write the steps to create a web page using text editor and a web page.
pls pls pls answer
Answers
Answer:
Step 1: Open Your Text Editor. The first step is to open your text editor. ...Step 2: Write Your HTML Skeleton. Now that your text editor is open, you can begin writing your HTML. ..
Step 3: Save Your File. ...
Step 4: Open Your Web Page in Your Browser.
Related Questions
Write a method called allDigitsOdd that returns whether every digit of a positive integer is odd. Return true if the number consists entirely of odd digits (1, 3, 5, 7, 9) and false if any of its digits are even (0, 2, 4, 6, 8). For example, the call allDigitsOdd(135319) returns true but allDigitsOdd(9145293) returns false.
Answers
Answer:
Sample output:
Enter integer 3232423
true
Enter integer 12131231
false
Explanation:
Above is the output of the program and for the solution check the screenshots attach to understand clearly the program.
Thanks



Print a message telling a user to press the letterToQuit key numPresses times to quit. End with newline. Ex: If letterToQuit = 'q' and numPresses = 2, print:

Answers
You can find in the photo. Good luck!

Compare the memory organization schemes of contiguous memory allocation and paging with respect to the following issues: a. External fragmentation b. Internal fragmentation c. Ability to share code across processes
Answers
Answer:
The comparison is based on memory organization schemes of contiguous memory allocation and paging with respect to External fragmentation, Internal fragmentation and Ability to share code across processes.
Explanation:
Memory organization schemes of contiguous memory allocation:
Contiguous memory allocation schemes suffers from external fragmentation. The reason is that address space is distributed contiguously and the holes and gaps keep growing when the old processes die and new processes are introduced. The variable size partition suffers from external fragmentation however the fixed size partitions do not suffer from external fragmentation. Contiguous memory allocation with variable size partitions does not encounter an internal fragmentation but with fixed size partitions suffers from internal fragmentation. Contiguous memory allocation does not support sharing code across processes. This is because the virtual memory segment of a process is not fragmented into non-contiguous fine grained blocks.
Paging:
Paging does not encounter external fragmentation as pages are of the fixed or equal size. So this reduces external fragmentation. However paging suffers from internal fragmentation. This is because a process can request more space or it can request for a less space. When page is allocated to the such a process that page is no longer utilized.This results in internal fragmentation because of the wastage of space even when the page has internal space but cannot be fully utilized. Paging allows to share code across processes.
Do you trust machine learning application?
Answers
Answer:
Trusting a machine learning model, in general, can be interpreted as creating a robust model which gives largely accurate results and has a high generalization ability. Classification models learn from past experience, so the robustness of a model primarily depends on the given training set
Explanation:
Hope it helps
Please mark as brainliest
Pls help I'm trying not to fail.

Answers
Answer:
18
Explanation:
tryIt(2) will return 9 because 2+7 is 9 (7 is the default value of b)
9 * 2 = 18.
You can try this yourself at replit.

Software as a Service (SaaS) allows users to
remotely access which of the following? Check all
of the boxes that apply.
software
data
applications
Answers
Answer:
Data software provides the best and most powerful software that allows you in the class
Answer:
software
data
applications
(all)
Explanation:
In which of the following situations must you stop for a school bus with flashing red lights?
None of the choices are correct.
on a highway that is divided into two separate roadways if you are on the SAME roadway as the school bus
you never have to stop for a school bus as long as you slow down and proceed with caution until you have completely passed it
on a highway that is divided into two separate roadways if you are on the OPPOSITE roadway as the school bus
Answers
The correct answer is:
on a highway that is divided into two separate roadways if you are on the OPPOSITE roadway as the school busWhat happens when a school bus is flashing red lightsWhen a school bus has its flashing red lights activated and the stop sign extended, it is indicating that students are either boarding or exiting the bus. In most jurisdictions, drivers are required to stop when they are on the opposite side of a divided highway from the school bus. This is to ensure the safety of the students crossing the road.
It is crucial to follow the specific laws and regulations of your local jurisdiction regarding school bus safety, as they may vary.
