Write a program that reads a file containing Java source code. Your program should parse for proper nesting of {}()[]. That is, there should be an equal number of { and }, ( and ), and [ and ]. You can think of { as opening a scope, } as closing it. Similarly, [ to open and ] to close, and ( to open and ) to close. You want to see (determine) if the analyzed file has:
1. A proper pairing of { }, [], ().
2. That the scopes are opened and closed in a LIFO (Last in First out) fashion.
3. Your program should display improper nesting to the console, and you may have your program stop on the first occurrence of improper nesting.
4. Your program should prompt for a file – do NOT hard code the file to be processed. (You can prompt either via the console or via a file picker dialog).
5. You do not need to worry about () {} [] occurrences within comments or as literals, e.g. the occurrence of ‘[‘ within a program.
6. Your video should show the processing of a file that is correct and a file that has improper scoping
Please implement it using JAVA
Answers
Here's an example Java program that reads a file containing Java source code and checks for proper nesting of `{}`, `[]`, and `()`:
```java
import java.io.BufferedReader;
import java.io.FileReader;
import java.io.IOException;
import java.util.Stack;
public class NestingChecker {
public static void main(String[] args) {
try (BufferedReader reader = new BufferedReader(new FileReader("input.java"))) {
String line;
int lineNumber = 1;
Stack<Character> stack = new Stack<>();
while ((line = reader.readLine()) != null) {
for (char ch : line.toCharArray()) {
if (ch == '{' || ch == '[' || ch == '(') {
stack.push(ch);
} else if (ch == '}' || ch == ']' || ch == ')') {
if (stack.isEmpty()) {
System.out.println("Improper nesting at line " + lineNumber + ": Extra closing " + ch);
return;
}
char opening = stack.pop();
if ((opening == '{' && ch != '}') ||
(opening == '[' && ch != ']') ||
(opening == '(' && ch != ')')) {
System.out.println("Improper nesting at line " + lineNumber + ": Expected " + getClosing(opening) + " but found " + ch);
return;
}
}
}
lineNumber++;
}
if (!stack.isEmpty()) {
char opening = stack.pop();
System.out.println("Improper nesting: Missing closing " + getClosing(opening));
} else {
System.out.println("Proper nesting: All scopes are properly opened and closed.");
}
} catch (IOException e) {
System.out.println("Error reading file: " + e.getMessage());
}
}
private static char getClosing(char opening) {
if (opening == '{') return '}';
if (opening == '[') return ']';
if (opening == '(') return ')';
return '\0'; // Invalid opening character
}
}
```
Here's how the program works:
1. The program prompts for a file named "input.java" to be processed. You can modify the file name or use a file picker dialog to choose the file dynamically.
2. The program reads the file line by line and checks each character for `{`, `}`, `[`, `]`, `(`, `)`.
3. If an opening symbol (`{`, `[`, `(`) is encountered, it is pushed onto the stack.
4. If a closing symbol (`}`, `]`, `)`) is encountered, it is compared with the top of the stack. If they match, the opening symbol is popped from the stack. If they don't match, improper nesting is detected.
5. At the end, if the stack is not empty, it means there are unmatched opening symbols, indicating improper nesting.
6. The program displays appropriate messages for proper or improper nesting.
You can run this program by saving it as a Java file (e.g., `NestingChecker.java`) and executing it using a Java compiler and runtime environment.
Make sure to replace `"input.java"` with the actual file name or modify the code to prompt for the file dynamically.
Note that this program assumes that the file contains valid Java source code and does not consider occurrences within comments or literals.
Learn more about Java
brainly.com/question/33208576
#SPJ11
Related Questions
which keyword instructs the computer to skip to the next line after a loop?
Answers
The keyword that instructs the computer to skip to the next line after a loop is the "continue" statement. A "continue" statement is used to control the execution of a loop in computer programming languages. It is utilized to bypass certain sections of the loop and move to the next iteration without executing the remaining code in the loop.
