Write a query to display the book number, title, subject, author last name, and the number of books written by that author. Limit the results to books in the Cloud subject. Sort the results by book title and then author last name (Figure P7.108).
Answers
According to standard SQL functioning, when sql mode is 'only full group by' it restricts the GROUP BY clause and SELECT clause such that select clause cannot have attributes which are not being used in group by clause, if any attribute have to be used in SELECT clause which is not part of GROUP BY clause then it must be used inside any aggregate function.
Methods to solve above error:
1. use this command to overwrite such restrictions on the query.
SET GLOBAL sql_mode=(SELECT REPLACE(sql_mode,'ONLY_FULL_GROUP_BY',''));
2. use only those attributes in select clause which are being used in GROUP BY clause.
i.e. use AU_ID in tthe SELECT clause and no other attribute.
Method 1 is more preferrable.
To know more that SQL, visit: https://brainly.com/question/25694408
#SPJ4
Related Questions
what is the most important consideration when choosing a rewritable dvd drive
Answers
There are a variety of factors to consider. However, the most important consideration is the type of discs that the drive can read and write. There are three different types of rewritable DVD drives. Each of these formats has its own advantages and disadvantages.
DVD+RW is another rewritable DVD format that is compatible with most DVD players and DVD-ROM drives. It is also faster than DVD-RW, which makes it a good choice for users who need to write large amounts of data to a disc quickly. However, it is also more expensive than DVD-RW, which makes it a less attractive option for users who are on a tight budget.
DVD-RAM is the third type of rewritable DVD format, and it is the most versatile of the three. It can be written to and erased many times, and it is also more durable than other rewritable DVD formats. However, it is not compatible with most DVD players and DVD-ROM drives, which makes it a less attractive option for users who need to share their data with others.
To know more about factors visit:
https://brainly.com/question/31931315
#SPJ11
During active listening, which response is NOT an example of providing feedback to the speaker to show that you understand his or her thoughts?
A.
nodding your head
B.
turning your back to the speaker
C.
saying, "You're saying that his reaction made you feel appreciated?"
D.
saying, "Sorry to interrupt, but can you explain that part again?"
Answers
Answer:
The answer is D.
Explanation:
They/you are asking the speaker to clarify what they just said.
Answer:
B. turning your back to the speaker
Explanation:
is there provision of monetary fine against Cyber Law in Nepal
Answers
Answer:
Accessing any computer system without authority results in imprisonment for three years, or a fine of two hundred thousand rupees, or both. Intentional damage to or deleting data from a computer system carries imprisonment for three years, or a fine of two hundred thousand rupees, or both
Explanation:
hope this helps you
Go to your Canvas course and locate the Assignment: Writing Prompt 1: Is the Internet making us Meaner?and complete the activity.
When you are finished, come back here and copy/paste the following as your answer below:
I have completed the Writing Prompt 1: Is the Internet making us Meaner? activity and submitted my assignment in CANVAS. By pasting this text below. I understand that the grade marked here is NOT the grade for the actual assignment and only a place holder for the grade I earn in Canvas.

Answers
Answer and Explanation:
The Internet is not changing anything other than making you extreme. The nice become nicer, the mean become meaner, the nice become mean, and the mean become nice. The internet just makes things easier to do. It really isn't a factor in if you are mean or not.
Answer:
Explanation:
POV: you didn’t find your answer
State one criteria that makes a piece of malware a virus.
Answers
Answer: Self replication
Explanation: Malware is a catch-all term for any type of malicious software, regardless of how it works, its intent, or how it's distributed. A virus is a specific type of malware that self-replicates by inserting its code into other programs.
To discover how many cells in a range contain values that meet a single criterion, use the ___ function
Answers
Answer:
COUNTIF
Explanation:
the Countif function counts the number of cells in range that meets a given criteria.
What defines employability
Answers
What is the output of the following snippet?
my_list =
[[0, 1, 2, 3] for i in range (2) ]
print (my_list [2] [0])
Answers
Answer:
Explanation is being shown in the file that takes you to the link
Contrasting colors should be used to
Answers
Answer:
It should be used to add visual interest
Which of these might cause a STOP error in Windows? Select 2 options. bad application coding bad or incompatible driver overheating an application stops responding to commands a missing image on a web page
Answers
Answer:
i think its bad driver and coding
Explanation:
The STOP error in Windows can be found with bad application coding or bad or incompatible driver. Thus, options A and B are correct.