Learn more about school bus at
https://brainly.com/question/30615345
#SPJ1
how does the internet bring people farther apart
use a paragraph to answer the question
Answers
Answer:
First of all you may not be able to see your friend in person and it gets very sad. Sometimes you call them but they don't answer you because they don't have enough time to talk or they have something else to do. They won't always want to be on the internet you know, they want to go outside and get a life and not be like the FRE-KIN T-I-K T-O-K-E-R-S WHO ARE CHILDREN AND BEING VERY STU-PID AND ARE TOTAL IDIOTS AND SAY STUFF THAT MAKE NO SENSE AND TRY TO GET ATTENTION. OH DON'T BRING TOWARDS THE GA-CHA IT SO TRASH. I still hate gacha :) and I am happy. Another thing is what some people post, you see you meet friends in real life and sometimes you get to know them but you don't know what they might be doing on the internet and another thing is that they post stuff that makes you feel uncomfortable and disgusted.
I am doing a customer service manual and need a toc. I can't get the numbers lined up. Can someone please help me? I am using Microsoft word

Answers
Below is a Table of Contents (TOC) for your customer service manual with aligned numbers using Microsoft Word:
Welcome StatementGetting StartedWays to Discern Customers' Needs and ConcernsTelephone Communication4.1 Transferring a Customer's Call4.2 Sending an EmailSelf-Care After the JobHow to Manage Your Time WiselyFundamental Duties of a Customer Service WorkerEnhancing Customer Impressions and SatisfactionDifference Between Verbal and Nonverbal CommunicationKey TraitsBest Speaking SpeedKnowing the Different Problems and How to Manage Them12.1 Extraordinary Customer Problems12.2 Fixing Extraordinary Customer ProblemsKnowing Customer Diversity13.1 Tactics for Serving Diverse and Multicultural CustomersKnowing How to Handle Challenging CustomersWhat is the customer service manual?Below is how you can create a Table of Contents (TOC) with aligned numbers in Microsoft Word:
Step 1: Place your cursor at the beginning of the document where you want to insert the Table of Contents.
Step 2: Go to the "References" tab in the Microsoft Word ribbon at the top of the window.
Step 3: Click on the "Table of Contents" button, which is located in the "Table of Contents" group. This will open a drop-down menu with different options for TOC styles.
Step 4: Choose the TOC style that best fits your needs. If you want aligned numbers, select a style that includes the word "Classic" in its name, such as "Classic," "Classic Word," or "Classic Format." These styles come with aligned numbers by default.
Step 5: Click on the TOC style to insert it into your document. The TOC will be automatically generated based on the headings in your document, with numbers aligned on the right side of the page.
Step 6: If you want to update the TOC later, simply right-click on the TOC and choose "Update Field" from the context menu. This will refresh the TOC to reflect any changes you made to your headings.
Note: If you're using a different version of Microsoft Word or a different word processing software, the steps and options may vary slightly. However, the general process should be similar in most word processing software that supports the creation of TOCs.
Read more about customer service here:
https://brainly.com/question/1286522
#SPJ1
See text below
I am doing a customer service manual and need a toc. I can't get the numbers lined up. Can someone please help me? I am using Microsoft word
Welcome Statement
Getting Started
Ways to discern customers' needs and concerns
Telephone communication....
Transferring a customer's call
Sending an email
Self-Care after the job
How to manage your time wisely
Fundamental duties of a Customer Service Worker
Enhancing Customer Impressions and Satisfaction
N
5
.5
6
Difference between Verbal and Nonverbal Communication
.6
Key Traits.....
.7
Best speaking speed
7
Knowing the different problems and how to manage them
Extraordinary Customer Problems
Fixing Extraordinary Customer Problems
Knowing Customer Diversity
Tactics for serving diverse and Multicultural customers
Knowing how to handle challenging customers.
Sure! Here's a Table of Contents (TOC) for your cu
examples in types of experimental methods
Answers
Lab Experiment
Field Experiment
Natural Experiment.
Answer:
Experimental research for individuals in the physical sciences and many other fields is the best-known kind of research design. The main reason is that experimental research is a typical scientific experiment, similar to that carried out in secondary schools.
Explanation:
The types of research designs are determined by how the researchers assign subjects to various conditions and groups. They are of three different types: pre-experimental, almost experimental, and real experimental research.
