is t = (v + √(v² + 215600v)) / 9.8.
To find the time it will take for the parcel to reach the ground, we can use the given formula: -4.9t² - vt + 11000, where t is the time in seconds since the parcel was dropped.
We need to solve this quadratic equation for t.
First, let's rewrite the equation in the form ax² + bx + c = 0, where a = -4.9, b = -v, and c = 11000.
Using the quadratic formula, t = (-b ± √(b² - 4ac)) / (2a), we can substitute the values of a, b, and c into the formula.
t = (-(-v) ± √((-v)² - 4(-4.9)(11000))) / (2(-4.9))
t = (v ± √(v² + 215600v)) / 9.8
Since we are only interested in the positive time it takes for the parcel to reach the ground, we can ignore the negative root. Therefore, the time it will take to reach the ground is t = (v + √(v² + 215600v)) / 9.8.
Now, you can write a program that takes the input of the positive floating-point number v and calculates the time it will take for the parcel to reach the ground using the above formula. Don't forget to include the necessary imports and input/output statements in your program.
With proper conclusion, this program will output the time it will take for the parcel to reach the ground.
To know more about speed visit;
brainly.com/question/17661499
#SPJ11
Bonus Problem 3.16: Give an example showing that if we remove the assumption that \( G \) is finite in Problem \( 3.15 \), then the conclusion need no longer follow,
Answers
We can see that if we remove the assumption that the group \( G \) is finite, then the conclusion need not follow.
Give an example showing that if we remove the assumption that \( G \) is finite in Problem \( 3.15 \), then the conclusion need no longer follow:We know that every finite group \( G \) of even order is solvable. But if we remove the assumption that the group \( G \) is finite, then the conclusion need not follow. This can be shown by the example of the general linear group \( GL_n(\mathbb{R}) \) over the real numbers.For all finite fields \( F \) and all positive integers \( n \), the group \( GL_n(F) \) is a finite group of order \( (q^n-1)(q^n-q)(q^n-q^2)…(q^n-q^{n-1}) \), where \( q \) is the order of the field \( F \). But if we take the limit as \( q \) tends to infinity, the group \( GL_n(\mathbb{R}) \) is an infinite group of even order that is not solvable.The group \( GL_n(\mathbb{R}) \) is not solvable because it contains the subgroup \( SL_n(\mathbb{R}) \) of matrices with determinant \( 1 \), which is not solvable. Thus, we see that if we remove the assumption that the group \( G \) is finite, then the conclusion need not follow.
Learn more about real numbers :
https://brainly.com/question/31715634
#SPJ11
For the CART model, if my three terminal node's deviation are
100,200,300. So can I know the deviation of the estimated model? If
yes, what's the value of deviation of the estimated model.
Answers
Yes, you can calculate the deviation of the estimated model for the CART model if the deviation of the three terminal nodes are 100, 200, and 300.
CART stands for Classification and Regression Trees and it is a machine learning technique used for classification and regression analysis of complex data by creating decision trees.
Decision trees are constructed by splitting a dataset into smaller subsets and repeating the process recursively until a termination condition is met
1:Deviation = 100Mean of the node = x1Standard deviation of the node = σ1Therefore,100 = ∑(xi - x1)² / n1where ∑(xi - x1)² is the sum of the squared deviations of the data points from the mean of the node and n1 is the number of data points in the node.
2:Deviation = 200Mean of the node = x2Standard deviation of the node = σ2100 = ∑(xi - x2)² / n2For terminal node
3:Deviation = 300Mean of the node = x3Standard deviation of the node = σ3100 = ∑(xi - x3)² / n3
Now, we can calculate the deviation of the estimated model as follows :d = (n1σ1² + n2σ2² + n3σ3²) / (n1 + n2 + n3)Substituting the values of n1, n2, n3, σ1, σ2, σ3, we get :d = (1(100²) + 1(200²) + 1(300²)) / (1 + 1 + 1)d = 166.67
Therefore, the deviation of the estimated model is 166.67.
To know more Deviation visit:
brainly.com/question/31835352
#SPJ11
What is the MOST likely reason for Karla to set an alarm on her work computer for 50 minutes past the hour every hour?
Question 2 options:
It reminds her to stand up for a few minutes each hour.
It signals that it's meal time.
It wakes her up in case she falls asleep.
It reminds her to readjust the position of her monitor.
