Write a Java Console application in which you initialize an arraylist with 10 string values. For example, 10 colour names, or fruit names, or car names. Display all the values in the list in a neat tabular format. Randomly select a value from the array. Now allow the user 3 chances to guess the value. After the first incorrect guess, provide the user with a clue i.e., the first letter of the randomly selected word. After the second incorrect guess, provide the user with another clue such as the number of letters in the word. When the user correctly guesses the word, remove that word from the list. Display the number of items remaining in the list. The user must have the option to play again.
Answers
Answer:
import java.util.ArrayList;
import java.util.Random;
import java.util.Scanner;
public class GuessTheCar {
public static void main(String[] args) {
ArrayList<String> cars = new ArrayList<>();
cars.add("Toyota");
cars.add("Honda");
cars.add("Chevrolet");
cars.add("BMW");
cars.add("Mercedes");
cars.add("Tesla");
cars.add("Ford");
cars.add("Audi");
cars.add("Porsche");
cars.add("Ferrari");
boolean play = true;
Scanner scanner = new Scanner(System.in);
while (play && cars.size() > 0) {
int randomIndex = new Random().nextInt(cars.size());
String randomCar = cars.get(randomIndex);
System.out.println("Car list:");
for (int i = 0; i < cars.size(); i++) {
System.out.printf("%d. %s\n", i + 1, cars.get(i));
}
System.out.println();
boolean correctGuess = false;
for (int i = 0; i < 3; i++) {
System.out.print("Guess the car name: ");
String guess = scanner.nextLine();
if (guess.equalsIgnoreCase(randomCar)) {
correctGuess = true;
break;
} else if (i == 0) {
System.out.printf("Clue: The car name starts with '%s'.\n", randomCar.charAt(0));
} else if (i == 1) {
System.out.printf("Clue: The car name has %d letters.\n", randomCar.length());
}
}
if (correctGuess) {
System.out.println("Congratulations! You guessed correctly!");
cars.remove(randomCar);
} else {
System.out.println("Sorry, you didn't guess the car correctly. The car was " + randomCar + ".");
}
System.out.printf("Cars remaining: %d\n", cars.size());
System.out.print("Do you want to play again? (Y/N): ");
String response = scanner.nextLine();
play = response.equalsIgnoreCase("Y");
}
scanner.close();
System.out.println("Thanks for playing!");
}
}
Here's an example of a Java console application that implements the described functionality:
java
Copy code
import java.util.ArrayList;
import java.util.List;
import java.util.Random;
import java.util.Scanner;
private static final int MAX_GUESSES = 3;
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
List<String> wordList = initializeWordList(); // Initialize the word list
do {
playGame(scanner, wordList); // Play the game
System.out.print("Do you want to play again? (y/n): ");
} while (scanner.nextLine().equalsIgnoreCase("y"));
System.out.println("Thanks for playing!");
}
private static List<String> initializeWordList() {
List<String> wordList = new ArrayList<>();
// Add 10 words to the list
wordList.add("apple");
wordList.add("banana");
wordList.add("orange");
wordList.add("strawberry");
wordList.add("watermelon");
wordList.add("kiwi");
wordList.add("mango");
wordList.add("grape");
wordList.add("pineapple");
wordList.add("pear");
return wordList;
}
private static void playGame(Scanner scanner, List<String> wordList) {
System.out.println("=== Guessing Game ===");
// Select a random word from the list
Random random = new Random();
int randomIndex = random.nextInt(wordList.size());
String randomWord = wordList.get(randomIndex);
int remainingGuesses = MAX_GUESSES;
boolean wordGuessed = false;
while (remainingGuesses > 0 && !wordGuessed) {
System.out.println("Guess the word (remaining guesses: " + remainingGuesses + "):");
String guess = scanner.nextLine();
if (guess.equalsIgnoreCase(randomWord)) {
wordGuessed = true;
System.out.println("Congratulations! You guessed it right.");
} else {
remainingGuesses--;
if (remainingGuesses > 0) {
if (remainingGuesses == 2) {
System.out.println("Incorrect guess. Here's a clue: First letter of the word is '" +
randomWord.charAt(0) + "'.");
} else if (remainingGuesses == 1) {
System.out.println("Incorrect guess. Here's another clue: The word has " +
randomWord.length() + " letters.");
}
System.out.println("Try again!");
} else {
System.out.println("Sorry, you're out of guesses. The word was '" + randomWord + "'.");
}
}
}
if (wordGuessed) {
wordList.remove(randomWord);
}
System.out.println("Number of items remaining in the list: " + wordList.size());
}
}
This program initializes an ArrayList with 10 words, allows the user to play the guessing game, and provides clues after incorrect guesses. After the game ends, it prompts the user to play again or exit.