A "continue" statement is used to move the control to the next iteration of the loop and skip the remaining instructions in the current loop iteration. When the program comes across the "continue" statement in a loop, it will ignore any remaining code in the current iteration and proceed to the next iteration.
A "continue" statement is frequently used in loops to skip certain iterations based on specific conditions. When a condition is met, a "continue" statement can be employed to bypass the rest of the code in the current iteration and proceed to the next iteration. The "continue" statement can be used in both for and while loops and is an essential element of loop control statements in programming.
To know more about loop visit:
https://brainly.com/question/31915192
#SPJ11
List four types of Web browsers
Answers
Answer:
internet explorer safari tor firefox
Explanation:
lindsay plans to give her audience a handout with images of her powerpoint slides. lindsay should distribute this handout after her presentation to maintain audience control. True or False
Answers
False. Lindsay should distribute the handout before or during her presentation to enhance audience engagement and comprehension.
The statement is false. Lindsay should distribute the handout before or during her presentation, rather than after, to maximize audience engagement and comprehension. Providing handouts beforehand allows the audience to follow along with the content and take notes, which can enhance their understanding and retention of the material. By having the slides in front of them, the audience can reference the information easily and stay focused on the presentation.
Distributing handouts after the presentation can lead to potential distractions and may hinder audience control. If the handouts contain detailed information, the audience might be tempted to read through the material instead of paying attention to Lindsay's delivery. Additionally, distributing handouts at the end may limit the opportunity for the audience to ask questions or seek clarification during the presentation.
Finally, giving handouts before or during the presentation is more effective for maintaining audience control and maximizing engagement. It allows the audience to actively participate, take notes, and refer to the slides as Lindsay presents, promoting a better understanding of the content.
Learn more about presentation here:
https://brainly.com/question/28233657
#SPJ11
what important scrum artifact is used to graphically display progress on each sprint during the monitoring and controlling process?
Answers
The crucial scrum artifact that has the function of graphically displaying progress on every sprint during the monitoring and controlling process is called a burndown chart.
The product increment is always thought of as the most important of the three artifacts of Scrum. It's the kind of the product that will be transfer at the end of each sprint. Whereas, the sprint backlog outlines what must be fulfilled within a sprint, the product increment details the outcome of all that work. A burndown chart present the amount of work that has been fulfilled in an epic or sprint, and the total work remaining. Burndown chart is used for speculating your team's likelihood of completing their work in the time available.
Learn more about The scrum artifact at https://brainly.com/question/29062642
#SPJ4
What are 5 different google g-suite tools that you can use to collaborate and communicate with othe
Answers
it is google docs like stuff made by google
what is a blend of the physical, virtual, and electronic environments creating a real-time ambient environment that changes as the user moves from one place to another?
Answers
This is known as a "smart environment" or "ubiquitous computing." It is a technology-enabled environment that is able to sense and respond to user interactions in real time.
Ambient Environments: A Blend of Physical, Virtual, and Electronic WorldsA smart environment is a technology-enabled environment that senses and responds to user interactions in real time. It blends the physical, virtual, and electronic worlds together to create an ambient environment that changes as the user moves from one place to another. This allows for a personalized experience that is seamless and intuitive.
A smart environment is a revolutionary technology that is transforming the way we interact with our surroundings. By combining physical, virtual, and electronic components, these environments are able to sense and respond to user interactions in real time. This creates a personalized experience that is seamless and intuitive, changing as the user moves from one place to another.
Learn more about the Environment: https://brainly.com/question/17413226
#SPJ4
Why might one choose to use a mnemonic device in order to remember information? Mnemonic devices are used as a strategy for improving memory. Mnemonic devices make it easier to remember information that is difficult, long, or complex.
Answers
A mnemonic device is a memory trick that can improve your recall and retention of information. Greek antiquity served as the foundation for this teaching strategy. To move information from your short-term memory to your long-term memory, you might employ mnemonic devices as memory aides.