Pre-experimental Research Design:-
In pre-experimental research, the effect of the application of a supposedly changing independent variable is observed by either a group or different dependent groups. It is the simplest form of experimental design and does not involve a control group.
Quasi-experimental Research Design:-
The term "almost" refers to partial, half, or pseudo. The quasi-experimental research therefore resembles, but not the same, the real experimental research. The participants are not assigned randomly in quasi-examples and are therefore used in environments that are difficult or unable to randomize.
True Experimental Research Design:-
To confirm or refute a hypothesis, real experimental research is based on statistical analyses. It is the most exact experimental type and can be performed on two randomly assigned subjects with, or without a pretest.
The true experimental design of the research must include a control group, a variable that the researcher can manipulate and the distribution must be random.
Using the Multiple-Alternative IFTHENELSE Control structure write the pseudocode to solve the following problem to prepare a contract labor report for heavy equipment operators: The input will contain the employee name, job performed, hours worked per day, and a code. Journeyman employees have a code of J, apprentices a code of A, and casual labor a code of C. The output consists of the employee name, job performed, hours worked, and calculated pay. Journeyman employees receive $20.00 per hour. Apprentices receive $15.00 per hour. Casual Labor receives $10.00 per hour.
Answers
Answer:
The pseudo-code to this question can be defined as follows:
Explanation:
START //start process
//set all the given value
SET Pay to 0 //use pay variable that sets a value 0
SET Journeyman_Pay_Rate to 20//use Journeyman_Pay_Rate variable to sets the value 20
SET Apprentices_Pay_Rate to 15//use Apprentices_Pay_Rate variable to sets the value 15
SET Casual_Pay_Rate to 10//use Casual_Pay_Rate variable to set the value 10
READ name//input value
READ job//input value
READ hours//input value
READ code//input value
IF code is 'J' THEN//use if to check code is 'j'
COMPUTE pay AS hours * JOURNEYMAN_PAY_RATE//calculate the value
IF code is 'A' THEN//use if to check code is 'A'
COMPUTE pay AS hours * APPRENTICES_PAY_RATE//calculate the value
IF code is 'C' THEN//use if to check code is 'C'
COMPUTE pay AS hours * CASUAL_PAY_RATE//calculate the value
END//end conditions
PRINT name//print value
PRINT job//print value
PRINT code//print value
PRINT Pay//print value
END//end process
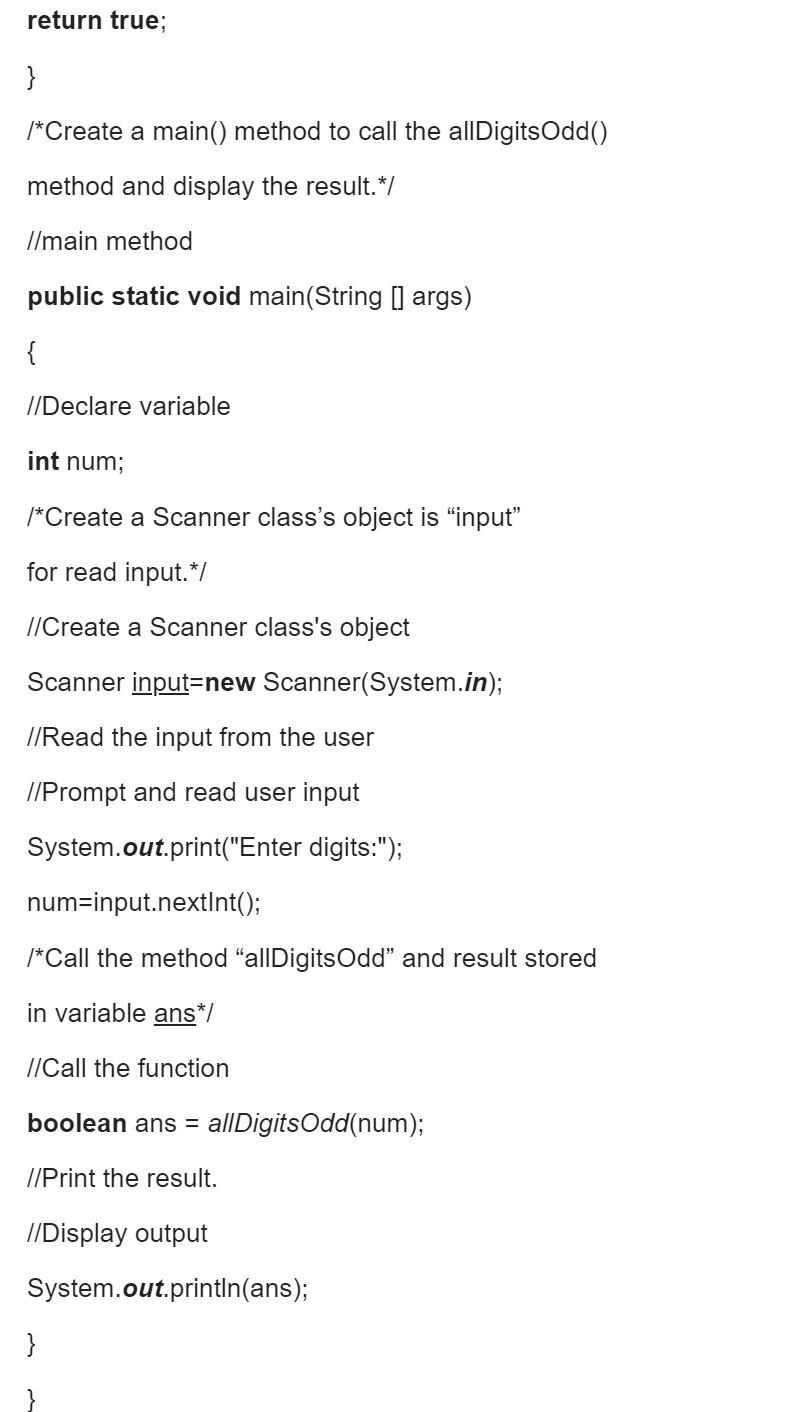