Please note that this implementation assumes you have basic knowledge of Java programming and how to run a Java console application.
Learn more about Java programming on:
https://brainly.com/question/30613605
#SPJ1
Related Questions
A LinkedIn profile is required to be able to share your work experience and qualifications with potential employers.
True
False
Answers
Answer:
False
Explanation:
A LinkedIn profile is not required.
24. Which of the following statements about Emergency Support Functions (ESFs) is correct?
O A. ESFs are not exclusively federal coordinating mechanism
O B. ESFs are only a state or local coordinating mechanism
O C. ESFs are exclusively a federal coordinating mechanism
O D. ESFs are exclusively a state coordinating mechanism
Answers
(ESFs) is correct: ESFs are not exclusively federal coordinating mechanism.
10
80 remo
9.0 25 alls
b0o* -a
*2
x 20
90x2 = 180
.
ec - = 42
",
nc - 42
90-42
x=48
3
luate
Solution
Assignment
the following ett Statement clearly
clearly showing your
I regt 3+32 lish - 2 +12 ts 2-9/3
I b=12+4 +976 412/3
Ghow the steps of
your
mathematical equati
(=Programy
Integer
.
ett
3
as
osters
Answers
Answer:
i need more \\
Explanation:
Chemical cold packs should be used for bone and joint injuries because they are generally colder than ice and stay cold longer.
A.
True
B.
False
Reset
Files can be stored on hard drives, network drives, or external drives, but not in the cloud.
True
False
Folders provide a method for organizing files.
True
False
Answers
Answer: (1) False, (2) True
Explanation:
children and texhnology
Answers
Answer: technology better
Explanation:
Without using parentheses, enter a formula in C4 that determines projected take home pay. The value in C4, adding the value in C4 multiplied by D4, then subtracting E4.
HELP!
Answers
Parentheses, which are heavy punctuation, tend to make reading prose slower. Additionally, they briefly divert the reader from the core idea and grammatical consistency of the sentence.
What are the effect of Without using parentheses?When a function is called within parenthesis, it is executed and the result is returned to the callable. In another instance, a function reference rather than the actual function is passed to the callable when we call a function without parenthesis.
Therefore, The information inserted between parenthesis, known as parenthetical material, may consist of a single word, a sentence fragment, or several whole phrases.
Learn more about parentheses here:
https://brainly.com/question/26272859
#SPJ1
Starting at time 0, a new process p of length 3 arrives every 4 time units. Starting at time 1, a new process q of length 1 arrives every 4 time units. Determine the ATT under FIFO, SJF, and SRT.
Answers
Answer:
A.T= Arrival Time B.T= Burst Time C.T= Completion Time T.T = Turn around Time = C.T - A.T W.T = Waiting Time = T.T - B.T ATT=sum of all Turn-around time / total no of process FIFO (first in first o
Please help its timed! Which of the following is an event? Select 4 options. adding three and four in a program. moving a mouse. clicking a mouse button. a sensor detecting the motion of an earthquake detector. scanning a credit card when you shop?
Answers
The option that is an event is known to be clicking a mouse button.
What is a computer event?An event, in a computing context, is known to be any kind of action that aim to know or is identified by a program and has a good importance for system hardware or software.
Events examples keystrokes and mouse clicks, program loading and others. so we can say that the option that is an event is known to be clicking a mouse button.
Learn more about program from
https://brainly.com/question/1538272
#SPJ1
how to configure the network connectivity in your computer
Answers
Answer:
Click the Start button, and then click Control Panel. In the Control Panel window, click Network and Internet. In the Network and Internet window, click Network and Sharing Center. In the Network and Sharing Center window, under Change your networking settings, click Set up a new connection or network
Explanation:
"our account has been moderated because one or more of the charges on the account were reported as unauthorized or disputed by the billing account holder". what notification is this?
Answers
This notification means that your account has been moderated because one or more of the charges on the account were reported as unauthorized or disputed by the billing account holder.
If you receive this notification, it means that your account has been moderated because one or more of the charges on the account were reported as unauthorized or disputed by the billing account holder.
This can happen if you make a charge that the account holder does not recognize, or if there is a dispute about a charge. If this happens, you will need to contact the billing account holder to resolve the issue.
For more questions like Notification click the link below:
https://brainly.com/question/6199558
#SPJ4
Explain what it means when industry leaders indicate that they are moving their organization from knowledge-centered support to knowledge-centered service. Also describe some of the implications for this movement towards knowledge centered service. What are some of the struggles employees may face?