Answers
The most likely reason for Karla to set an alarm on her work computer for 50 minutes past the hour every hour is option C: It wakes her up in case she falls asleep.
How were people on time for work before alarm clocks?Ancient Greeks as well as Egyptians created sundials and colossal obelisks that would serve as time markers by casting a shadow that changed with the position of the sun.
Humans created hourglasses, water clocks, as well as oil lamps that measured the passage of time by the movements of sand, water, and oil as early as 1500 B.C.
Therefore, An alarm clock, or simply an alarm, is a type of clock used to warn a person or group of people at a certain time. These clocks' main purpose is to wake people up after a night's sleep or a little nap; however, they can also serve as reminders for other things.
Learn more about alarm clock from
https://brainly.com/question/16452153
#SPJ1
step 1: interpreting the seismograms estimate the times of the first arrival of the p waves and the s waves at each seismograph station. enter these times into your data table. reminder: you are trying to find the difference between the arrival time of the p wave and the s wave. determine the difference between the arrival of the p wave and the arrival of the s wave, and enter this difference into the data table.
Answers
To interpret the seismograms and estimate the times of the first arrival of the P waves and the S waves at each seismograph station, use the following steps:
Look for the point at which the waves first appear on the seismogram. This is the time of the first arrival for each wave type.Record the time of the first arrival of the P wave and the S wave in your data table.Subtract the time of the first arrival of the P wave from the time of the first arrival of the S wave to get the difference between the two.Enter this difference into the data table.Remember that the time difference between the arrival of the P waves and the S waves is an important indicator of the type of seismic event and its location.
learn more about seismograms :
brainly.com/question/27339869
#SPJ11
before you install an rpm package, you want to verify the authenticity of the package and check the digital signature to ensure that it has not been altered. which rpm option should you use?
Answers
The option you should use is "rpm --checksig". This command will verify the digital signature of a specified RPM package and verify that it has not been altered.
What is the RPM ?RPM stands for “Revolutions Per Minute” and is a measure of the speed at which a rotating object turns. It is commonly used to measure the speed of a motor, as well as the speed of a vehicle’s wheels when it is in motion. It is also used to measure the speed of a record player’s turntable and the speed of a fan. RPM is a measure of the number of rotations an object makes in one minute. It is often used in engineering and manufacturing to ensure that a machine is running at the correct speed for its specific application. RPMs can be used to compare the speed of two different motors or machines. RPMs are also used to determine how much power is being generated by an engine or motor.
To learn more about RPM
https://brainly.com/question/13107800
#SPJ4
Who is responsible for providing the equipment employees need to stay safe on the job (like a hardhat or safety
goggles)?
• the Occupational Safety and Health Administration (OSHA)
O the employer
the labor union
O the employee
MacBook Pro
Answers
Answer:
the employer
Explanation:
Answer:
the employer
Explanation:
Which braid is created when the outside strands are crossed under the center strand?
weaving
overlapping
3-strand overbraid
3-strand underbraid
Answers
The braid created when the outside strands are crossed under the center strand is called a 3-strand underbraid.
A 3-strand underbraid is a type of braiding technique where the outside strands are crossed under the center strand, creating a braid that has a smooth and uniform appearance. This braid is commonly used in various hairstyles and can be achieved by starting with three strands of hair, crossing the left strand under the center strand, then the right strand under the center strand, and repeating until the braid is complete. The resulting braid has a unique look and is often used in combination with other braiding techniques to create intricate and beautiful hairstyles.
Learn more about techniques here:
https://brainly.com/question/30078437
#SPJ11
what is the minimum pixel depth, in bytes, that would be needed to store percentages as integer values?
Answers
The minimum pixel depth, in bytes, that would be needed to store percentages as integer values is 1 byte.
Digital information is stored in units called bytes, which typically have eight bits. The byte is the lowest addressable unit of memory in various computer architectures because it was historically the amount of bits needed to encode a single character of text in a computer.
Network protocol specifications such as The Internet Protocol (RFC 791) refer to an 8-bit byte as an octet to distinguish them from the ordinary 8-bit definition. Depending on the bit endianness, an octet's bits are typically counted from 0 to 7 or 7 to 0, respectively. Since the first bit is a zero, the eighth bit is a seven.
