Your worksheet has a column labeled Profit. When you set up the column in dollar sign and comma format, you notice there is some space to the right of the numbers. Why is this?
Answers
The extra space to the right of numbers in the Profit column is due to the alignment of the cell contents. It allows for potential negative values to be displayed without shifting the alignment of the entire column.
The extra space to the right of numbers in the Profit column is a result of the default alignment setting in spreadsheet software, which aligns numbers to the right of the cell. This setting allows for easy comparison and addition of numbers in a column. However, it also leaves extra space to the right of the number, which is especially useful for negative numbers, as it prevents the alignment of the entire column from shifting when negative numbers are displayed. This extra space can be adjusted or removed through formatting options.
learn more about cell here:
https://brainly.com/question/24271647
#SPJ11
Related Questions
Write an IF statement involving a Boolean operator (AND, OR or
the same function as
NOT) which performs
the following nested IF statement:
IF day =
"sunny"
IF temperature
20
picnic ( "Yes"
ELSE
picnic ( "No"
ENDIF
ENDIF
Answers
Answer:
i need a friend , ...............r u up?
Which character is the best choice to start a SQL injection attempt? A. Colon B. Semicolon C. Double quote. D. Single quote.
Answers
D. Single quote is the best choice to start a SQL injection attempt. It is commonly used to exploit vulnerabilities by injecting malicious SQL code, such as closing the initial query and appending additional code for unauthorized database access.
In SQL injection attacks, single quotes are typically used to manipulate SQL queries. By injecting a single quote, an attacker can terminate the original query and introduce their own malicious SQL code. This allows them to bypass input validation and perform unauthorized actions on the database, such as extracting sensitive information or modifying data. Other options like colon, semicolon, and double quote are not commonly used to initiate SQL injection attacks and may not have the desired effect of injecting malicious code.
Learn more about SQL here:
https://brainly.com/question/31663284
#SPJ11
What is a legacy database? Select the best answer from the following. O Any database with data from the time the company started its operations. O A database containing historical data. O A database that predates the relational model or any system that predates current technology, O A database that remains on-premise after the latest version has been moved to the cloud.
Answers
A legacy database is a database that predates the relational model or any system that predates current technology.
A legacy database refers to a database system that is outdated or no longer in use, typically because it predates current technology. Legacy databases may be difficult to be managed or to be integrated with newer systems due to differences in structure, format, or technology. They can also be challenging to maintain, update, or migrate to newer platforms or cloud-based solutions. Examples of legacy databases include flat file systems, hierarchical databases, and network databases, which predate the widely adopted relational database model.
Learn more about the legacy database:https://brainly.com/question/29468465
#SPJ11
Note that common skills are listed toward the top and less common skills are listed toward the bottom. According to O*NET, what are some common skills needed by Accountants? Select four options
mathematics
reading comprehension
equipment maintenance
quality control analysis
active listening
writing
Answers
Answer:
A, B, E and F Brainliest please
Explanation:
WILL GIVE BRAINLIEST!! If a flowchart has a diamond with the words “yes” and “no” to the sides of it, then it is representing a program that is a sequence.
true
false
Answers
Answer:
false
Explanation:
a flowchart with a diamond and with the words “yes” and “no” to the sides of it, then it is representing a program with branches.
it represents branch, like an if , else statement.
It is not in sequence.
Answer:
True
Explanation:
Do you think social media has negative effects on teens? Explain why or why not.
Answers
Answer:
yes and no
Explanation:
yes because some teens get addicted to social media
no because some social media is good
Answer:
Yes, Made teens feel they're living in the complete opposite of the person who's posting fun moments and happy moments as if they're living wayy better than the teen watching leading the teen to feel depressed
Explanation:
only one caption is allowed per web table, and the caption element must be listed directly after the opening _________ tag.
Answers
only one caption is allowed per web table, and the caption element must be listed directly after the opening table tag.
In web design, table captions are a way to provide context and description for tables.
Only one caption is allowed per table, and for proper structuring, the caption element must be listed directly after the opening table tag.
The opening table tag is used to define a table in HTML. By placing the caption immediately after this tag, web designers ensure that the caption is associated with the table and will be correctly interpreted by screen readers and other assistive technologies.
Captions help improve the accessibility of web tables and make them easier to understand for all users, including those with visual impairments. It is also a good practice for web designers to provide informative and concise captions that accurately describe the table content.