Any learning strategy that promotes information retention or retrieval in the human mind for greater comprehension is referred to as a mnemonic device, also known as a memory device. In mnemonics, information is encoded using certain methods that make it easy to remember and recall, such as retrieval cues, imagery, and complex encoding. Mnemonics enable new knowledge to be connected to something more relatable or significant, improving subject memory retention. Despite the fact that mnemonics can be applied to a range of information types and in visual or kinesthetic formats, they are most frequently utilized for lists and in aural formats, such as rhyme schemes, acronyms, initialisms, or catchy phrases.
Learn more about mnemonic from
brainly.com/question/22724173
#SPJ4
How to send an email to multiple recipients individually.
Answers
Answer:
The BCC method
Explanation:
Corrine is doing online research about polar bears. One Web site she finds is wwwdefendersorg. What is the likely primary goal of this Web site?
A. to persuade or change the thinking or actions of others
B. to sell a product
C. to provide clear, balanced, and unbiased information about the topic
D. to entertain the viewer
Answers
Answer:
C
Explanation:
This should be right
cccccccccccccccccccc Explanation:
You're setting up a test environment that involves two subnets with three Windows Server 2016 servers on each subnet. The servers are running broadcast-based network services, such as DHCP. The host computer is attached to the production network, so you must prevent any conflicts. You want the two subnets to be able to communicate with each other. The test environment consists of a single Windows Server 2016 machine running Hyper-V. Describe how you plan to configure the virtual network.
Answers
Create a virtual switch in Hyper-V Manager. Launch the Hyper-V Manager, then select the server from the left pane or click "Connect to Server" in the right pane.
What is DHCP?The Dynamic Host Configuration Protocol (DHCP) is a client/server protocol that automatically assigns an IP address and other configuration information to an Internet Protocol (IP) host, such as the subnet mask and default gateway. Jul 29, 2021 DHCP (Dynamic Host Configuration Protocol) is a network management protocol that assigns an Internet Protocol (IP) address to any device or node on a network so that they can communicate via IP. The Dynamic Host Configuration Protocol (DHCP) is a network protocol that allows a server to automatically assign an IP address to a computer from a predefined range of numbers (called a scope) that has been configured for a specific network.To learn more about DHCP, refer to:
https://brainly.com/question/14234787
#SPJ1
2) What are two reasons we analyze algorithms?
a) make decisions about what algorithms to use
b) ease of coding
c) sorting data
d) predict performance
Answers
Answer:
Make decisions about what algorithms to use
Explanation:
In your own words: 1. Briefly explain how to create a new folder in Drive and move files to a new folder. 2. Explain why folders are helpful to keep your Drive organized.
Answers
To create a new folder in Drive, you can follow these steps:
Click on the "New" button in the top left corner of the Drive interface.Select "Folder" from the dropdown menu.Name the folder and hit "Create."How to move files on DriveTo move files to the new folder, select the files you want to move by checking the boxes next to them.Click on the "Move to" button in the top menu bar and select the new folder from the list of options.Folders are helpful in keeping your Drive organized because they allow you to group related files together in a logical manner.
This makes it easier to find and access the files you need quickly, without having to search through all your files one by one.
Folders also make it simpler to share multiple files with others at once, as you can share an entire folder rather than selecting individual files.
Read more about folders here:
https://brainly.com/question/20262915
#SPJ1
What is the keyboard shortcut for pasting information that you have already copied to the clipboard?.
Answers
The keyboard shortcut for pasting data that has already been copied to the clipboard is CTRL + V.
A keyboard shortcut, also referred to as a hotkey, is a sequence of one or more keys used in computing to quickly launch a software application or carry out a preprogrammed action.