What is a STOP error?STOP error in windows can be given as the blue and death screen. The screen has been found in the operating system with the fatal error and gave rise to the development of a bug enabling the operation.
The error causes the system to shut down or restart the computer system. The error can be fixed by restarting the computer or updating the windows, and other ways.
The error in Windows such as STOP can be found for the reasons such as bad coding for the application, or the incompatible driver installed in the system that gave rise to inappropriate working. Thus, options A and B are the correct reasons for the STOP error in windows.
Learn more about STOP error, here:
https://brainly.com/question/15031386
#SPJ5
Which types of computer hardware are internal?
Answers
Answer:
Here are some :) (sorry if there are too many)
Explanation:
RAM (Random Access Memory): It's a fast-access memory that is cleared when the computer is powered-down. RAM attaches directly to the motherboard, and is used to store programs that are currently running.
Video Card/GPU (Graphics Processing Unit): It's a specialized processor originally designed to accelerate graphics rendering.
Sound Card: USB sound "cards" are external devices that plug into the computer via USB.
Storage: SSD (Solid State Drive): It is a data storage device that uses solid-state memory to store persistent data.
HDD (Hard Disk Drive): It is a non-volatile storage device which stores digitally encoded data on rapidly rotating platters with magnetic surfaces. Just about every new computer comes with a hard disk these days unless it comes with a new solid-state drive.
CPU (Central Processing Unit/ sometimes just called a processor) It's a machine that can execute computer programs, and sometimes called the brain of the computer.
Motherboard: The motherboard is the body or mainframe of the computer, through which all other components interface. It is the central circuit board making up a complex electronic system.
Firmware: Firmware is loaded from the Read only memory (ROM) run from the Basic Input-Output System (BIOS). It is a computer program that is embedded in a hardware device, for example a microcontroller.
Power Supply: The power supply as its name might suggest is the device that supplies power to all the components in the computer.
CD-ROM Drive: There are two types of devices in a computer that use CDs: CD-ROM drive and a CD writer. The CD-ROM drive used for reading a CD. The CD writer drive can read and write a CD.
Floppy Disk: A floppy disk is a type of data storage that is composed of a disk of thin, flexible(“floppy”) magnetic storage medium encased in a square or rectangular plastic shell.
Internal Storage: Internal storage is hardware that keeps data inside the computer for later use and remains persistent even when the computer has no power.
Disk Array Controller: A disk array controller is a device which manage the physical disk drives and presents them to the computer as logical units.
On some computers the speakers are internal as well. :)
Which category does codec fall under?
Codec falls under the ______category, as it affects the quality of the video.
Answers
Codec falls under the compression category, as it affects the quality of the video.
A codec is a program or device that is used to encode or decode digital data, such as audio, video, or images. The term "codec" is derived from the words "coder" and "decoder".
Codecs are used to compress digital data for efficient transmission or storage, and then decompress the data for playback or use. They use various algorithms to compress and decompress the data and can be either software or hardware-based.
Codecs are used in a variety of applications, such as videoconferencing, streaming media, digital television, and digital audio. They allow for the efficient transmission and storage of high-quality digital content while minimizing bandwidth requirements and storage space.
Overall, codecs are an essential component of modern digital communication and media and have played a significant role in the development of many new technologies and applications.
Learn more about codec here:
https://brainly.com/question/14618121
#SPJ11
A three phase generator has each of its windings out-of-phase with each other by ? .
Answers
A three phase generator has each of its windings out-of-phase with each other by 120 degrees.
What is Three phase generator?An AC three-phase generator is known to be called the three AC single-phase generators.
They are said to be generators that tends to run sequentially with a kind of offset of 120° that often exist between them been taken two at a time.
Therefore, based on the above, one can say that the three phase generator has each of its windings out-of-phase with each other by 120 degrees.