To know more about byte click here:
https://brainly.com/question/2280218
#SPJ4
a diagram of a flow chart to find the average of 10 numbers
Answers
Answer:
Kindly check attached picture
Explanation:
Flowchart gives a graphical representation of a steps taken towers the execution of a program.
In the flowchart attached, A variable was initialized and set to 0 ; then a for loop was used to iterate integers 1 up to 10, for each number. It is added to the initialized variable sum until all the 10 integer numbers are added. The the average is obtained by dividing by 10.

which of the following information technology career fields generally requires the lowest level of education for an entry level position?
Answers
Answer:
C
Explanation:
What do computers use to represent on and off? 0 and 1 1 and 2 RGB Megabyte
Answers
List 5 general safety precautions that you can take when working with a computer equipment.
Answers
Answer:
Wear the right clothes, unplug all equipment, keep your work area clean, check for damaged parts, and do not force components into ports.
Explanation:
These are all general safety precautions when working with computer equipment.
âAn organized, generalized knowledge structure in long-term memory is a(n) ____.a. engramb. tracec. icond. schema
Answers
The answer is D. schema. A schema is an organized, generalized knowledge structure in long-term memory that helps individuals make sense of new information and experiences by relating them to existing knowledge and experiences.
The term "knowledge management infrastructure" refers to the tools and environments that support learning and promote the creation and sharing of information inside an organisation. The knowledge structure includes people, information technology, organisational culture, and organisational structure.
The following three core KM infrastructure components, which include social and technical viewpoints, should be considered by every organisation performing KM research: Information technology, organisational culture, and knowledge processes The knowledge management field is divided into three main subfields: accumulating knowledge. sharing and keeping knowledge.
The organisational structure, which determines how and to what extent roles, power, and obligations are divided, controlled, and coordinated, governs information flow throughout levels of management.
Learn more about knowledge structure here
https://brainly.com/question/29022277
#SPJ11
please help me i will award brainliest
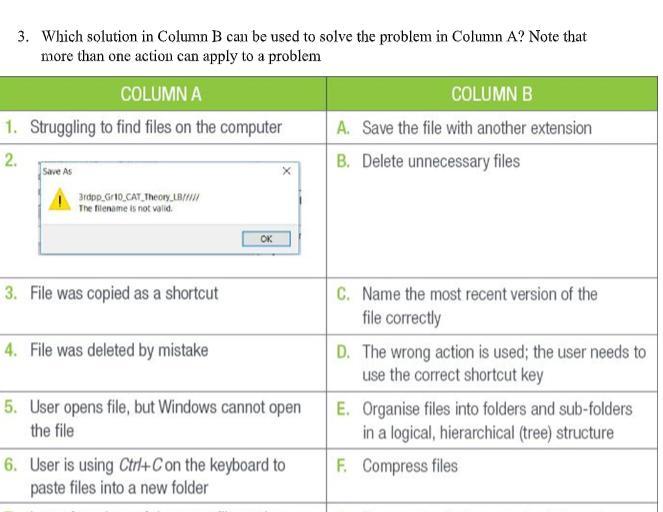

Answers
Answer: It would be option C.
Explanation: The file name is invalid, so therefore it would make sense to rename the most recent version correctly.
What is the keyboard shortcut for the Undo command?
Choose the answer.
CTRL+X
CTRL+Z
CTRL+U
CTRL+V
Answers
Answer:
CTRL+Z is Undo
Explanation:
CTRL+X: Cut
CTRL+Z: Undo
CTRL+U: Underline
CTRL+V: Paste
(ANWNER QUICK PLS) What attributes of color does the Luminosity blend mode affect?
You can use the Luminosity blend mode to match the brightness of the original color to the brightness of the new color.
and
are unaffected
Answers
The Luminosity blend mode affects the brightness and luminance of a color.
It is used to match the brightness of the original color to the brightness of the new color, while keeping the hue and saturation unaffected. This means that the Luminosity blend mode only affects the lightness of a color, and does not change the color itself. It is a useful tool for making adjustments to the brightness of an image without changing the overall color scheme.
Luminosity blend mode is a popular blending mode used in photo editing software such as Photoshop, GIMP, and Corel PaintShop Pro. It is used to match the brightness of the original color to the brightness of the new color, while preserving the hue and saturation of the original. To achieve this, the Luminosity blend mode looks at the color information in each channel and darkens the base color to reflect the blend color by decreasing the brightness.