A function checkZeros accepts three double parameters. It checks to see if the sum of all three parameters is equal to zero. If this sum is equal zero, the function returns true, otherwise the function returns false. 1. Give an example CALL from main: 2. Write the prototype for the function: 3. Write down the definition (header and body) for the function.
Answers
Answer:
Explanation:
The following code is written in Java. It creates the interface/prototype, the function, and the main method call. The function takes in the three int parameters, adds them, and then checks if the sum equals zero, outputting the correct boolean value. Output can be seen in the picture attached below. Due to technical difficulties I had to add the code as a txt file below.

what is java programing
Answers
Answer:
Explanation:
Java is a class-based, object-oriented programming language that is designed to have as few implementation dependencies as possible. ... Java applications are typically compiled to bytecode that can run on any Java virtual machine (JVM) regardless of the underlying computer architecture
Answer:
The Java programming language was developed by Sun Microsystems in the early 1990s. Although it is primarily used for Internet-based applications, Java is a simple, efficient, general-purpose language. Java was originally designed for embedded network applications running on multiple platforms.
Explanation:
spreadsheet feature that can be used to arrange data from highest to lowest based on average
Answers
Answer:
RANK.AVG
Explanation:
Required
Arrange data in descending order based on average
The feature to do this is to use the RANK.AVG() function.
By default, the function will return the ranks of the selected data in descending order (i.e. from highest to lowest); though, the sort order can be changed to ascending order.
The syntax is:
=RANK.AVG (number, ref, [order])
Where
number \(\to\) The number to use as rank
ref \(\to\) The cell range
order \(\to\) 0 represents descending order while 1 represents ascending order
ITIL 4: Which of the following TRUE with respect to Practices in ITIL®?
A Practices are independents activities outside SVC
B: practice is just a new name given for process
C: practices support multiple activities within Value chain
D: every practice is tightly linked to a specific activity within value chain
Answers
Answer:
m
Explanation:
it would be c cause i take the test
The option that is true with respect to Practices in ITIL is that its practices support multiple activities within Value chain.
What are ITIL practices?ITIL is known to be the background of all the best methods used for delivering IT services.
Conclusively, the key element in the ITIL SVS is known to be the Service Value Chain as it uses an operating model for service delivery. Its practices aids the use of different activities within Value chain.
Learn more about Practices from
https://brainly.com/question/1147194
What is the definition of an adapter?
O the push that makes electrons move in a wire; the greater the voltage, the stronger the push
O a device that uses voice recognition to provide a service
O a device that converts one voltage to another
O communication of the binary data via the voltage level for each time interval
Answers
Answer:
an adapter is a device for connecting pieces of equipment that cannot be connected directly. But I do not know what the context of this question is in, so the answer that makes the most sense would have to be the 3rd option " a device that converts one voltage to another. "
Answer:
1.Adapter,2.digital signal,3.voltage,4.voice Assistant
Explanation:
1. A network administrator was to implement a solution that will allow authorized traffic, deny unauthorized traffic and ensure that appropriate ports are being used for a number of TCP and UDP protocols.
Which of the following network controls would meet these requirements?
a) Stateful Firewall
b) Web Security Gateway
c) URL Filter
d) Proxy Server
e) Web Application Firewall
Answer:
Why:
2. The security administrator has noticed cars parking just outside of the building fence line.
Which of the following security measures can the administrator use to help protect the company's WiFi network against war driving? (Select TWO)
a) Create a honeynet
b) Reduce beacon rate
c) Add false SSIDs
d) Change antenna placement
e) Adjust power level controls
f) Implement a warning banner
Answer:
Why:
3. A wireless network consists of an _____ or router that receives, forwards and transmits data, and one or more devices, called_____, such as computers or printers, that communicate with the access point.
a) Stations, Access Point
b) Access Point, Stations
c) Stations, SSID
d) Access Point, SSID
Answer:
Why:
4. A technician suspects that a system has been compromised. The technician reviews the following log entry:
WARNING- hash mismatch: C:\Window\SysWOW64\user32.dll
WARNING- hash mismatch: C:\Window\SysWOW64\kernel32.dll
Based solely ono the above information, which of the following types of malware is MOST likely installed on the system?
a) Rootkit
b) Ransomware
c) Trojan
d) Backdoor
Answer:
Why:
5. An instructor is teaching a hands-on wireless security class and needs to configure a test access point to show students an attack on a weak protocol.
Which of the following configurations should the instructor implement?
a) WPA2
b) WPA
c) EAP
d) WEP
Answer:
Why:
Answers
Network controls that would meet the requirements is option a) Stateful Firewall
Security measures to protect against war driving: b) Reduce beacon rate and e) Adjust power level controlsComponents of a wireless network option b) Access Point, StationsType of malware most likely installed based on log entry option a) RootkitConfiguration to demonstrate an attack on a weak protocol optio d) WEPWhat is the statement about?A stateful firewall authorizes established connections and blocks suspicious traffic, while enforcing appropriate TCP and UDP ports.
A log entry with hash mismatch for system files suggest a rootkit is installed. To show a weak protocol attack, use WEP on the access point as it is an outdated and weak wireless network security protocol.
Learn more about network administrator from
https://brainly.com/question/28729189
#SPJ1
e requirements of Phase 3 are as follows:
In this third phase, you will be obtaining the case, power supply, and monitor for your computer. You will also include a printer.
Case:
Analyze the specifications for the case. Discuss what stood out to you about your choice. For example, "Why did you choose this specific component?" What stood out to you (price, specifications, etc.)?
What are the specifications, source, and price of the case? How did each of these components influence your decision to select it?
Power Supply:
Analyze the specifications for the power supply. Discuss what stood out to you about your choice. For example, "Why did you choose this specific component?" What stood out to you (price, specifications, etc.)?
What are the specifications, source, and price of the power supply? How did each of these components influence your decision to select it?
Monitor:
Analyze the specifications for the monitor. Discuss what stood out to you about your choice. For example, "Why did you choose this specific component?" What stood out to you (price, specifications, etc.)?
What are the specifications, source, and price of the monitor? How did each of these components influence your decision to select it?
Printer:
Analyze the specifications for the printer. Discuss what stood out to you about your choice. For example, "Why did you choose this specific component?" What stood out to you (price, specifications, etc.)?
What are the specifications, source, and price of the printer? How did each of these components influence your decision to select it?
References:
List references used.
References should relate to decision-making articles in addition to a website where one could purchase the product.
All references must be in APA format.
Any images used must be cited properly.
Format:
APA formatted cover page as well as the entirety of the document.
Paragraphs are coherently organized, including the use of proper grammar and correct spelling.
Clearly organized using graphics and tables (where appropriate).
Acronyms are spelled out on first use.
Answers
Because this is a research that should b carried out, I will guide you on how to do same. Pay attention to the requirement on APA Formatting.
How can the above research be executed?In order to make an informed decision on each component, it is imperative that you conduct thorough research on their specifications, source and price.
Reliable sources of information such as reputable tech review websites should be utilized in the comparison of features and prices for each option available.
Proper citation using APA format will need to be observed together with inclusion of any images used. Organizing your document with clear and coherent structure will further enhance readability- utilizing tables and graphics where applicable.
Learn more about APA Formatting:
https://brainly.com/question/12548905
#SPJ1
what command in cisco IOS allows the user to see the routing table
Answers
Answer:
Show IP route command
Explanation:
listen to exam instructions which of the following are best practices for hardening a server? (select three.) answer disable or uninstall unnecessary software. set the account lockout threshold. apply the latest patches and service packs. require multiple authentication factors. disable inactive accounts. ensure that a host-based firewall is running. establish time-of-day restrictions.
Answers
Note that from the options given, the best option or best practice for hardening a server are:
disable or uninstall unnecessary software.(Option A)apply the latest patches and service packs. (Option B)require multiple authentication factors. disable inactive accounts. (Option C).What is Server Hardening?Server hardening is the process of improving the security of a server by taking steps to protect it from potential threats.
This can include installing security software, applying security patches and updates, disabling unnecessary services and software, and implementing security measures such as firewalls and authentication systems.
Note that the purpose of server hardening is to reduce the risk of unauthorized access to the server and protect it from potential attacks or vulnerabilities. By following best practices for server hardening, businesses and organizations can ensure that their servers are secure and protected from potential threats.
Learn more about Server Hardening:
https://brainly.com/question/19592219
#SPJ1
Discuss the advantages and disadvantages of using digital publishing over traditional forms of offset publishing.
Write in paragraph pls
Answers
Answer:
Advantages: Dynamic: Digital magazines are extremely dynamic. They can be read on tablets and mobile devices anywhere and anytime. Readers can access the information without delays.Unsold Stock: There are no fears of having unsold stock like that of printed newspapers and magazines.Disadvantages: Digital magazines can sometimes be harder to read than printed magazines as the reader must be able to zoom in and out. Again, this would depend on the chosen digital magazine software. Other issues some people may face is outdated software, poor internet connection and download speeds. With a physical magazine or newspaper, you needn’t worry about it running out of power.
In C++
Write a simple program to test your Circle class. The program must call every member function at least once. The program can do anything of your choice.
Answers
Answer:
int main() {
Circle* pCircle = new Circle(5.0f, 2, 3);
pCircle->up();
pCircle->down();
pCircle->left();
pCircle->right();
cout << "X: " << pCircle->getx() << endl;
cout << "Y: " << pCircle->gety() << endl;
cout << "Radius: " << pCircle->getRadius() << endl;
pCircle->print();
pCircle->update_radius(4.0f);
if (pCircle->isUnit()) {
cout << "is unit" << endl;
}
pCircle->move_x(10);
pCircle->move_y(10);
}
Explanation:
something like that?
Make a Python program to calculate a user's Body Mass Index. Use the console to ask their name, weight in lbs, and their height in feet and inches. You can use two variables to represent height if this makes it easier: one for inches, and one for feet. Use this data to calculate the users BMI using the formula: BMI
Answers
Answer:
Answered below
Explanation:
weight = float(input("Enter weight in lbs: "))
height_in_feet = float(input ("Enter height in feet: "))
height_in_inches = float(input("Enter height in inches: "))
total_height = height_in_feet + (height_in_inches * 0.0833)
weight_in_kg = weight * 0.454
bmi = weight_in_kg/ (total_height ** 2)
print (bmi)
17. What data structure is used for depth first
traversal of a graph.
Answers
Answer:
Depth First Search (DFS) algorithm traverses a graph in a depthward motion and uses a stack to remember to get the next vertex to start a search, when a dead end occurs in any iteration.anation:
What are your thoughts on copyright?
(Write 2 or more sentences)
Answers
Answer:
I look down on copyright. To take someone else's work and disguising it as your own seems like a form of theft.
How y’all doin?