Learn more about three phase generator from
https://brainly.com/question/15052099
#SPJ1
Which jobs are most likely to be replaced by robots and what effect will this have
Answers
Answer:
Here we go. Generally the robots are designed in order to do the work which has very much risk and Humans find it too laborious or hard to do. The robots will be used for the army, or as laborers. In my country Nepal, there's a restaurant where robots are used as waiters. They take order from you and provide you the food. The robots can be used for various purposes but I don't think they will be appointed for the job of higher authority. The use of robots will have massive effect in human life. The use of robots and appointing them in various jobs will cause the problem of unemployment. The poor will be affected and their existence may get into problem. This is one effect but there can be many effects from the use of robots. Using robot in army can reduce human deaths but also people get unemployed. There is both advantage and disadvantage from their use.
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
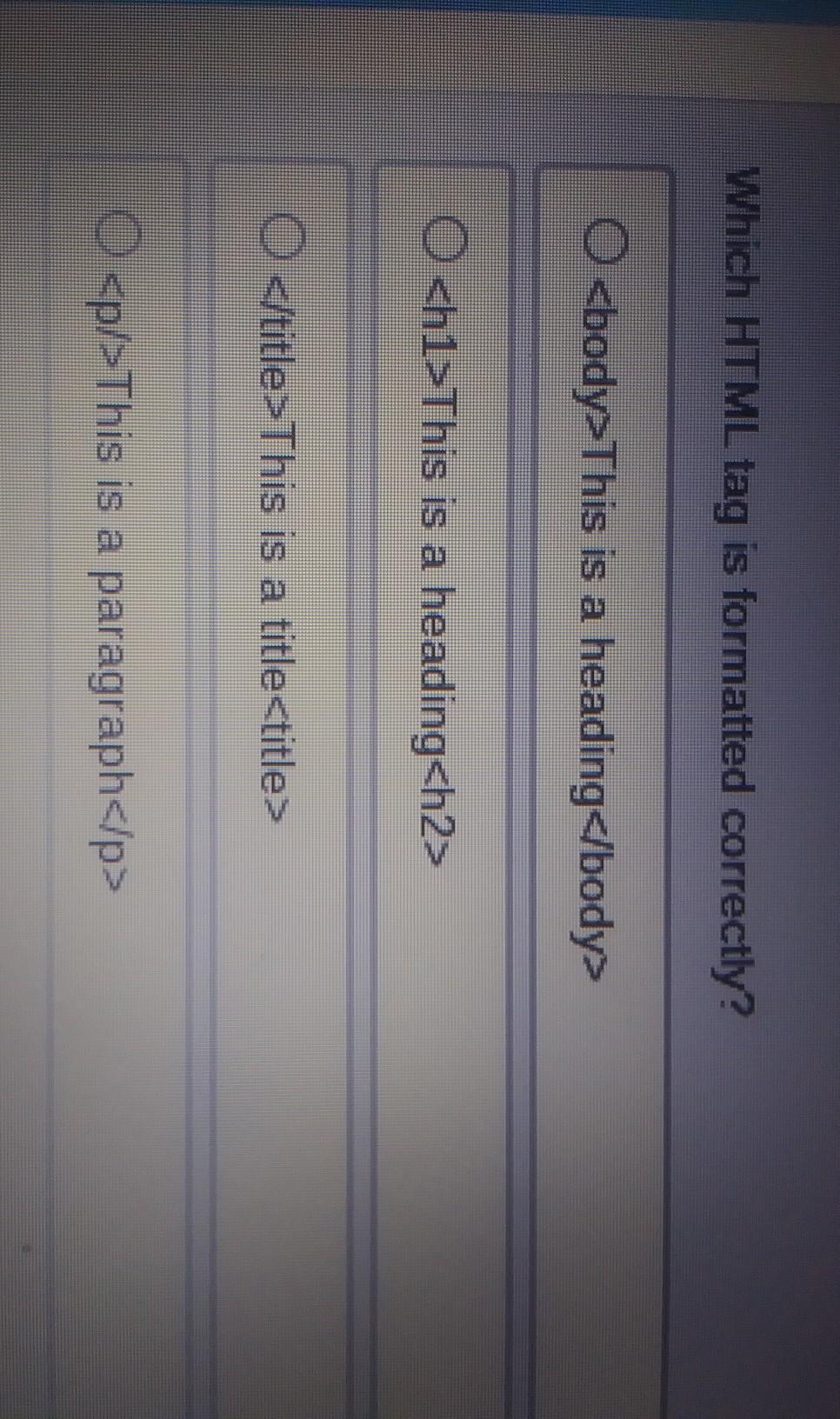
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
With most forms of media, you can use up to _____% under “fair use” guidelines.