Learn more about fusion Luminosity:
https://brainly.com/question/1401157
#SPJ11
The Luminosity blend mode affects the brightness and luminance of a color.
It is used to match the brightness of the original color to the brightness of the new color, while keeping the hue and saturation unaffected. This means that the Luminosity blend mode only affects the lightness of a color, and does not change the color itself. It is a useful tool for making adjustments to the brightness of an image without changing the overall color scheme.
Luminosity blend mode is a popular blending mode used in photo editing software such as Photoshop, GIMP, and Corel PaintShop Pro. It is used to match the brightness of the original color to the brightness of the new color, while preserving the hue and saturation of the original. To achieve this, the Luminosity blend mode looks at the color information in each channel and darkens the base color to reflect the blend color by decreasing the brightness.
Learn more about fusion Luminosity:
brainly.com/question/1401157
#SPJ11
monitor calibration is not enough to ensure total image accuracy through the process. a. evaluation b. manipulation c. output d. input
Answers
Monitor calibration is insufficient to guarantee complete image accuracy during output.
Why does the photograph usually go through the matting process before being framed?The mat, when used in a frame, prevents the picture from contacting and sticking to the glass. Matting can be completed totally with historical materials, unlike other presenting approaches, and it is simple to undo.
What justifications exist for matting an image?Artwork can be protected by matting. Unframed art can be handled by artists and collectors without really touching the piece thanks to a mat. A mat enables airflow between the artwork and the glazing substance.
To know more about output visit:-
https://brainly.com/question/14227929
#SPJ4
Write a program that reads text data from a file and generates the following:
A printed list (i.e., printed using print) of up to the 10 most frequent words in the file in descending order of frequency along with each word’s count in the file. The word and its count should be separated by a tab ("\t").
A plot like that shown above, that is, a log-log plot of word count versus word rank.
Answers
Here's a Python program that reads text data from a file and generates a printed list of up to the 10 most frequent words in the file, along with each word's count in the file, in descending order of frequency (separated by a tab). It also generates a log-log plot of word count versus word rank using Matplotlib.
```python
import matplotlib.pyplot as plt
from collections import Counter
# Read text data from file
with open('filename.txt', 'r') as f:
text = f.read()
# Split text into words and count their occurrences
word_counts = Counter(text.split())
# Print the top 10 most frequent words
for i, (word, count) in enumerate(word_counts.most_common(10)):
print(f"{i+1}. {word}\t{count}")
# Generate log-log plot of word count versus word rank
counts = list(word_counts.values())
counts.sort(reverse=True)
plt.loglog(range(1, len(counts)+1), counts)
plt.xlabel('Rank')
plt.ylabel('Count')
plt.show()
```
First, the program reads in the text data from a file named `filename.txt`. It then uses the `Counter` module from Python's standard library to count the occurrences of each word in the text. The program prints out the top 10 most frequent words, along with their counts, in descending order of frequency. Finally, the program generates a log-log plot of word count versus word rank using Matplotlib. The x-axis represents the rank of each word (i.e., the most frequent word has rank 1, the second most frequent word has rank 2, and so on), and the y-axis represents the count of each word. The resulting plot can help to visualize the distribution of word frequencies in the text.
Learn more about Python program here:
https://brainly.com/question/28691290
#SPJ11
The required program that generates the output described above is
```python
import matplotlib.pyplot as plt
from collections import Counter
# Read text data from file
with open('filename.txt', 'r') as f:
text = f.read()
# Split text into words and count their occurrences
word_counts = Counter(text.split())
# Print the top 10 most frequent words
for i, (word, count) in enumerate(word_counts.most_common(10)):
print(f"{i+1}. {word}\t{count}")
# Generate log-log plot of word count versus word rank
counts = list(word_counts.values())
counts.sort(reverse=True)
plt.loglog(range(1, len(counts)+1), counts)
plt.xlabel('Rank')
plt.ylabel('Count')
plt.show()
```
How does this work ?The code begins by reading text data from a file called 'filename.txt '. The 'Counter' module from Python's standard library is then used to count the occurrences of each word in the text.
In descending order of frequency, the software publishes the top ten most frequent terms, along with their counts. Finally, the program employs Matplotlib to build a log-log plot of word count vs word rank.
Learn more about Phyton:
https://brainly.com/question/26497128
#SPJ4