Using your knowledge of classes, arrays, and array list, write the Java code for the UML above in NetBeans. [7 marks]
Answers
The Java code for the TestElection class that does the tasks is
java
import javax.swing.JOptionPane;
public class TestElection {
public static void main(String[] args) {
// Declare an array to store objects of the Election class
int length = Integer.parseInt(JOptionPane.showInputDialog("Enter the number of candidates:"));
Election[] candidates = new Election[length];
// Request values from the user to initialize the instance variables of Election objects and assign these objects to the array
for (int i = 0; i < length; i++) {
String name = JOptionPane.showInputDialog("Enter the name of candidate " + (i + 1) + ":");
int votes = Integer.parseInt(JOptionPane.showInputDialog("Enter the number of votes for candidate " + (i + 1) + ":"));
candidates[i] = new Election(name, votes);
}
// Determine the total number of votes
int totalVotes = 0;
for (Election candidate : candidates) {
totalVotes += candidate.getVotes();
}
// Determine the percentage of the total votes received by each candidate and the winner of the election
String winner = "";
double maxPercentage = 0.0;
for (Election candidate : candidates) {
double percentage = (double) candidate.getVotes() / totalVotes * 100;
System.out.println(candidate.getName() + " received " + candidate.getVotes() + " votes (" + percentage + "%)");
if (percentage > maxPercentage) {
maxPercentage = percentage;
winner = candidate.getName();
}
}
System.out.println("The winner of the election is " + winner);
}
}
What is the arrays about?In the above code, it is talking about a group of things called "candidates" that are being saved in a special place called an "array. " One can ask the user how long they want the list to be using JOptionPane and then make the list that long.
Also based on the code, one can also ask the user to give us information for each Election object in the array, like the name and number of votes they got, using a tool called JOptionPane.
Learn more about arrays from
https://brainly.com/question/19634243
#SPJ1
Using your knowledge of classes, arrays, and array list, write the Java code for the UML above in NetBeans. [7 marks] Write the Java code for the main method in a class called TestElection to do the following: a) Declare an array to store objects of the class defined by the UML above. Use a method from the JOptionPane class to request the length of the array from the user. [3 marks] b) Use a method from the JOptionPane class to request values from the user to initialize the instance variables of Election objects and assign these objects to the array. The array must be filled. [5 marks] c) Determine the total number of votes and the percentage of the total votes received by each candidate and the winner of the election. The sample output of your program is shown below. Use methods from the System.out stream for your output.
A _________________ is a storage area inside the CPU that is optimized for speed
Answers
A memory is a storage area inside the CPU that is optimized for speed.
What is computer memory?Memory is a computing term for a system or device that stores data for immediate use in a computer, computer hardware, or other digital electronic devices.
The terms main memory and primary storage are frequently used interchangeably. Store is a dated word for memory.
Other names for primary storage are main memory and internal memory. The program instructions, input data, and intermediate results are kept in this area of the CPU. Its size is often smaller.
Examples of primary storage include RAM (Random Access Memory) and ROM (Read Only Memory).
Thus, a storage space inside the CPU that is geared toward speed is called a memory.
For more details regarding computer memory, visit:
https://brainly.com/question/30273393
#SPJ1
__________ techniques map plaintext elements (characters, bits) into ciphertext elements. A. Transposition B. Symmetric C. Traditional D. Substitution
Answers
Answer: Substitution
Explanation: Substitution techniques: map plaintext elements (characters, bits) into ciphertext elements.
Write a program that reads numbers from the user until a blank line is entered. Your
program should display the average of all of the values entered by the user. Then
the program should display all of the below average values, followed by all of the
average values (if any), followed by all of the above average values. An appropriate
label should be displayed before each list of values.
Answers
Answer:
nums = []
while True:
in = input()
if in:
nums.append(in)
else:
break
if nums:
avg = sum(nums) / len(nums)
for i in range(len(nums)):
if nums[i] == avg:
print(f"index: {i+1}")
print(nums[i])
else:
print(-1) # if there aren't any values in nums
Explanation:
Assuming that you are coding in Python 3x. The last 'else' statement is an edge case that you might want to consider, I don't know what you want to put there, but I'm just going to leave it as -1.
Is it possible to beat the final level of Halo Reach?