Answers
Answer:
With most forms of media, you can use up to 10% under “fair use” guidelines.
How can an Outlook user search for contacts? Check all that apply.
✓ the Search bar located above the list of contacts
the Search People bar on the Find command group
the Search People located on the People navigation icon
✓ CTL + E to activate the search contacts box
✓ advanced Find under the Search tab
* the options menu in the backstage view
Answers
Answer:
A. the Search bar located above the list of contacts
B. the Search People bar on the Find command group
C. the Search People located on the People navigation icon
D. CTL + E to activate the search contacts box
E. advanced Find under the Search tab
Answer:
A. B. C. D. E.
Explanation:
what are the methods used by hackers to modify a route table?
Answers
The methods used by hackers to modify a route table include:
1. ARP Spoofing: Hackers can use Address Resolution Protocol (ARP) spoofing to manipulate the ARP cache of a target device, thus changing the destination IP address to their own controlled system, effectively modifying the route table.
2. Routing Protocol Attacks: Hackers can exploit vulnerabilities in routing protocols like OSPF or BGP by injecting false routing information, causing the route table to be modified with incorrect routes.
3. Man-in-the-Middle Attacks: In this method, hackers can intercept and modify the data packets transmitted between two devices, effectively modifying the route table by diverting the packets to their own controlled systems.
4. DNS Poisoning: By poisoning the DNS cache, hackers can redirect users to malicious websites, effectively modifying the route table by providing false IP address information.
5. ICMP Redirect Attacks: Hackers can use Internet Control Message Protocol (ICMP) redirect attacks to manipulate a target device's route table by sending a spoofed ICMP redirect message, effectively changing the preferred route.
To summarize, hackers can modify a route table using methods such as ARP spoofing, routing protocol attacks, man-in-the-middle attacks, DNS poisoning, and ICMP redirect attacks. These techniques allow them to manipulate the route tables of target devices and redirect network traffic to their controlled systems.
Learn more about ICMP here:
https://brainly.com/question/30523285
#SPJ11
write aQbasic program to find simple interest,time ,rate principal using go to function. don't use any ai.
Answers
Here is a sample program in QBasic that calculates simple interest using the GOTO function:
The QBasic ProgramCLS
INPUT "Enter Principal amount: ", P
INPUT "Enter Rate of interest: ", R
INPUT "Enter Time in years: ", T
SI = P * R * T / 100
PRINT "Simple Interest = $"; SI
GOTO END
END:
END
This program takes inputs for the principal amount (P), the rate of interest (R), and the time in years (T).
It then calculates the simple interest using the formula SI = P * R * T / 100 and prints the result. Finally, the program jumps to the end using the GOTO END statement.\
Read more about Qbasic here:
https://brainly.com/question/20727977
#SPJ1
What is computer. Write full form of mips
Answers
Answer:
Stands for "Million Instructions Per Second." It is a method of measuring the raw speed of a computer's processor. ... The MIPS measurement has been used by computer manufacturers like IBM to measure the "cost of computing." The value of computers is determined in MIPS per dollar.
However, you need to add many practices and techniques to the framework."
Answers
Yes, it is true that in order to fully utilize the framework, you need to incorporate many practices and techniques. It is important to continuously evaluate and update your practices and techniques in order to stay current and make the most of the framework.
a variety of practises and approaches must be used. This is especially true when it comes to business management frameworks like Six Sigma or the Agile approach. While these frameworks offer a helpful structure for planning work and enhancing efficiency, it's critical to regularly review and update the methods and strategies used to execute the framework in order to stay current and maximise its advantages. You can make sure that you are producing the greatest results for your organisation and maintaining your position as a leader in your industry by continuously improving and modifying your approach to the framework.
learn more about techniques here:
https://brainly.com/question/30078437
#SPJ11
PLS HURRY!!!