This procedure might be included in the operating system's or application program's standard functionality, or it might have been programmed by the user using a scripting language. A "key" is sometimes defined differently depending on the integrated keyboard; some keyboards with pointing devices also have keys. For instance:
Copy: Ctrl + CCut: Ctrl + XPaste: Ctrl + VLearn more about keyboard shortcut https://brainly.com/question/12531147
#SPJ4
Your wireless network consists of multiple 802.11n access points that are configured as follows: SSID (hidden): CorpNet Security: WPA2-PSK using AES Frequency: 5.75 GHz Bandwidth per channel: 40 MHz Because of the unique construction of your organization's facility, there are many locations that do not have a clear line of sight between network clients and access points. As a result, radio signals are reflected along multiple paths before finally being received. The result is distorted signals that interfere with each other. What should you do
Answers
Answer:restart your internet box
Explanation:
What will print to the console after running this code segment?
A. 15.
B. 16.
C. 18.
D. 21.
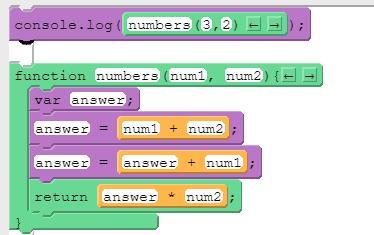
Answers
Answer:
16
Explanation:
answer =3+2
answer =5+3
return 8 × 2
16 will print to the console after running this code segment. Therefore, option B is correct.
What do you mean by code segment ?A code segment, also known as a text segment or simply text, is a section of an object file or the program's virtual address space that contains executable instructions.
A character array segment that represents a text fragment. Even though the array is directly accessible, it should be treated as immutable. This allows for quick access to text fragments without the overhead of copying around characters.
In memory, the code segment functions normally as read-only memory and has a fixed size; thus, without the need for loading, it can generally be found in read-only memory (ROM) on embedded systems.
answer = 3+2, answer = 5+3
return 8 × 2
= 16
Thus, option B is correct.
To learn more about the code segment, follow the link;
https://brainly.com/question/20063766
#SPJ2
Betta is taking up the hobby of knitting. How can she use typing to help her learn how to knit faster?
Answers
Typing can help Betta learn how to knit faster by allowing her to quickly search for tutorials, knitting patterns, and knitting tips online. She can also use typing to look up knitting terminology, abbreviations, and symbols. Additionally, typing can be used to save notes, helpful knitting tips, and important information Betta finds while researching. Finally, typing can be used to keep track of projects, yarn amounts, and other details related to her knitting.
Answer:
She can search up tutorials on how to knit.
Explanation:
I got an 5/5 Quiz 1.02 k12

A beam of electrons accelerated in an electric field is passing through two slits separated by a very small distance d and then hits a screen that glows when an electron hits it. The potential difference is v. Assume the distance from the slits to the screen is l.
Answers
The double-slit experiment is a display in modern physics that light and matter can demonstrate characteristics of both classically defined waves and particles; additionally, it demonstrates the fundamentally probabilistic nature of quantum mechanical phenomena.
what is double-slit experiment?
Thomas Young first performed this type of experiment in 1802, as a demonstration of visible light's wave behavior.
Light was thought to be made up of either waves or particles at the time.
If the viewing distance is greater than the slit separation (the far field), the phase difference can be calculated using the geometry. The path difference between two waves traveling at an angle is calculated as follows:
\(dsin\theta = d\theta\)
To know more about Quantum, visit: https://brainly.com/question/28034280
#SPJ4
How many residues separate amino acids that are stabilized by hydrogen bonds in α helices?.
Answers
The numbers of residues separate amino acids that are stabilized by hydrogen bonds in α helices is 3.6 amino acid residues.
Why are amino acids called residues?The Amino acids are known to be compounds that are said to be called residues if there is two or more amino acids that are known to be bond with each other.
Note that the amino group on one amino acid is one that tends to interacts with the carboxyl group and as such form a peptide bond.
Therefore, The numbers of residues separate amino acids that are stabilized by hydrogen bonds in α helices is 3.6 amino acid residues.
Learn more about amino acids from
https://brainly.com/question/2526971
#SPJ1
What is the shortcut for show/hide color panel?
O F2
O F6
O F4
Answers
Answer:
A F4
Explanation:
I have no idea because
what are worms ? this question is from computer from chapter virus;
Answers
Answer:
A computer worm is a type of malware that spreads copies of itself from computer to computer. A worm can replicate itself without any human interaction, and it does not need to attach itself to a software program in order to cause damage.
Explanation:
MNIST dataset - The MNIST dataset is divided into two sets - training and test. Each set comprises a series of images (28 x 28-pixel images of handwritten digits) and their respective labels (values from 0-9, representing which digit the image corresponds to). a) Use mnist function in keras datasets to split the MNIST dataset into the training and testing sets. Print the following: The number of images in each training and testing set, and the image width and height. b) Write a function (with images of ten digits and labels as the input) that plots a figure with 10 subplots for each 0-9 digits. Each subplot has the number of the handwritten digit in the title. c) Create a loop to call the plot function in (b) with images from each set to create three figures. Note: the code has to select the images randomly. Include all the 10 digits in each figure. Show the results of your code. d) In machine learning, we usually divide the training set into two sets of training and validation sets to adjust a machine learning model parameters. In your code, randomly select 20% of the training images and their corresponding labels and name them as x_valid and y valid, respectively. Name the remaining training images and their labels as x_train and y_train, respectively. Print the number of images in each training and validation set. Note: that there are no overlaps between the two sets.
Answers
a) To split the MNIST dataset into training and testing sets using the mnist function from Keras datasets, and print the number of images in each set along with the image width and height,
you can use the following code:
from tensorflow.keras.datasets import mnist
# Load the MNIST dataset
(x_train, y_train), (x_test, y_test) = mnist.load_data()
# Print the number of images in each set
print("Number of images in the training set:", x_train.shape[0])
print("Number of images in the testing set:", x_test.shape[0])
# Print the image width and height
print("Image width:", x_train.shape[1])
print("Image height:", x_train.shape[2])
b) To write a function that plots a figure with 10 subplots for each digit, you can use the following code:
import matplotlib.pyplot as plt
def plot_digits(images, labels):
fig, axes = plt.subplots(2, 5, figsize=(10, 4))
axes = axes.ravel()
for i in range(10):
axes[i].imshow(images[i], cmap='gray')
axes[i].set_title(str(labels[i]))
axes[i].axis('off')
plt.tight_layout()
plt.show()
c) To create a loop that randomly selects images from each set and calls the plot function to create three figures, each containing all 10 digits, you can use the following code:
import numpy as np
# Concatenate the training and testing sets
x_all = np.concatenate((x_train, x_test))
y_all = np.concatenate((y_train, y_test))
# Create three figures
for _ in range(3):
# Randomly select 10 images from the dataset
indices = np.random.choice(len(x_all), size=10, replace=False)
selected_images = x_all[indices]
selected_labels = y_all[indices]
# Call the plot function
plot_digits(selected_images, selected_labels)
d) To randomly select 20% of the training images and labels as the validation set, while keeping the remaining images and labels as the training set, you can use the following code:
from sklearn.model_selection import train_test_split
# Split the training set into training and validation sets
x_train, x_valid, y_train, y_valid = train_test_split(x_train, y_train, test_size=0.2, random_state=42)
# Print the number of images in each set
print("Number of images in the training set:", x_train.shape[0])
print("Number of images in the validation set:", x_valid.shape[0])
This code splits the training set into 80% for training (x_train and y_train) and 20% for validation (x_valid and y_valid). The train_test_split() function from scikit-learn is used to perform the random split, ensuring there are no overlaps between the two sets.
Learn more about dataset here:
https://brainly.com/question/31190306
#SPJ11
A small startup company has hired you to harden their new network. Because funds are limited, you have decided to implement a unified threat management (UTM) device that provides multiple security features in a single network appliance: Firewall VPN Anti-spam Antivirus You join the UTM device to the company's Active Directory domain. The company's traveling sales force will use the VPN functionality provided by the UTM device to connect to the internal company network from hotel and airport public Wi-Fi networks. Which weaknesses exist in this implementation
Answers
Answer: The UTM represents a single point of failure
Explanation:
Unified threat management is a method used in information security which has to do with the installation of a single hardware or software that provides several security functions.
Even though it's easy to manage from a single device, the disadvantage is that within the information technology infrastructure, there is a single point of failure.
What can you do to help create a safe online environment?
Answers
Answer:
by not adding a scam proof app
Explanation:
because thats life
What software enables an os to communicate with hardware?.
Answers
Answer:
device driver: A piece of software that acts as a translator, enhancing the capabilities of the operating system by enabling it to communicate with hardware.
Explanation:
hope this helps.
What do HIPAA guidelines protect?
Answers
Answer:
They protect patient medical records im pretty sure
Explanation:
which protocol, used to handle low-level housekeeping tasks such as router advertisements, involves simple, single sessions that consist of a packet or a series of packets?
Answers
Internet Control Message Protocol (ICMP) uses straightforward, single sessions that are made up of a packet or a set of packets to handle low-level housekeeping duties like router ads.
ICMP: What is it?When network issues prohibit the transmission of IP packets, network devices like routers employ ICMP (Internet Control Message Protocol) to emit error messages to the source IP address.When a gateway to the internet, such as a router, service, or host, cannot be contacted for packet delivery, ICMP constructs and transmits messages to the originating IP address.Any device connected to an IP network is able to send, receive, or process ICMP packets.The transport protocol ICMP does not convey data between systems.Although ICMP is not frequently usedKNOW MORE ABOUT ICMP click here:
https://brainly.com/question/10124043
#SPJ4
the contribution of Charles Babbage in the history of computer
Answers
Plz give me the brainliest :)
Please help!!
What does a for loop look for in the sequence of
data? Check all that apply
the first variable
the second variable
the third variable
the last variable
Answers
Answer:
The first and last variable
Explanation:
Answer:
A) the first variable and D) the last variable
Explanation:
because i said so, you're welcome !
State whether the given statement is True/False. Arguments are the input values to functions upon which calculations are performed.
Answers
You are defining a database table. Which of the following best explains why you would assign a Social Security number field as a text field?
a. The field will not be manipulated mathematically.
b. This is the default type for most DBMS table fields.
c. You plan to use this field as a primary key, which must therefore be a text field.
d. The field is too long to define as a numerical f
Answers
A Social Security number is a unique identifier assigned to individuals, consisting of a specific format of nine digits. While it is possible to represent the Social Security number as a numerical field, it is often more appropriate to assign it as a text field in a database table.
1. Assigning a Social Security number field as a text field in a database table is best explained by the fact that the field will not be manipulated mathematically. This choice is made to preserve the integrity and accuracy of the Social Security number data.
2. The primary reason for choosing a text field is that Social Security numbers are not typically subjected to mathematical operations within the context of database operations. Manipulating Social Security numbers mathematically is not a common requirement or practice. By defining the field as a text field, the database ensures that the Social Security number is stored and handled as a string of characters, preserving its exact format and preventing any unintended numerical calculations or conversions.
3. Additionally, using a text field allows for the inclusion of leading zeros, which are significant in Social Security numbers. Numerical fields may remove leading zeros, potentially altering the data. By using a text field, the integrity and accuracy of the Social Security number data are maintained.
4. While the other options provided (b, c, and d) do not directly justify the choice of a text field for a Social Security number, it is important to note that the specific requirements and constraints of the database system being used can also influence the choice of field type. However, the primary reason for assigning a Social Security number field as a text field is its non-mathematical nature and the need to preserve its format and integrity.
Learn more about database table here: brainly.com/question/30883187
#SPJ11
QUESTION: You are defining a database table. Which of the following best explains why you would assign a Social Security number field as a text field?
a. The field will not be manipulated mathematically.
b. This is the default type for most DBMS table fields.
c. You plan to use this field as a primary key, which must therefore be a text field.
d. The field is too long to define as a numerical field.