Answers
Organizational support teams may find it difficult to keep up, but Knowledge Centered Service is changing that. Knowledge is emphasized as a crucial asset for providing service and support in the knowledge-centered service model, or KCS
What are some of the benefits of using KCS methodology?Businesses that employ KCS methodology discover that it offers a variety of advantages. It gradually enhances customer satisfaction, lowers employee turnover, and shortens the time required for new hires to complete their training. Ursa Major is working to set up a program with these features in order to achieve those benefits.The goal of the content standard is to formally document or use a template that outlines the choices that must be made regarding the structure and content of KCS articles in order to promote consistency. KCS articles come in two varieties: - Close the loop since articles are produced in response to customer demand.Digital is a way of life in the twenty-first century, particularly inside any business or organization. It seems that support functions can hardly keep up with the significant changes in innovation and productivity. Now that technical support is a daily part of customer interactions, it is no longer the internal, back-office division that customers never saw. Organizational support teams may find it difficult to keep up, but Knowledge Centered Service is changing that.To learn more about KCS methodology refer to:
https://brainly.com/question/28656413
#SPJ1
9. A change in the appearance of a value or label in a cell
a) Alteration
b) Format
c) Indentation
d) Design
10. The placement of information within a cell at the left edge, right ed
a) Indentation
b) Placement
c) Identification
d) Alignment
11. Spreadsheet can be best classified as
a) Word
b) Database
c) Excel
d) Outlook
12. Formulas in Excel start with
Answers
Answer:
format
alignment
excel
=
Explanation: i'm an accountant
A change in the appearance of a value or label in a cell is format. The placement of information within a cell at the left edge, right edge is alignment, and spreadsheet can be best classified as Excel. The correct options are b, d, and c respectively.
What exactly does a spreadsheet mean?A spreadsheet, also known as an electronic work sheet, is a computer program that organizes data into graph-like rows and columns. Formulas, commands, and formats can be used to manipulate each row and column.
Spreadsheets are most commonly used to store and organize data such as revenue, payroll, and accounting information. Spreadsheets allow the user to perform calculations on the data and generate graphs and charts.
Format is a change in the appearance of a value or label in a cell. The alignment of information within a cell at the left edge, the alignment of information within a cell at the right edge, as well as spreadsheets are usually best classified as Excel.
Thus, b, d, and c respectively are correct options.
For more details regarding spreadsheet, visit:
https://brainly.com/question/8284022
#SPJ6
What would game programmers do when decomposing a task in a modular program?
Answers
1. Identify the overall task or feature: Game programmers start by identifying the larger task or feature they want to implement, such as player movement, enemy AI, or collision detection.
2. Analyze the task: They analyze the task to understand its requirements, inputs, and desired outputs. This helps them determine the necessary functionality and behavior.
3. Identify subtasks or components: They identify the subtasks or components that make up the larger task. For example, in the case of player movement, this could involve input handling, character animation, physics simulation, and rendering.
4. Break down the subtasks further: Each subtask can be further decomposed into smaller, more specific functions or modules. For example, input handling might involve separate functions for keyboard input, mouse input, or touch input.
5. Define interfaces: They define clear interfaces between the modules, specifying how they interact and communicate with each other. This helps ensure modularity and maintainability of the code.
6. Implement and test modules: Game programmers then proceed to implement each module or function, focusing on their specific responsibilities. They can test and iterate on these smaller units of functionality independently.
7. Integrate and test the modules: Finally, they integrate the modules together, ensuring they work harmoniously and produce the desired outcome. Thorough testing is conducted to verify that the overall task or feature functions correctly.
By decomposing tasks in this manner, game programmers can effectively manage the complexity of game development, promote code reusability, enhance collaboration, and facilitate the maintenance and future expansion of the game.
When decomposing a task in a modular program, game programmers follow a structured approach to break down the task into smaller, more manageable components.
This process is crucial for code organization, maintainability, and reusability. Here's an outline of what game programmers typically do:
1. Identify the task: The programmer begins by understanding the task at hand, whether it's implementing a specific game feature, optimizing performance, or fixing a bug.
2. Break it down: The task is broken down into smaller subtasks or functions that can be handled independently. Each subtask focuses on a specific aspect of the overall goal.
3. Determine dependencies: The programmer analyzes the dependencies between different subtasks and identifies any order or logical flow required.
4. Design modules: Modules are created for each subtask, encapsulating related code and functionality. These modules should have well-defined interfaces and be independent of each other to ensure reusability.
5. Implement and test: The programmer then implements the modules by writing the necessary code and tests their functionality to ensure they work correctly.
6. Integrate modules: Once individual modules are tested and verified, they are integrated into the larger game program, ensuring that they work together seamlessly.
By decomposing tasks into modules, game programmers promote code organization, readability, and ease of maintenance. It also enables parallel development by allowing different team members to work on separate modules simultaneously, fostering efficient collaboration.
For more such questions on programmers,click on
https://brainly.com/question/30130277
#SPJ8
Make sure your animal_list.py program prints the following things, in this order:
The list of animals 1.0
The number of animals in the list 1.0
The number of dogs in the list 1.0
The list reversed 1.0
The list sorted alphabetically 1.0
The list of animals with “bear” added to the end 1.0
The list of animals with “lion” added at the beginning 1.0
The list of animals after “elephant” is removed 1.0
The bear being removed, and the list of animals with "bear" removed 1.0
The lion being removed, and the list of animals with "lion" removed
Need the code promise brainliest plus 100 points
Answers
Answer:#Animal List animals = ["monkey","dog","cat","elephant","armadillo"]print("These are the animals in the:\n",animals)print("The number of animals in the list:\n", len(animals))print("The number of dogs in the list:\n",animals.count("dog"))animals.reverse()print("The list reversed:\n",animals)animals.sort()print("Here's the list sorted alphabetically:\n",animals)animals.append("bear")print("The new list of animals:\n",animals)
Explanation:
Question 4
Fill in the blank to complete the “increments” function. This function should use a list comprehension to create a list of numbers incremented by 2 (n+2). The function receives two variables and should return a list of incremented consecutive numbers between “start” and “end” inclusively (meaning the range should include both the “start” and “end” values). Complete the list comprehension in this function so that input like “squares(2, 3)” will produce the output “[4, 5]”.
Answers
The increment function will be written thus:
ef increments(start, end):
return [num + 2 for num in range(start, end + 1)]
print(increments(2, 3)) # Should print [4, 5]
print(increments(1, 5)) # Should print [3, 4, 5, 6, 7]
print(increments(0, 10)) # Should print [2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12]
How to explain the functionThe increments function takes two arguments, start and end, which represent the inclusive range of numbers to be incremented.
The goal is to create a list of numbers incremented by 2 (n+2) using a list comprehension.
Learn more about functions on
https://brainly.com/question/10439235
#SPJ1
You received an email message stating that your mother's bank account is going to be forfeited if you do not respond to the email. Is it safe to reply?Why?
It's a scenario<3
Answers
Answer:
No.
Explanation:
I'm almost certain it's a scam. Banks generally don't use emails to contact clients. They use telephones and paper correspondence. If they contact you by email it is because they have no other way of getting in touch with you because you have changed your address and your phone, etc..
A company that wants to send data over the Internet has asked you to write a program that will encrypt it so that it may be transmitted more securely. All the data is transmitted as four-digit integers. Your app should read a four-digit integer entered by the user and encrypt it as follows: Replace each digit with the result of adding 7 to the digit and getting the remainder after dividing the new value by 10. Then swap the first digit with the third, and swap the second digit with the fourth. Then display the encrypted integer. Write a separate app that inputs an encrypted four-digit integer and decrypts it (by reversing the encryption scheme) to form the original number. Use the format specifier D4 to display the encrypted value in case the number starts with a 0
Answers
Answer:
The output of the code:
Enter a 4 digit integer : 1 2 3 4
The decrypted number is : 0 1 8 9
The original number is : 1 2 3 4
Explanation:
Okay, the code will be written in Java(programming language) and the file must be saved as "Encryption.java."
Here is the code, you can just copy and paste the code;
import java.util.Scanner;
public class Encryption {
public static String encrypt(String number) {
int arr[] = new int[4];
for(int i=0;i<4;i++) {
char ch = number.charAt(i);
arr[i] = Character.getNumericValue(ch);
}
for(int i=0;i<4;i++) {
int temp = arr[i] ;
temp += 7 ;
temp = temp % 10 ;
arr[i] = temp ;
}
int temp = arr[0];
arr[0] = arr[2];
arr[2]= temp ;
temp = arr[1];
arr[1] =arr[3];
arr[3] = temp ;
int newNumber = 0 ;
for(int i=0;i<4;i++)
newNumber = newNumber * 10 + arr[i];
String output = Integer.toString(newNumber);
if(arr[0]==0)
output = "0"+output;
return output;
}
public static String decrypt(String number) {
int arr[] = new int[4];
for(int i=0;i<4;i++) {
char ch = number.charAt(i);
arr[i] = Character.getNumericValue(ch);
}
int temp = arr[0];
arr[0]=arr[2];
arr[2]=temp;
temp = arr[1];
arr[1]=arr[3];
arr[3]=temp;
for(int i=0;i<4;i++) {
int digit = arr[i];
switch(digit) {
case 0:
arr[i] = 3;
break;
case 1:
arr[i] = 4;
break;
case 2:
arr[i] = 5;
break;
case 3:
arr[i] = 6;
break;
case 4:
arr[i] = 7;
break;
case 5:
arr[i] = 8;
break;
case 6:
arr[i] = 9;
break;
case 7:
arr[i] = 0;
break;
case 8:
arr[i] = 1;
break;
case 9:
arr[i] = 2;
break;
}
}
int newNumber = 0 ;
for(int i=0;i<4;i++)
newNumber = newNumber * 10 + arr[i];
String output = Integer.toString(newNumber);
if(arr[0]==0)
output = "0"+output;
return output;
}
public static void main(String[] args) {
Scanner sc = new Scanner(System.in);
System.out.print("Enter a 4 digit integer:");
String number = sc.nextLine();
String encryptedNumber = encrypt(number);
System.out.println("The decrypted number is:"+encryptedNumber);
System.out.println("The original number is:"+decrypt(encryptedNumber));
}
}
Which tool adds different amazing effects to a picture.
(a) Paint
(b) Lines tool
(c) Magic tool
Answers
Answer:
magic tool
Explanation:
Write a statement using a compound assignment operator to cut the value of pay in half (pay is an integer variable that has already been declared and initialized). C++
Answers

Assignment
Write a assembly program that can display the following shapes:
Rectangle
Triangle
Diamond
The program will read an input from the user. The input is terminated with a period. So the program will continue to run until a period is read.
The data the program reads is as follows:
A shape command followed by parameters.
R stands for Rectangle. The parameters are height (rows) and width (columns)
T stands for Triangle. The parameters is base width
D stands for Diamond. The parameters
Your program needs to read the input and based on the input do the following:
Print your name
Then print the name of the shape
Then the shape below it.
Sample input:
R 03 10
T 05
D 11
.
Output:
Loay Alnaji
Rectangle
**********
**********
**********
Triangle
*
***
*****
Diamond
*
***
*****
*******
*********
***********
*********
*******
*****
***
*
Requirements
Your main should only be the driver. It should only read the "shape type", based on that, call the proper function to read the parameters and draw the shape.
Example of your main (just example, pseudocode):
loop:
read shape
if shape is '.' then exit
if shape is 'R'
call Rectangle Function
if shape is 'D'
call Diamond Function
if shape is 'T'
Call Triangle Function
go to loop
Answers
The program above is one that begins with the _begin name, which is the passage point of the program.
What is the program about?The program uses framework call int 0x80 to print your title on the screen utilizing the compose framework call. It loads the suitable values into the registers (eax, ebx, ecx, edx) to indicate the framework call number, record descriptor, buffer address (where the title is put away), and length of the title.
It checks in case the shape input may be a period (.), which demonstrates the conclusion of input. In case so, it bounced to the exit name to exit the program.
Learn more about program from
https://brainly.com/question/23275071
#SPJ1



Which of the following would be considered software? Select 2 options.
memory
printer
operating system
central processing unit (CPU)
Microsoft Office suite (Word, Excel, PowerPoint, etc.)
Thing
Answers
Answer:
Microsoft Office suite (Word, Excel, PowerPoint, etc.), and thing
Explanation:
The Operating system and Microsoft Office suite will be considered as software.
A Software is the opposite of Hardware in a computer system.
Let understand that Software means some set of instructions or programs on a computer which are used for operation and execution of specific tasks.There are different type of software and they include:
Application Software are software installed into the system to perform function on the computer E.g. Chrome.System Software is the software designed to provide platform for other software installed on the computer. Eg. Microsoft OS. Firmware refers to set of instructions programmed on a hardware device such as External CD Rom.In conclusion, the Operating system is a system software while the Microsoft Office suite is an application software.
Learn more about Software here
brainly.com/question/1022352
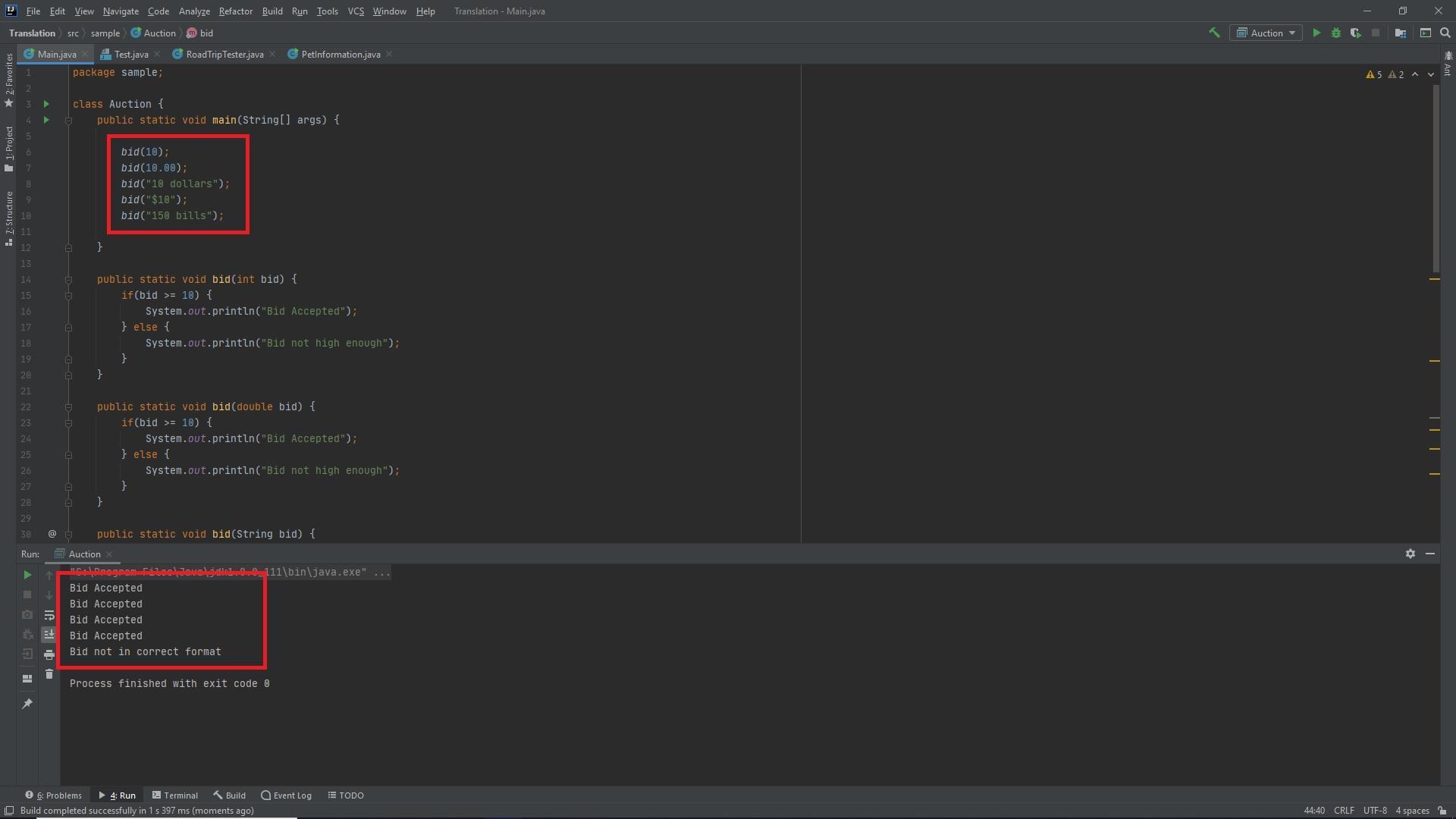
Create a program named Auction that allows a user to enter an amount bid on an online auction item. Include three overloaded methods that accept an int, double, or string bid. Each method should display the bid and indicate whether it is over the minimum acceptable bid of $10. If the bid is greater than or equal to $10, display Bid accepted. If the bid is less than $10, display Bid not high enough. If the bid is a string, accept it only if one of the following is true: It is numeric and preceded with a dollar sign. It is numeric and followed by the word dollars. Otherwise, display a message that says Bid was not in correct format. Grading When you have completed your program, click the Submit button to record your score.
Answers
Answer:
Explanation:
The following code is written in Java and creates the overloaded methods as requested. It has been tested and is working without bugs. The test cases are shown in the first red square within the main method and the output results are shown in the bottom red square...
class Auction {
public static void main(String[] args) {
bid(10);
bid(10.00);
bid("10 dollars");
bid("$10");
bid("150 bills");
}
public static void bid(int bid) {
if(bid >= 10) {
System.out.println("Bid Accepted");
} else {
System.out.println("Bid not high enough");
}
}
public static void bid(double bid) {
if(bid >= 10) {
System.out.println("Bid Accepted");
} else {
System.out.println("Bid not high enough");
}
}
public static void bid(String bid) {
if (bid.charAt(0) == '$') {
if (Integer.parseInt(bid.substring(1, bid.length())) > 0) {
System.out.println("Bid Accepted");
return;
} else {
System.out.println("Bid not in correct Format");
return;
}
}
int dollarStartingPoint = 0;
for (int x = 0; x < bid.length(); x++) {
if (bid.charAt(x) == 'd') {
if (bid.substring(x, x + 7).equals("dollars")) {
dollarStartingPoint = x;
} else {
break;
}
}
}
if (dollarStartingPoint > 1) {
if (Integer.parseInt(bid.substring(0, dollarStartingPoint-1)) > 0) {
System.out.println("Bid Accepted");
return;
} else {
System.out.println("Bid not in correct format");
return;
}
} else {
System.out.println("Bid not in correct format");
return;
}
}
}
How does one take personal responsibility when choosing healthy eating options? Select three options.
1 create a log of what one eats each day
2 increase one’s consumption of fast food
3 critique one’s diet for overall balance of key nutrients
4 identify personal barriers that prevent an individual from making poor food choices
5 eat only what is shown on television advertisements
Answers
The three options to a healthier eating culture are:
create a log of what one eats each daycritique one’s diet for overall balance of key nutrientsidentify personal barriers that prevent an individual from making poor food choicesHow can this help?Create a log of what one eats each day: By keeping track of what you eat, you become more aware of your eating habits and can identify areas where you may need to make changes. This can also help you to monitor your intake of certain nutrients, and ensure that you are getting enough of what your body needs.
Critique one’s diet for overall balance of key nutrients: A balanced diet should include a variety of foods from different food groups. By assessing your diet, you can determine whether you are consuming enough fruits, vegetables, whole grains, lean proteins, and healthy fats. If you find that you are lacking in any of these areas, you can adjust your eating habits accordingly.
Read more about healthy eating here:
https://brainly.com/question/30288452
#SPJ1
Your professor is advising a new crowd-funding app for women's self-help groups (SHGs) in Latin America on their database architecture. This is the business requirement she has worked on: All campaigns belong to a SHG. An SHG must exist before a campaign is created, and when an SHG is deleted from the database, all its campaigns are deleted. SHGs always belong to a country, and a country must be added to the app before SHGs are added to it. Which of the following is true of the entities defined in the database? Select all that apply.
Question 6 options:
An SHG entity depends on a Campaign entity
A Campaign entity is a depend on the SHG entity
A Country is not dependent on the Campaign entity
An SHG entity is dependent on a Country entity
A Campaign is an Independent entity
Answers
Based on the given information, the following statements are true:
An SHG entity depends on a Country entity.A Campaign entity is dependent on the SHG entity.What is a country entity?In the context of database design, a country entity refers to a logical representation of a country within a database system.
It typically stores information related to countries, such as their names, codes, demographics, or any other relevant data.
The country entity serves as a reference point for other entities in the database, such as self-help groups (SHGs) or campaigns, allowing for proper organization and association of data within the system.
Learn more about Entity at:
https://brainly.com/question/29491576
#SPJ1
Drag the tiles to the correct boxes to complete the pairs. Match each role to the corresponding web development task.
1.creating budget spreadsheets 2.researching target audiences
3.selecting color palettes
4.coding
A. art director
B. web project manager
C. usability lead
D. developer
Answers
The matching of each role to the corresponding web development task is as follows:
Art director: selecting color palettes.Web project manager: creating budget spreadsheets.Usability lead: researching target audiences.Developer: coding.What is a Web development task?Web development tasks may be characterized as the tasks that are directly associated with developing websites for hosting via intranet or internet. The web development methodology may include web design, web content development, client-side/server-side scripting, and network security configuration, among other tasks.
The various role performed during the web development process (task) includes art director, web project manager, usability lead, developer, etc. All these roles have to perform specific responsibilities in the overall process.
Therefore, the matching of each role to the corresponding web development task is well described above.
To learn more about Web development, refer to the link:
https://brainly.com/question/29554914
#SPJ1
state and explain application areas where computer are applied
Answers
Answer:
There are at least five areas that are covered by computer applications, and five of those are business, government, military, manufacturing, and music. There are also other areas such as scientific and the role of technology in our society is growing annually.
Computers have now for several decades brought automation to the table in small, medium, and large businesses. There are word processing and spreadsheet applications for small businesses all the way up to enterprise-wide applications that cover every aspect of a large business such as accounting, inventory, shop floor, management, and feature real-time reporting capability that can give a snapshot glimpse of the financial position of a company at any point in time.
The government has a wide variety of computer applications. Government uses many of the same tools as small to large businesses in desktop type applications and many that are much more advanced that are used in the military. Manufacturing applications involve computer-aided design and applications that are used to track production from the time a raw material is moved into the warehouse all the way to the production floor and back into the warehouse as a finished good.
Military only applications include systems that use GPS in missiles to hone in on targets from miles away. There are all kinds of other applications some of which are secret in nature and the public does not become aware of these until a war is underway. Computer applications in music can help to transcribe and compose music as well as provide accompaniment for a musician to practice with.
Expect the number of computer applications in all of these fields to become more common in the future. Expect many applications to take the place of people to save money in a cash-crunched economy where everyone is looking for more ways to save money and cut costs.
Explanation:
Summary
In this lab, you add a loop and the statements that make up the loop body to a C++ program that is provided. When completed, the program should calculate two totals: the number of left-handed people and the number of right-handed people in your class. Your loop should execute until the user enters the character X instead of L for left-handed or R for right-handed.
The inputs for this program are as follows: R, R, R, L, L, L, R, L, R, R, L, X
Variables have been declared for you, and the input and output statements have been written.
Instructions
Ensure the source code file named LeftOrRight.cpp is open in the code editor.
Write a loop and a loop body that allows you to calculate a total of left-handed and right-handed people in your class.
Execute the program by clicking the Run button and using the data listed above and verify that the output is correct.
Answers
The loop on the statement regarding the program is illustrated below.
How to illustrate the loop?A loop is used to repeatedly execute a specific block of code. For loops and while loops are the two major forms of loops.
A loop is a set of instructions in computer programming that is repeatedly repeated until a given condition is met. Typically, a process is performed, such as retrieving and modifying data, and then a condition is verified, such as whether a counter has reached a predetermined number.
This will be:
// LeftOrRight.cpp - This program calculates the total number of
//left-handed and right-handed
// students in a class.
// Input: L for left-handed; R for right handed; X to quit.
// Output: Prints the number of left-handed students
//and the number of right-handed students.
#include <iostream>
#include <string>
using namespace std;
int main()
{
// L or R for one student.
string leftOrRight = "";
// Number of right-handed students.
int rightTotal = 0;
// Number of left-handed students.
int leftTotal = 0;
// This is the work done in the housekeeping() function
cout << "Enter an L if you are left-handed, a R if you are right-handed or X to quit: ";
cin >> leftOrRight;
//Use while loop repeat the loop until X is found
while (leftOrRight != "X")
{
//if the above input is R increment
//rightTotal by 1
if (leftOrRight == "R")
rightTotal++;
//if the above input is L increment
//leftTotal by 1
else if (leftOrRight == "L")
leftTotal++;
//read the move again
cin >> leftOrRight;
}
// This is the work done in the detailLoop() function
// Write your loop here.
// This is the work done in the endOfJob() function
// Output number of left or right-handed students.
cout << "Number of left-handed students: " << leftTotal << endl;
cout << "Number of right-handed students: " << rightTotal << endl;
return 0;
}
Learn more about loop on:
https://brainly.com/question/16922594
#SPJ1
Additional rows and columns are inserted into a table using the
tab.
o Table Tools Design
o Insert Table
o Table Tools Layout
o Table Tools Insert
Answers
Do the binary numbers 0011 and 000011 have the same or different values? Explain
Answers
Answer:
system has two symbols: 0 and 1 , called bits. ... 0011 0100 0011 0001 1101 0001 1000 B , which is the same as hexadecimal B343 1D18H ) ... Example 1: Suppose that n=8 and the binary pattern is 0100 0001 B , the value of this unsigned integer is 1×2^0 ... An n-bit pattern can represent 2^n distinct integers.
Explanation:
Using binary to decimal conversions, it is found that the answer is that the binary numbers 0011 and 000011 have the same values.
--------------------------
Here, conversion between binary and decimal is explained, which are used to find the answer.
The conversion starts from the last bits, that is, the least significant bits.As the conversion gets closer to the first bit, that is, the most significant bit, the weight of 2, that is, the exponent increases, as we are going to see.--------------------------
The conversion of 0011 to decimal is:
\((0011)_2 = 1 \times 2^0 + 1 \times 2^1 + 0 \times 2^2 + 0 \times 2^3 = 1 + 2 + 0 + 0 = 3\)
--------------------------
The conversion of 000011 to decimal is:
\((000011)_2 = 1 \times 2^0 + 1 \times 2^1 + 0 \times 2^2 + 0 \times 2^3 + 0 \times 2^4 + 0 \times 2^5 = 1 + 2 + 0 + 0 + 0 + 0 = 3\)
In both cases, the decimal equivalent is 3, thus, they represent the same value.
A similar problem is given at https://brainly.com/question/7978210
You have a new computer placed on your desk. The computer consists of the CPU case, a monitor, a keyboard, and a mouse. The CPU case has indicator lights for power and for the hard disk. You press the power switch on the CPU case. The power light comes on. You hear noises coming from the CPU case, and the hard disk light blinks on and off several times. After a couple of minutes, the noises and blinking disk light stop. You hear a soft sound like a fan running, but you can't hear anything else. The screen has been totally blank during the entire process.
What is the most likely reason the screen is blank?
A. The monitor is not turned on.
B. The CPU power supply is not working.
C. The computer is not on.
D. The keyboard is not connected.
Answers
The most likely reason the screen is blank is A. The monitor is not turned on.
What is Troubleshooting?Troubleshooting is a type of problem resolution that is frequently used to fix broken components or operations on a machine or a system.
In order to address an issue and get the product or process back in operation, a logical, methodical search for the problem's source is required. It takes troubleshooting to find the symptoms.
Hence, it is stated that there is the power light on in the CPU, but the screen is blank and hence, the conclusion here is that the monitor is not turned on.
Read more about troubleshooting here:
https://brainly.com/question/26350093
#SPJ1