Look at the image below!

Answers
Answer:
Ctrl+c
Explanation:
U Need to use Ctrl+C
If the value of score1 is 350 and the value of score2 is 210, what will be the value of result after the code segment is executed
Answers
The value of result of the code segment is executed is known to be 4.
Why is the value of the code segment so?When the result of is not executed because the condition is said to be false and also when there is a false condition is, the else statement will be said to be true
Therefore, result = result + 2; -> result is brought up by 2 to bring about 4 and as such, the value of result of the code segment is executed is known to be 4.
Learn more about scores from
https://brainly.com/question/19492935
#SJ1
Answer:
its 5
Explanation:
I put 4 and got it wrong and checked the test
pls answer asap do not use internet
what are the differences and similarities between windows os and linux based os
Answers
Answer:
key differences between linux and windows operating system linux is free and open resource whereas windows is a commercial operating system whose source code is inaccessible windows is not customizable as against linux is customizable and a user can modify the code and can change it looks and feels
Explanation:
I hope this helps
State what the code will do:
int("76423")
Answers
The thing that the code will do: Int("76423"), Asc(" T ") and 12 Mod 5 are:
Take the string "76423" and return the integer 76423.Return the ASCII number for the character "T"Returns the remainder when 12 is said to be divided by 5, i.e. 2.What is Coding?Coding is the process of writing instructions in programming languages for computers, according to the definition. Programming is used to create the websites, apps, and other technologies that we use on a daily basis.
Note that ASCII is the foundation for all character sets used in HTML, on the Internet, and in contemporary computers.
Learn more about ASCII number from
https://brainly.com/question/13143401
#SPJ1
See full question below
State what the code will do: Int("76423"), Asc(" T") and 12 Mod 5.
Which term refers to actions that you would typically perform on a computer to revive it if it functions in an unexpected manner?
The corrective action(s) that you need to perform on a computer in case it functions in an unexpected manner is called______?
Answers
Answer:
Reconected to your computor
Explanation:
can you please help me with this question

Answers
Random Acess Memory is usually an external device which is a mix of both RAM and ROM.
Thus, The hardware in a computing device called RAM (Random Access Memory) stores the operating system (OS), application programs, and data that are currently in use so that the processor of the device can access them rapidly.
The primary memory of a computer is RAM. Compared to other forms of storage like a hard disk drive (HDD), solid-state drive (SSD), or optical drive, it is much faster to read from and write to.
Volatile random access memory. This means that information is kept in RAM while the computer is running, but it is erased when the machine is powered off. The operating system and other files are frequently loaded from an HDD or SSD into RAM when the computer is restarted.
Thus, Random Acess Memory is usually an external device which is a mix of both RAM and ROM.
Learn more about RAM, refer to the link:
https://brainly.com/question/31089400
#SPJ1
When you want to express the ratio of all outputs to all inputs, you should use a ________ productivity measure.
Answers
When you want to express the ratio of all outputs to all inputs, you should use a total productivity measure.
What is total measure productivity?Productivity is known to be one that can be calculated by the act of measuring the number of units that is made and that is relative to employee labor hours or by the act of measuring a firm's net sales that is known to be relative to employee labor hours.
Note that Multifactor productivity connote the fact that the productivity of all the inputs that are said to be used in the production process.
Therefore, When you want to express the ratio of all outputs to all inputs, you should use a total productivity measure.
Learn more about productivity from
https://brainly.com/question/2992817
#SPJ1
Which of these scenarios is the BEST example of digital piracy?
A.
Michael threatens physical harm to someone online after they get in a disagreement.
B.
Tamara intentionally places a virus on a school computer after receiving a bad grade.
C.
Cory downloads a game on the school's computer without permission.
D.
Grace uses a website to download music illegally to her phone.
Answers
Answer:
D
Explanation:
Because it doesn't say how much music she downloaded it could've been 100000 songs!
um can anyone who is really into science and physics answer this question
Answers
Answer:
What question?
Explanation: