a hacker who changed the voice mail greeting of a company to say that it is offering free products by asking customers to dial a different phone number to claim their gifts is engaging in
Answers
A man-in-the-middle (MitM) attack is a sort of cyberattack in which communications between two parties are intercepted, frequently with the goal of stealing login credentials by a hacker .
What does unlawful data copying involve?Employees stealing confidential or sensitive information Employee data theft, also known as insider data theft, happens when a current or former employee of a corporation steals sensitive or secret data for personal gain or to harm the organization.
Which of the following qualifies as a malevolent hacker?Black hat hackers, often known as crackers, are malicious hackers. Black hats are unethical, occasionally break the law, hack into computer systems with malicious intent, and may compromise the confidentiality, integrity, or accessibility of an organization's systems and data.
To know more about a hacker visit :-
https://brainly.com/question/30141575
#SPJ4
Related Questions
high speed easily accessible storage space used by the cpu
Answers
High-speed easily accessible storage space used by the CPU is known as Cache memory. This is a type of volatile computer memory that improves the computer's performance by reducing the time required to access data from the primary storage by temporarily storing frequently used data closer to the CPU.
Cache memory is located in the CPU's chip, making it quicker to access than main memory or disk storage. It can be categorized into three different levels, L1, L2, and L3, with L1 being the smallest and fastest and L3 being the biggest and slowest.The CPU cache's size determines the amount of data that can be stored in it, with larger caches resulting in quicker data access times. A cache miss occurs when the requested data is not found in the cache, and the CPU must look for it in the main memory, resulting in a latency penalty.The use of cache memory is essential for modern-day computer systems. It provides a faster way of accessing data, which makes the computer more responsive. The CPU utilizes this high-speed storage to temporarily store the frequently used data, reducing the need to access the main memory, which takes longer to access and slows down the system. Therefore, cache memory improves the computer's performance by reducing the latency penalty that occurs when data is fetched from the main memory.
In summary, cache memory is an essential component of a computer system that improves its performance by providing a high-speed easily accessible storage space for frequently used data.
For more details regarding cache memory, visit:
brainly.com/question/23708299
#SPJ11
What are the differences between online platforms sites and content?.
Answers
Websites offer one-way interaction, with visitors taking in whatever content is presented.
Platforms provide reciprocal engagement, with user interactions resulting in individualized experiences. Marketplaces, search engines, social media, blogs, app stores, communications services, payment systems, services included in the so-called "collaborative" or "gig" economy, and many more online services have all been referred to as "online platforms." A digital service known as an online platform makes use of the Internet to enable communications between two or more dissimilar but related users. Platforms are locations where electronic demand and supply collide.
Learn more about communication here-
https://brainly.com/question/14809617
#SPJ4
select all statements that are true about html: question 15 options: html can be used to create only static web pages; it can not create a dynamic web page. html can easily integrate with other languages and is easy to develop. html provides a high level of security. html displays content according to the window size or the device. html language is not centralized.
Answers
The true statements about HTML are the following:
1. HTML can be used to create only static web pages; it cannot create a dynamic web page.
2. html can easily integrate with other languages and is easy to develop.
3. HTML provides a high level of security.
4. HTML displays content according to the window size or the device.
What are the true statements?The true statements about HTML include the fact that it is only used in creating static web pages. The kinds of ages developed by this language are not high level so dynamic interactions might be difficult.
Also, this language can be easily integrated with other languages and it is not hard to develop. It also has a good level of security.
Learn more about HTML Here:
https://brainly.com/question/4056554
#SPJ1
ANSWER ASAP!!!!
Collect ten examples of design which use good layout and composition principles.
On a separate sheet of paper, answer the following questions for each example:
What kind of object is the example
Who is the intended audience for this design
Where does this design appear
What is the topic of this design
What is effective about the design’s layout and composition
Create a citation sheet listing all sources used.
Answers
Here are ten instances of design that demonstrate effective geography and composition standard.
Examples of designThese designs include a magazine cover, site homepage, book cover, poster, menu, infographic, output packaging, business card, sign, and social publishing post.
Each design targets a specific hearing and appears in various regions, such as newsstands, bookstores, public scopes, and online platforms.
The fields range from politics, e-commerce, and novel to food, touristry, and fashion. Effective layouts incorporate clear hierarchy of facts, attention-grabbing metaphors, bold typography, and use of negative scope.
These examples were culled from popular design websites such as Behance, Dribbble, Canva, Designspiration, Awwwards, and Smashingmagazine.
Read more about design here:
https://brainly.com/question/21422013
#SPJ1
quick and easy points how is this wrong Ap computer science?

Answers
The correct answer to the given question is Strings and not Variables.
This is because in JavaScript, the use of Strings is enclosed between a pair of either single quotation marks '' or double quotation marks "" and there is no difference between using double or single quotes, as they both serve the same function.
What is a String?This refers to a linear sequence of characters, words, or other data and is a literal constant or variable
Hence, we can see that The correct answer to the given question is Strings and not Variables.
This is because in JavaScript, the use of Strings is enclosed between a pair of either single quotation marks '' or double quotation marks "" and there is no difference between using double or single quotes, as they both serve the same function.
Read more about strings in programming here:
https://brainly.com/question/15683939
#SPJ1
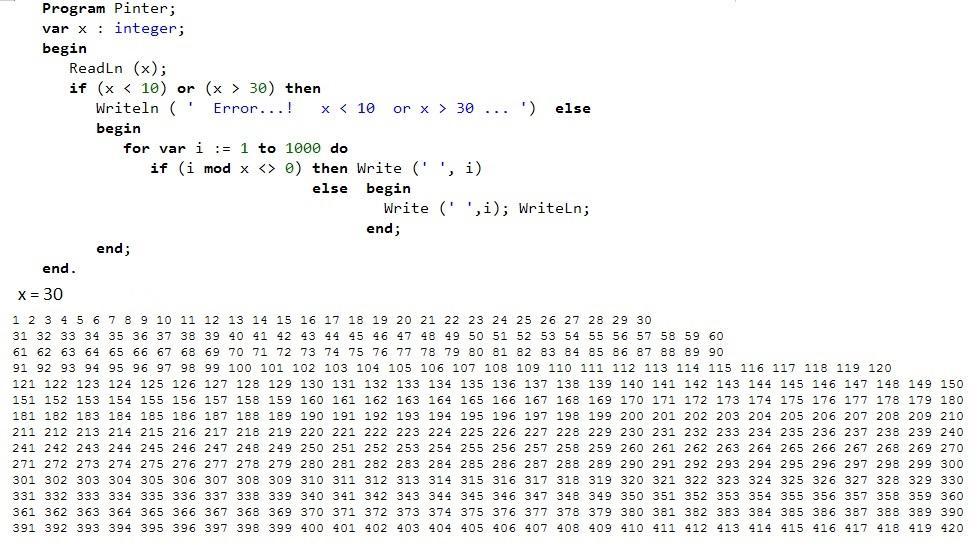
write a program which asks the user for an integer x. the program then outputs the values from 1 to 1000 as x numbers per line, where x is the value that the user entered. you must use only 1 loop for this. validate x to make sure that the numbers per line value is between (10 to 30).
Answers
Answer:
Explanation:
PascalABC
Program and Result:
Program Pinter;
var x : integer;
begin
ReadLn (x);
if (x < 10) or (x > 30) then
Writeln ( ' Error...! x < 10 or x > 30 ... ') else
begin
for var i := 1 to 1000 do
if (i mod x <> 0) then Write (' ', i)
else begin
Write (' ',i); WriteLn;
end;
end;
end.

The program could be written as follows (in Python):
# Prompt user for input and validate x
x = int(input("Enter the numbers per line (between 10 and 30): " ))
# Validate x to ensure it is between 10 and 30
if x < 10 or x > 30:
print("Invalid input. Please enter a value between 10 and 30.")
else:
count = 0 # Counter to keep track of numbers per line
# Loop from 1 to 1000
for i in range(1, 1001):
# Print the current number with a space
print(i, end=" ")
# Increment the count
count += 1
# Check if count reaches x (numbers per line)
if count == x:
print() # Move to the next line
count = 0 # Reset the count
How to write this program?We can write a Python program that fulfills the requirements you mentioned:
# Prompt user for input and validate x
x = int(input("Enter the numbers per line (between 10 and 30): " ))
# Validate x to ensure it is between 10 and 30
if x < 10 or x > 30:
print("Invalid input. Please enter a value between 10 and 30.")
else:
count = 0 # Counter to keep track of numbers per line
# Loop from 1 to 1000
for i in range(1, 1001):
# Print the current number with a space
print(i, end=" ")
# Increment the count
count += 1
# Check if count reaches x (numbers per line)
if count == x:
print() # Move to the next line
count = 0 # Reset the count
In this program, we prompt the user to enter the value for "numbers per line" (x) using the input function. We then validate the input to ensure that x is between 10 and 30 using an if statement.
If x is within the valid range, we initialize a count variable to keep track of the numbers per line. Then we use a single loop to iterate from 1 to 1000. Within the loop, we print each number followed by a space using print(i, end=" ").
After printing a number, we increment the count by 1. If the count reaches the value of x, we move to the next line by printing an empty print() statement, and we reset the count to 0.
Learn more about programs at:
https://brainly.com/question/23275071
#SPJ2
what is technology in computer
Answers
Answer:
she is right or he :)
Explanation:
Answer:
well its somthing
Explanation:
What is your favorite cool math games game?
Answers
Answer:
Explanation:
me cars 3 to like 7
Answer:
my favorite game is there is no game
Explanation:
Write an LMC program as follows instructions:
A) User to input a number (n)
B) Already store a number 113
C) Output number 113 in n times such as n=2, show 113
113.
D) add a comment with a details exp
Answers
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
The LMC program can be written as follows:
sql
Copy code
INP
STA 113
INP
LDA 113
OUT
SUB ONE
BRP LOOP
HLT
ONE DAT 1
Explanation:
A) The "INP" instruction is used to take input from the user and store it in the accumulator.
B) The "STA" instruction is used to store the number 113 in memory location 113.
C) The "INP" instruction is used to take input from the user again.
D) The "LDA" instruction loads the value from memory location 113 into the accumulator.
E) The "OUT" instruction outputs the value in the accumulator.
F) The "SUB" instruction subtracts 1 from the value in the accumulator.
G) The "BRP" instruction branches back to the "LOOP" label if the result of the subtraction is positive or zero.
H) The "HLT" instruction halts the program.
I) The "ONE" instruction defines a data value of 1.
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
To know more about LMC program visit :
https://brainly.com/question/14532071
#SPJ11
If you have a collection of related attributes that can be considered a subtheme for one of the entities and you remove it, what form is the database now in?
A. Third normal
B. Second normal
C. Fourth normal
D. First normal
Answers
Answer:
If you have a collection of related attributes that can be considered a subtheme for one of the entities and you remove it, the form of the database is now in Second Normal Form (2NF).
Explanation:
In the Second Normal Form, the table is in 1st Normal Form and all non-key attributes are fully dependent on the primary key. It means that the table does not contain any partial dependency, which is when a non-key attribute is dependent on only a part of the primary key and not the entire key.
A database that is in 2NF has been stripped of all attributes that do not depend on the primary key, which is the subtheme that you have removed.
A database in third normal form (3NF) has no transitive dependency.
A database in fourth normal form (4NF) has no multi-valued dependency.
A database in first normal form (1NF) has no repeating groups.
Why is it important to use only the training set to identify the features to be dropped? Explain how stable machine learning libraries such as scikit-learn facilitate this.
Answers
When dealing with data sets, it is crucial to split the dataset into training and test sets. This is important for machine learning models because the performance of the model on unseen data is usually the objective.To make sure that the model learns from the data in the best possible way, it is critical to use only the training data to identify the features to be dropped. This is because the test set is used to evaluate the model's ability to generalize, and using the test set for feature selection would introduce data leakage.
This means that the model will have access to information from the test set, and it may be overfitted or biased toward the test data.The scikit-learn library provides several tools that make feature selection and model training a straightforward process. The library implements a variety of feature selection techniques, such as Recursive Feature Elimination (RFE), SelectKBest, and SelectPercentile, that can be used to reduce the dimensionality of the data. These methods work by ranking the features based on some criteria, such as mutual information or correlation, and then selecting the top-ranked features.Another feature of scikit-learn that aids in the stability of machine learning models is cross-validation.
Cross-validation allows the model's performance to be evaluated using multiple train-test splits of the data, reducing the risk of overfitting to a particular training set. It also aids in the selection of the best model hyperparameters by comparing the model's performance across different parameter combinations.In conclusion, the use of only the training set for feature selection is critical to ensure that the machine learning model learns to generalize and does not overfit the data. The scikit-learn library provides tools such as feature selection techniques and cross-validation to aid in the stability of machine learning models.
To know more about performance visit:-
https://brainly.com/question/30164981
#SPJ11
Activating the ______ will make the trigger stay in the operating mode even when it is released.
Answers
Answer:
Trigger lock
Explanation:
(04.01 LC)
An if statement tells the computer when a certain condition is true; the computer should execute the block
of code within it. (5 points)
A. True
B. False
Answers
For example, the code
if(x > 5)
{
y = 10;
}
will check to see if x is larger than 5. If so, then it assigns the number 10 to the variable y. If x is not larger than 5, then everything in the curly braces is not executed and it skips over this section.
Answer:
True
Explanation:
How is the bandwidth of a network measured?
Answers
Answer:
Bandwidth is measured as the amount of data that can be transferred from one point to another within a network in a specific amount of time.
Explanation:
How do you resolve you have uncommitted work pending Please commit or rollback before calling out?
Answers
In order to resolve this issue, you need to either commit or rollback the pending work. Committing the pending work will save the changes to the database.
What is database ?A database is a collection of data that is organized in a structured format and stored in a computer system. It is typically used to store, retrieve and manipulate data. Databases are used for a variety of purposes, including recording customer information, storing financial records, and tracking inventory. A typical database contains tables, fields, records, and indexes, which are used to store and organize the data. Database management systems (DBMS) are responsible for managing the data and providing access to users. These systems provide various tools, such as query languages, forms, and reports, to assist in manipulating and retrieving the data.
To learn more about database
https://brainly.com/question/28033296
#SPJ4
What button is used to replicate amounts across several
months in the budget worksheet?
Answers
In the context of a budget worksheet, there isn't a specific universal button that is used to replicate amounts across several months.
What is the feature in the worksheet?However, most spreadsheet software like Microsoft Excel or G o o gle Sheets provide features that allow you to copy and paste formulas or values across multiple cells or ranges.
To replicate amounts across several months in a budget worksheet, you can use techniques such as filling formulas or dragging the cell with the formula across the desired range of cells.
Alternatively, you can use functions like the Fill Series or AutoFill to quickly populate the desired cells with the replicated amounts.
Read more about worksheets here:
https://brainly.com/question/32563659
#SPJ4
A computer _________ is any person whose primary occupation involves the design, configuration, analysis, development, modification, testing, or security of computer hardware or software.
Answers
Answer:
Engineering
Explanation:
Because they are the one who create software applications
what tells the hardware what to do and how to do it?
Software
Hard drive (Hdd)
hardware
Cpu
Answers
Answer:
I think its CPU
Explanation:
The method getValueFromFile is public and returns an int. It accepts no arguments. The method is capable of throwing an IOException and a FileNotFoundException. Write the header for this method.
Answers
The method header is an illustration of java programs
The definitions of the method header are:
public int getValueFromFile()public static int getValueFromFile()How to determine the header of the method?From the question, we have the following parameters:
Method name: getValueFromFile Modifier: publicReturn type: intNumber of arguments = 0The syntax to define the header of a method is:
modifier return-type method-name (argument-list)
Using the above syntax, the definition of the method header is:
public int getValueFromFile()
It can also be written as:
public static int getValueFromFile()
Read more about java programs at:
https://brainly.com/question/18554491
Explain how the advancements in computer hardware and decrease in hardware costs has impacted the use of business utilizing Big Data? .
Answers
Advancements in computer hardware and decreased hardware costs have significantly impacted businesses utilizing Big Data.
What has this development led to?These developments have allowed organizations to handle and process larger volumes of data at a faster pace, enabling more sophisticated analysis and insights.
Improved processing power and increased storage capacity have made it feasible to store and analyze massive datasets, enabling businesses to extract valuable information and make data-driven decisions. Lower hardware costs have also reduced barriers to entry, making Big Data technologies more accessible to smaller organizations.
Read more about Big Data here:
https://brainly.com/question/28333051
#SPJ4
Which option is a temporary storage area in memory that is created to hold data?
O subprocedure
O variable
O function
O module
Answers
If you want to stop a loop before it goes through all of its iterations, the break statement may be used. Group of answer choices True False
Answers
Answer:
Answer is true
Explanation:
Lillian is creating a presentation about social media and she would like to include transitions to add flair. What does she need to do to make sure her transitions are balanced?
Apply one simple transition to all of her slides.
Use a different transition for each slide.
Add a subtle transition to every other slide.
Give each slide a different duration time.
Answers
Answer:
A: Apply one simple transition to all of her slides.
Explanation:
I got it correct on a quiz I did that had this question.
HURRY PLEASE
The software that allows programmers to write and run code is called an IDE True O False
Answers
Explanation:
true
................
Answer:
False
Explanation:
Hope this helps.
Which disk interface technology transfers data over a parallel bus?
a. SATA
b. USB
c. SAS
d. SCSI
Answers
Answer: d, Small Computer System Interface.
Explanation:
The disk interface technology that transfers data over a parallel bus is the Small Computer System Interface (SCSI).
Among the options provided, SATA (Serial ATA), USB (Universal Serial Bus), and SAS (Serial Attached SCSI) are all serial interfaces, meaning they transfer data bit by bit sequentially. On the other hand, SCSI is a parallel interface that transfers data in parallel, utilizing multiple data lines simultaneously.
SCSI was one of the earliest disk interface technologies and was commonly used in high-performance computing environments. It allowed for faster data transfer rates compared to its serial counterparts. SCSI devices, including hard drives and tape drives, were connected to the computer using a SCSI host adapter, which typically had a parallel bus interface. This parallel bus enabled multiple data signals to be sent simultaneously, increasing the overall throughput.
However, it's worth noting that as technology has advanced, serial interfaces like SATA and SAS have become more prevalent in modern storage systems due to their advantages in terms of simplicity, cost-effectiveness, and compatibility with smaller form factors. Nonetheless, SCSI remains a legacy technology that played a significant role in the history of disk interfaces.
learn more about disk interface here:
https://brainly.com/question/32254091
#SPJ11
you use chrome as your web browser on the desktop computer in your dorm room. because you're concerned about privacy and security while surfing the web, you decide to block pop-ups from banner ad companies. however, you still want the computer to accept pop-ups from legitimate sites, such as your bank's website. you also want to block location tracking and third-party cookies in the browser. your task in this lab is to configure the content settings in chrome as follows:
Answers
To configure the content settings in Chrome to block pop-ups from banner ad companies, allow pop-ups from legitimate sites, block location tracking, and block third-party cookies, follow these steps:
1. Open Chrome and click on the three dots in the top right corner of the browser window.
2. Select "Settings" from the drop-down menu.
3. Scroll down to the "Privacy and security" section and click on "Site Settings".
4. Under the "Permissions" section, click on "Pop-ups and redirects".
5. Toggle the switch to "Blocked (recommended)" to block pop-ups from banner ad companies.
6. Click on "Add" next to "Allow" to add legitimate sites that you want to allow pop-ups from, such as your bank's website.
7. Go back to the "Site Settings" page and click on "Location" under the "Permissions" section.
8. Toggle the switch to "Blocked" to block location tracking.
9. Go back to the "Site Settings" page and click on "Cookies and site data" under the "Permissions" section.
10. Toggle the switch next to "Block third-party cookies" to block third-party cookies in the browser.
By following these steps, you can configure the content settings in Chrome to block pop-ups from banner ad companies, allow pop-ups from legitimate sites, block location tracking, and block third-party cookies.
Learn more about Chrome:
https://brainly.com/question/29668247
#SPJ11
Which type of system is not proprietary?
Answers
Nonproprietary software is open source and accessible for free download and usage. It also makes its source code completely available. Software that is not proprietary can also be referred to as open-source.
Due to the fact that Linux and Android are not proprietary, there are several variations of both operating systems. A system, tool, or program that is solely owned by an organization is referred to as proprietary technology. In most cases, the proprietor develops and employs them domestically in order to manufacture and offer goods and services to clients. From the foregoing, it can be inferred that Microsoft Windows is an example of proprietary system software. Linux is an open-source, free operating system that was made available under the GNU General Public License (GPL). The source code may be used, examined, altered, and distributed by anybody, and they may even sell copies of the altered code. computer operating system that is specific to a certain class of computers
Learn more about software here:
https://brainly.com/question/1022352
#SPJ4
you are having a hard day at work, but you have to make several phone calls. what can you do to make sure your voice projects a friendly tone? leave a short, curt voice mail message.
Answers
Since you are having a hard day at work, but you have to make several phone calls. The thing that you could do to make sure your voice projects a friendly tone is option C: Avoid talking on the phone.
What can you do to ensure that your voice carries a welcoming tone?The listener's ability to comprehend your message is the most crucial component of a voicemail. Don't mumble, and make sure to talk properly and aloud. Speaking softly will make it difficult for the listener to comprehend you and may prevent them from calling you back. Hence, this is not advisable in the above situation.
Note that End statements with a lower tone and queries with a higher pitch. It will appear like you don't believe what you just stated if you end sentences with a high pitch. Changing your voice pitch while you speak is the greatest approach to maintain a welcoming tone and since you are tired, you better wait and not make calls because it may tell in your voice.
Learn more about friendly tone from
https://brainly.com/question/25627023
#SPJ1
See full question below
What can you do to make sure your voice projects a friendly tone?
Leave a short, curt voice mail message.
Smile when speaking on the phone.
Avoid talking on the phone.
a data analyst writes the following code chunk to return a statistical summary of their dataset: quartet %>% group by(set) %>% summarize(mean(x), sd(x), mean(y), sd(y), cor(x, y)) which function will return the average value of the y column?
Answers
The function that will return the average value of the y column is mean(x,y). The correct option is 4.
What is a dataset?A dataset is a structured collection of data that is usually associated with a single piece of work. A database is a structured collection of data that is stored in multiple datasets.
Data sets can store information such as medical records or insurance records for use by a system program.
Data sets are also used to store information that is required by applications or the operating system, such as source code, macro libraries, or system variables or parameters.
mean is the function that returns the average value of the y column (x,y).
Thus, the correct option is 4.
For more details regarding dataset, visit:
https://brainly.com/question/26468794
#SPJ1
Your question seems incomplete, the missing options are:
1. sd(x)
2. cor(x,y)
3. sd(y)
4. mean(y)
Which type of selector is specified by placing a # symbol in front of the selector name?
Question options:
tag
first
class
id
Answers
The type of selector that is specified by placing a # symbol in front of the selector name is an ID selector.
In CSS (Cascading Style Sheets), an ID selector is used to select and style a specific element on a web page based on its unique ID attribute. To create an ID selector, you start with the "#" symbol, followed by the ID name. For example, if you have an element with an ID of "my-element", you can create a CSS rule to style it using the following code:
#my-element {
color: red;
font-size: 16px;
}
This code applies the styles specified within the curly braces to the element with the ID of "my-element".
In summary, an ID selector is a CSS selector that selects and styles a specific element on a web page based on its unique ID attribute. It is specified by placing a "#" symbol in front of the ID name.
Learn more about symbol here:
https://brainly.com/question/9718834
#SPJ11