To learn more about web designing visit:
https://brainly.com/question/33560647
#SPJ4
the client server network strategy can handle very large networks efficiently
Answers
The client-server network strategy is a popular approach for managing large networks efficiently. In this strategy, the network is divided into two main components: the client and the server. The client refers to the user's device, such as a computer or smartphone, while the server is a powerful computer that stores and processes data.
One way this strategy handles large networks efficiently is through the distribution of resources. The server handles requests from multiple clients simultaneously, allowing for efficient use of resources. For example, in a web server-client scenario, the server can handle multiple client requests for web pages, images, or videos concurrently.
Another benefit is centralized management. With a client-server network, administrators can easily manage and control resources from a central location. Updates, security patches, and software installations can be applied to the server, which then propagates changes to the connected clients. This centralized approach saves time and ensures consistency across the network.
Additionally, client-server networks support scalability. As network demands increase, additional servers can be added to handle the load. This scalability ensures that the network remains efficient even as it grows. In summary, the client-server network strategy efficiently handles large networks through resource distribution, centralized management, and scalability.
To know more about network visit :-
https://brainly.com/question/15088389
#SPJ11
Which Microsoft virtualization product runs on Windows 7, but is no longer supported in Windows 8 and later?
a. VirtualBox
b. vSphere
c. Virtual PC
d. Hyper-V
Answers
Microsoft Virtual PC is a virtualization product that runs on Windows 7 but is no longer supported in Windows 8 and later versions.
In Windows 8 and later, Microsoft introduced a new virtualization platform called Hyper-V, replacing Virtual PC.
What is Microsoft Virtual PC?
Microsoft Virtual PC is a tool that enables users to enjoy a flexible and expansive Windows environment. It is meant to be used in conjunction with the Windows 7 operating system. Microsoft Virtual PC is a very comprehensive virtualization solution for Microsoft Windows operating system. It was introduced by Microsoft in July 2021.
To know more about Microsoft Windows:
https://brainly.com/question/1092651
#SPJ11
What are the 5 core concepts explored in the computer science standards?
Answers
Helppppp meeeeee eee
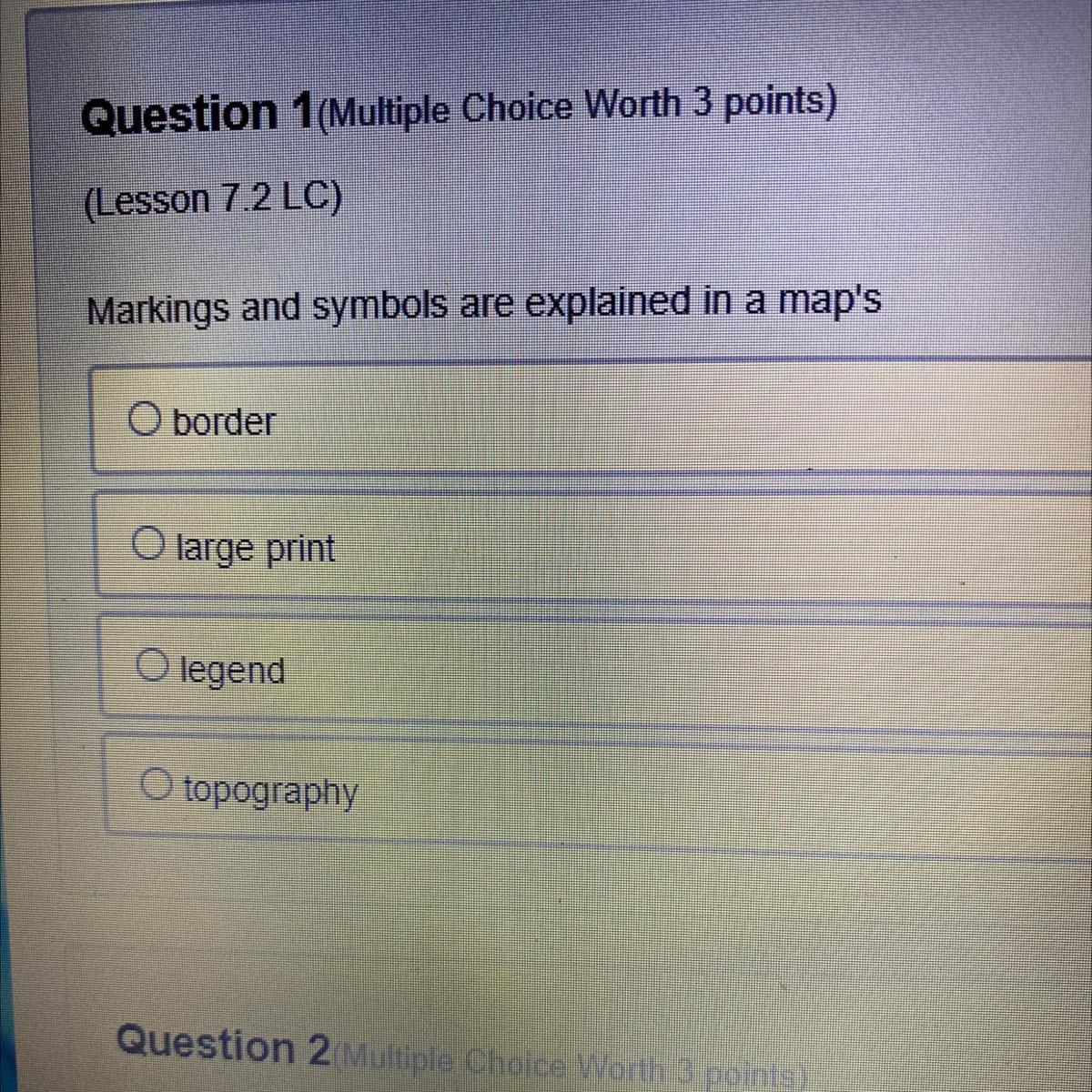
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
What is true about Electronic Business Cards in Outlook 2016? Check all that apply.
They are a way to share contact information with other users.
You can choose what is included on the business card.
You can create multiple electronic business cards.
They can be shared only with users in the organization.
You cannot send electronic business cards by email.
Answers
Answer:
A. B. C.
Explanation:
They are a way to share contact information with other users and You can choose what is included on the business card.
What is Electronic business cards?
Information exchange in the modern era is done through digital business cards.
Digital business cards, also referred to as virtual or electronic cards, are more interactive, economical, and environmentally friendly than traditional cards.
The ability to distribute digital business cards with anybody, everywhere is a big advantage. You can design your own digital business cards with on a computer, an iOS device, or an Android device.
Therefore, They are a way to share contact information with other users and You can choose what is included on the business card.
To learn more about Business card, refer to the link:
https://brainly.com/question/28850206
#SPJ2
a force of 50n acts on a body of mass 5kg. calculate acceleration produced .
Answers
Answer:
Force = 50n
mass = 5kg
Force = m * acc
50 = 5 * A
A = 50/5
A = 10 m/s^2
HOPE IT HELPS!!!
Explanation:
There are numerous data storage companies in existence today, each with their own plans to store data for different purpose and size. Let's consider a scenario where you have recently been employed by a such company called "StorageSolutions" which specializes in storing huge amount of data. Now, you have been assigned the task to store a number in a variable. The number is 51,147,483,647,321. You have different data types like Integer, Float, Char, and Double. Which data type will you use from the given data types to store the given number and why? Justify your answer with logical reasoning
Answers
Storage Solutions is one of the many data storage companies with different data storage purposes and sizes. In this scenario, you have to store a number 51,147,483,647,321 in a variable.
There are several data types available, including Integer, Float, Char, and Double. Based on the requirements, we will select the appropriate data type to store the value. Since the value is relatively large, we can rule out the Char and Integer data types.
Double data types provide greater precision than float data types and are ideal for high-precision calculations. Since the value we need to store is 51,147,483,647,321, we need a data type that can hold a larger number of digits than the Float data type can. In this situation, Double is the best data type choice for storing large numbers. Hence, we can use the Double data type to store the value.
To know more about Storage visit:
https://brainly.com/question/86807
#SPJ11
Where is a Pivot Table inserted?
a. Next to the last column of data in your worksheet
b. Below the last row of data in your worksheet
c. It depends on whether you select to insert the Pivot Table in the current worksheet or a new worksheet
d. Above the first row of data in your worksheet
Answers
The Create PivotTable dialog box will prompt you to create a Pivot Table on an Existing Worksheet if you insert one on a data-filled worksheet. One of the options in the Create PivotTable dialog box is this one.
Utilized in spreadsheet applications like Excel, OpenOffice.org Calc, and Ggle Sheets is a data summarization tool called a pivot table. Sorting, counting, and totaling data in a table are its primary uses. In order to create a report, you can summarize the data in a variety of ways using a pivot table.
The dialog box for "Create PivotTable":
In Excel, a new pivot table can be created using the dialog box labeled "Create PivotTable."
Learn more about PivotTable at
brainly.com/question/18410166
#SPJ4
possible paper orientations for printing a worksheet are landscape and . select one: a. preview b. portrait c. normal d. page break
Answers
The possible paper orientations for printing a worksheet are landscape and portrait.
The possible paper orientations for printing a worksheet are landscape and portrait.
Landscape orientation means that the paper is oriented horizontally, so the width is greater than the height. This is useful when you have a worksheet that has a lot of columns, because it allows you to fit more columns on a single page. You can imagine turning a piece of paper sideways, so that the long edge is at the top and bottom.Portrait orientation, on the other hand, means that the paper is oriented vertically, so the height is greater than the width. This is useful when you have a worksheet that has a lot of rows, because it allows you to fit more rows on a single page. To print a worksheet in landscape or portrait orientation, you will need to adjust the Page Setup options in your printing settings. This will allow you to choose the orientation that best suits your worksheet.Know more about the Portrait orientation
https://brainly.com/question/14997923
#SPJ11
computer programs that are designed to erase files or compromise data integrity are called
Answers
The computer programs that are designed to erase files or compromise data integrity are called malware.
Malware is a short form of "malicious software," which is a program or code that aims to harm computers and networks. Malware is typically deployed by cybercriminals and can range from simple to sophisticated software programs. Malware, in general, is used to destroy or steal sensitive data, destroy networks, and ransomware that encrypts data in return for payment.
The following are the four primary types of malware:
Virus - A virus is a form of malware that infects a system by modifying the code of another program. When the victim program runs, the virus code executes, infecting the computer. The virus code can self-replicate and spread to other computers through email, messaging, and file-sharing networks.
Trojan - A Trojan is a program that is disguised as a legitimate application but performs malicious activities when installed. Trojan horses are distributed via email attachments, downloads, and other deceptive methods.
Worm - A worm is a standalone malware program that does not need to be attached to a host program to function. It can spread through networks, operating systems, and other communication pathways without human intervention.
Adware - Adware is an advertising software that appears on websites, browsers, or other apps. Adware collects and transmits user data to advertisers for targeted marketing purposes.
To learn more about malware visit : https://brainly.com/question/399317
#SPJ11
how could the seven-segment display driver be designed using a 4-to-16 decoder and logic gates rather than multiplexers?
Answers
A digital combinational logic circuit known as a digital or binary decoder can change one kind of digital code into another.
A particular decoder called a BCD to 7-segment display decoder may change binary coded decimals into a format that can be easily viewed on a 7-segment display. Four binary weighted address inputs (A0 to A3) are decoded to produce sixteen mutually exclusive outputs (Y0 to Y15). The device has two inputs that are input enable (E0 and E1). The outputs are forced to be HIGH when either input is HIGH. In order to break down any combination of inputs into a set of terms that are all set to "0" except for one term, decoders are just a group of logic gates that are organized in a specified fashion.
Learn more about input here-
https://brainly.com/question/13014455
#SPJ4
What is an Array known as in Python?
Answers
Arrays are an essential component of the majority of programming languages and a fundamental data structure. They are containers in Python that can store multiple items simultaneously. In particular, they are a logical collection of values belonging to the same data type for each one.
In particular, they are a logical collection of values belonging to the same data type for each one. The fact that Python arrays can only hold a sequence of multiple items of the same type is the most important thing to keep in mind about them.
The Python programming language supports lists, whereas arrays do not. Because they are not a built-in data structure, arrays cannot be used without being imported through the array module. When working with homogeneous data, the array module's arrays are useful because they act as a thin wrapper for C arrays.
They are also smaller and use less memory and space, making them more space- and size-efficient than lists. NumPy arrays should be used to carry out mathematical calculations by importing the NumPy package. Aside from that, lists work in a similar manner and are easier to use, so you should only use them when absolutely necessary.
Learn more about Array at
https://brainly.com/question/19570024
Using the flowchart below, what value when entered for Y will generate a mathematical error and prevent our flowchart from being completely executed? 3 0 1 None of these values will produce a mathematical error

Answers
Answer:
The answer is the last choice that is "None of these values will produce a mathematical error".
Explanation:
In this question, the above given choice correct because neither of the flowchart procedures could trigger a mathematical error. This error could not be induced by multiplication, addition and subtraction, and the only division by 15. It is the only divide by 0, that's why the above flowchart will produce a mathematical error.
Which blu-ray standard defines rewritable disks?
Answers
The blu-ray standard that defines rewritable disks is BD-RE.
What is a rewritable disk?It should be noted that a rewritable disk simply means an erasable disk that can be reused.
In this case, the blu-ray standard that defines rewritable disks is BD-RE. It is the recordable standard.
Learn more about disks on:
brainly.com/question/20381259
#SPJ12
The goal of a system is to
a) be natural or human-made
b) use energy
c) perform a task
d) be social or physical
Answers
Answer:
d it is d I know cause I answered it on a test I had
hope it helps
give three reasons why csma/cd cannot be used in wireless communication
Answers
Answer:
CSMA/CD (Carrier Sense Multiple Access with Collision Detection) is a media access control (MAC) protocol that is widely used in wired Ethernet networks. However, it cannot be used in wireless communication due to the following reasons:
Hidden Terminal Problem: In wireless communication, it is possible that two devices that are out of each other's range may both try to transmit at the same time, causing a collision. This is known as the hidden terminal problem, and CSMA/CD cannot detect it.
Exposed Terminal Problem: In contrast to the hidden terminal problem, in some wireless communication scenarios, a device may refrain from transmitting even when it is allowed to do so, because it senses that another device is transmitting even though it is far enough away to avoid interfering. This is known as the exposed terminal problem, and CSMA/CD may unnecessarily hold off transmissions in this case.
No Physical Carrier: In wired communication, CSMA/CD relies on detecting collisions by sensing the physical carrier (the wire) for traffic. In wireless communication, there is no physical carrier to detect collisions, and thus the collision detection component of CSMA/CD cannot be implemented.
As a result of these limitations, other MAC protocols such as CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) are used in wireless communication to mitigate the hidden and exposed terminal problems and ensure reliable data transmission.
Explanation:
CSMA/CD (Carrier Sense Multiple Access/Collision Detection) is a protocol that is commonly used in wired Ethernet networks to avoid data collisions. However, it is not suitable for wireless communication due to several reasons.
Three reasons why CSMA/CD (Carrier Sense Multiple Access with Collision Detection) cannot be used in wireless communication are:
1. Hidden Node Problem:
In wireless communication, two devices may be unable to directly detect each other's signals due to obstacles or distance, but can still communicate with a common access point. CSMA/CD relies on the ability to detect collisions from all devices on the network, but in this case, the devices cannot detect each other's transmissions, leading to potential collisions that go undetected.
2. Fading and Signal Attenuation:
Wireless signals are subject to signal attenuation, which means their strength decreases as they travel through the air and encounter obstacles. This makes it difficult for devices in a wireless network to accurately detect collisions and determine when the channel is clear for transmission, reducing the effectiveness of CSMA/CD.
3. Increased Overhead and Inefficiency:
In a wireless network, CSMA/CD would require continuous monitoring of the channel for collision detection. This can lead to increased overhead and decreased efficiency in wireless communication, as devices would need to spend more time and energy monitoring the channel instead of focusing on data transmission.
In summary, CSMA/CD cannot be used in wireless communication due to the hidden node problem, signal fading and attenuation, and increased overhead and inefficiency.
To learn more about CSMA/CD visit : https://brainly.com/question/30562918
#SPJ11
Question 17/20
The process for maturing an idea towards patentability is called:
Select the correct option(s) and click submit.
Freedom to Operate
MCD
Trademarking
CIM
Submit
Answers
The process for maturing an idea towards patentability is called: CIM.
An intellectual property can be defined as an intangible and innovative creation of the mind that is solely dependent on human intellect (intelligence).
Hence, an intellectual property is an intangible creation of the human mind, ideas, thoughts or intelligence.
Globally, there are three (3) main ways to protect an idea or intellectual property and these include:
Trademarks.Copyright.Patents.A patent can be defined as the exclusive (sole) right granted to an inventor by a sovereign authority such as a government, which enables him or her to manufacture, use, or sell an invention (idea) for a specific period of time.
Generally, patents are used on an idea or innovation for products that are manufactured through the application of various technologies.
CIM is an acronym for collaborative invention mining and it can be defined as the process for maturing an idea towards patentability, especially through collaborative interaction..
Thus, the objective of collaborative invention mining (CIM) is to collectively strengthen, mature and develop an idea to become a tangible product that proffers a solution to a problem, thereby, making it patentable.
Read more: https://brainly.com/question/22374164
What serves as a safety device on the FMU-124A/B?
Answers
The FMU-124A/B is a type of bomb fuse used in various military aircraft. It is designed to provide reliable and precise detonation of bombs in different conditions and scenarios. One crucial feature of the FMU-124A/B is its safety mechanism, which is called a Safe/Arm device.
The Safe/Arm device on the FMU-124A/B serves as a safety mechanism that prevents accidental or premature detonation of the bomb during handling or transport. It consists of a mechanical switch that must be physically moved to the "armed" position before the bomb can be detonated. The Safe/Arm device ensures that the bomb is only armed when it is in the desired location and conditions, such as when it has been released from the aircraft and is on a trajectory towards its intended target.
In addition to the mechanical switch, the FMU-124A/B also has other safety features, such as environmental sensors that monitor temperature, pressure, and humidity. These sensors ensure that the Safe/Arm device remains in the "safe" position until the bomb is in the appropriate environment for use.
Overall, the Safe/Arm device on the FMU-124A/B is a critical safety feature that ensures the bomb is only armed and detonated in the intended location and conditions, preventing accidental or premature detonation that could cause harm to personnel and equipment.
Learn more about sensors here:
https://brainly.com/question/29738927
#SPJ11
Write the method drawSquare below.
/** Precondition: 0 ≤ x < 10, 0 < y ≤ 10, and len > 0.
* Draws a square on a 10-by-10 xy-coordinate grid
* and prints the square’s side length and area.
* The upper left corner of the square will be located
* at the coordinate (x, y) and the side length of the * square will be len (or as large as will fit in the grid).
*/
public void drawSquare(int x, int y, int len)
Answers
The method drawSquare is an illustration of functions; functions are named program statements that are executed when called
The method drawSquareThe method drawSquare written in Java, where comments are used to explain each action is as follows:
//This defines the function
public static void drawSquare(int x, int y, int len) {
//This checks if x + len exceeds 10
if(x+len>10){
len = 10-x;}
//This checks if y + len exceeds 10
if(y+len>10){
len = 10-y;}
//The next four lines draw the square
drawLine(x, y, x+len, y);
drawLine(x+len,y,x+len,y-len);
drawLine(x+len, y-len, x, y-len);
drawLine(x, y-len, x, y);
}
Read more about java programs at:
https://brainly.com/question/19271625
a language translator is a ???
Answers
Answer:
Explanation:
speech program
Answer:
hi
Explanation:
language translator is a program which is used to translate instructions that are written in the source code to object code i.e. from high-level language or assembly language into machine language.
hope it helps
have a nice day
Can anyone re-write this code in a way that still works but looks different to the reader? It is a single-player Tic Tac Toe game.
board = [' ' for x in range(10)]
def insertLetter(letter, pos):
board[pos] = letter
def spaceIsFree(pos):
return board[pos] == ' '
def printBoard(board):
print(' | |')
print(' ' + board[1] + ' | ' + board[2] + ' | ' + board[3])
print(' | |')
print('-----------')
print(' | |')
print(' ' + board[4] + ' | ' + board[5] + ' | ' + board[6])
print(' | |')
print('-----------')
print(' | |')
print(' ' + board[7] + ' | ' + board[8] + ' | ' + board[9])
print(' | |')
def isWinner(bo, le):
return (bo[7] == le and bo[8] == le and bo[9] == le) or (bo[4] == le and bo[5] == le and bo[6] == le) or(bo[1] == le and bo[2] == le and bo[3] == le) or(bo[1] == le and bo[4] == le and bo[7] == le) or(bo[2] == le and bo[5] == le and bo[8] == le) or(bo[3] == le and bo[6] == le and bo[9] == le) or(bo[1] == le and bo[5] == le and bo[9] == le) or(bo[3] == le and bo[5] == le and bo[7] == le)
def playerMove():
run = True
while run:
move = input('Please select a position to place an \'X\' (1-9): ')
try:
move = int(move)
if move > 0 and move < 10:
if spaceIsFree(move):
run = False
insertLetter('X', move)
else:
print('Sorry, this space is occupied!')
else:
print('Please type a number within the range!')
except:
print('Please type a number!')
def compMove():
possibleMoves = [x for x, letter in enumerate(board) if letter == ' ' and x != 0]
move = 0
for let in ['O', 'X']:
for i in possibleMoves:
boardCopy = board[:]
boardCopy[i] = let
if isWinner(boardCopy, let):
move = i
return move
cornersOpen = []
for i in possibleMoves:
if i in [1,3,7,9]:
cornersOpen.append(i)
if len(cornersOpen) > 0:
move = selectRandom(cornersOpen)
return move
if 5 in possibleMoves:
move = 5
return move
edgesOpen = []
for i in possibleMoves:
if i in [2,4,6,8]:
edgesOpen.append(i)
if len(edgesOpen) > 0:
move = selectRandom(edgesOpen)
return move
def selectRandom(li):
import random
ln = len(li)
r = random.randrange(0,ln)
return li[r]
def isBoardFull(board):
if board.count(' ') > 1:
return False
else:
return True
def main():
print('Welcome to Tic Tac Toe!')
printBoard(board)
while not(isBoardFull(board)):
if not(isWinner(board, 'O')):
playerMove()
printBoard(board)
else:
print('Sorry, O\'s won this time!')
break
if not(isWinner(board, 'X')):
move = compMove()
if move == 0:
print('Tie Game!')
else:
insertLetter('O', move)
print('Computer placed an \'O\' in position', move , ':')
printBoard(board)
else:
print('X\'s won this time! Good Job!')
break
if isBoardFull(board):
print('Tie Game!')
while True:
answer = input('Do you want to play again? (Y/N)')
if answer.lower() == 'y' or answer.lower == 'yes':
board = [' ' for x in range(10)]
print('-----------------------------------')
main()
else:
break
Answers
The re-written program for the Tic Tac Toe game is given as follows:
board = [' ' for _ in range(10)]
def insert_letter(letter, pos):
board[pos] = letter
def space_is_free(pos):
return board[pos] == ' '
def print_board(board):
print(' | |')
print(' ' + board[1] + ' | ' + board[2] + ' | ' + board[3])
print(' | |')
print('-----------')
print(' | |')
print(' ' + board[4] + ' | ' + board[5] + ' | ' + board[6])
print(' | |')
print('-----------')
print(' | |')
print(' ' + board[7] + ' | ' + board[8] + ' | ' + board[9])
print(' | |')
def is_winner(bo, le):
return (bo[7] == le and bo[8] == le and bo[9] == le) or (bo[4] == le and bo[5] == le and bo[6]
What is a Tic Tac Toe Game?Tic-tac-toe, also known as noughts and crosses or Xs and Os, is a two-person paper-and-pencil game in which each player takes turns marking the spaces in a three-by-three grid with an X or an O.
The winner is the player who successfully places three of their markers in a horizontal, vertical, or diagonal row.
Learn more about games:
https://brainly.com/question/3863314
#SPJ1
what mode do you use to extract split or reshape your red Builder brush
Answers
Answer:
what the hell is a red builder brush???
You can use artificial lighting when rendering a view. When the dimming value of a light fitting is set to 1, what does that do within the render?
Answers
When rendering a view, artificial lighting can be used to achieve a specific look or mood. The dimming value of a light fitting determines the brightness of the light, with 1 being the highest level of brightness.
When the dimming value is set to 1, the light fitting will emit its maximum brightness in the render, creating a brighter and more illuminated scene. This can be useful for highlighting certain features or objects within the view, or simply for creating a well-lit and visually appealing scene. Overall, understanding how to manipulate artificial lighting and dimming values is crucial for achieving the desired look and feel in a rendered view.
learn more about rendering a view here:
https://brainly.com/question/17405314
#SPJ11