a third-party vendor created an unmanaged lightning web component. the salesforce administrator wishes to expose the component only on record page layouts. which two actions should the developer take to accomplish this business objective? choose 2 answers specify lightningcommunity page as a target in the xml file. ensure isexposed is set to true on the xml file. specify lightningcommunity page layout as a target in the xml file. specify lightning recordpage as a target in the xml file. see all questions back next question
Answers
The developer should take these two actions to accomplish this business objective:
Ensure isExposed is set to true on the XML file.
Specify lightning_RecordPage as a target in the XML file.
What is XML file?A file that ends in ".xml" is an XML file and contains XML code. It has tags that specify how the document should be stored and transported over the internet, in addition to how it should be structured.
XML files are plain text documents, making them simple for both computers and people to create, store, transport, and understand. Because of this, XML is among the most widely used languages on the internet. Many web-based software programmes use XML as their primary data storage and communication format.
Text and tags in both XML and HTML contain instructions for the software on how to use them. HTML tags, however, define how data is displayed, whereas XML tags define the type of data.
Learn more about XML
https://brainly.com/question/11605816
#SPJ4
Related Questions
Martin is responsible for translating the script into a visual form by creating a storyboard. Which role is he playing?
Martin is playing the role of a(n)
Answers
Answer:
The correct answer to this question is given below in the explanation section.
Explanation:
The question is about to identify the role of Martin, who converts script into visual form by creating a storyboard.
The correct answer to this question is:
Martin is playing the role of Production Design and he is working at the position of the production designer.
Before shooting a film, the production designer is the first artist who converts script into a visual form such as creating storyboards. And, that storyboard serves as the first film draft.
A storyboard is a series of sketches, paintings, etc arranged on a panel to show the visual progress of the story from one scene to the next. These storyboards are used from start to finish of the film. Because these storyboards or sketches serve as the visual guide for the director of the film throughout the production.
Answer:
Hi
Explanation:
THE ANSWER UP TOP IS WRONG LIKE DEAD WRONG
Hey tell me more about your service
Answers
Answer:
look below!
Explanation:
please add more context and I’ll be happy to answer!
1. What is virtual memory?
The use of non-volatile storage, such as disk to store processes or data from physical memory
A part of physical memory that's used for virtualisation
Some part of physical memory that a process though it had been allocated in the past
O Future physical memory that a process could be allocated
Answers
Answer:
The use of non-volatile storage, such as disk to store processes or data from physical memory.
Explanation:
Virtual memory is used by operating systems in order to allow the execution of processes that are larger than the available physical memory by using disk space as an extension of the physical memory. Note that virtual memory is far slower than physical memory.
Drag each tile to the correct box.
Match the certifications to the job they best fit.
CompTIA A+
Cisco Certified Internetwork Expert (CCIE)
Microsoft Certified Solutions Developer (MCSD)
help desk technician
network design architect
software developer
Answers
Answer:
software developer- microsoft certified solutions developer
help desk technician- CompTIAA+
network design architect- Cisco certified internetwork expert
Explanation
edmentum
Select the correct answer. Which number system consists of digits 0 to 9 and letters A to F? octal binary hexadecimal decimal
Answers
Answer:
hexadecimal
represents a radix of 16
3. Think of a 2D game you enjoyed recently. Did it use vector graphics or bitmap graphics? How do you think the developers made their decision between which style to use—beyond the consideration of scalability?
4. One way to analyze software is to look at its functionality (whether the features work and give you the expected outcome) and its usability (whether it is easy to understand and use). Analyze one (or more) of the software programs discussed in the unit (i.e., GIMP) according to its functionality and usability.
5. The unit described how the game Assassin’s Creed uses rich landscapes based on real-world locations like Rome in Renaissance Italy or Jerusalem during the Crusades. While the benefits include creating a highly immersive game experience, what are some of the potential drawbacks to creating game environments based on the real-world
Answers
It used vector graphics, and the making was excellent.
Need help
I need help with this it’s really confusing and I have to send it to my teacher with a file I don’t get it

Answers
Answer:
100 POINTS MATHEMATICS MIDDLE SCHOOL HOMEWORK.
I will report you if you answer incorrectly or steal my points.
When should you use an array in developing a program? Explain why it is important to apply arrays in a program.
Answers
Answer:
The answer is below
Explanation:
There are various reasons to apply arrays in a program. Some of which includes:
1. Arrays provides users to easily save specified numbers of the element in them.
2. It easily store data of similar types and sizes.
3. It allows users to store data in various dimensional arrays.
4. It eliminates deficit of memories for the location of its elements
What is one way to calm your feelings before taking
a test?
Answers
Answer:
For me I chew gum if avaliable and if it's not I think of something funny
Explanation:
Order the steps to successfully create a data table.
Answer: Write the formula used to create table values
Select the range
Select the Data tab and What-If Analysis
Select Data Table
Select the values for row/column input.
Answers
Here are the steps to successfully create a data table:
Select the range.Select the Data tab and What-If Analysis.Select Data Table.Write the formula used to create table values.Select the values for row/column input.How to create the data tableFor achieving the desired outcome of generating a data table, it is suggested to adhere to the following measures:
Choose the cells group in which you intend to generate the data table. Include both the cells for input and presentation of results in the specified range.
Provide the equation that you intend to apply for computing the figures enlisted in the data chart. This equation must refer to the designated cells and yield the intended outcome.
Access the What-If Analysis feature by navigating to the Data tab within your spreadsheet program. To access the menu, simply click on it.
Choose the Data Table option from the What-If Analysis menu. This action will trigger the appearance of a dialog box or prompt that will require you to input the required details.
Determine the desired input values for either the row or the column in the data table dialogue box. The table's outcomes will be computed based on these values.
By adhering to these guidelines, you can produce a chart of data that exhibits computed figures derived from various input situations, aiding you in scrutinizing and comprehending the ramifications of different factors on your data.
Read more about data tables here:
https://brainly.com/question/32534586
#SPJ1
you are in the process of inducting new employees on the Global AssetView application. In your presentation you have to add the features of the application, which features from the list below will you include?
Answers
1. Data Visualization: This feature allows users to view asset data in a variety of ways, such as charts, graphs, and tables. This helps users quickly get an overview of their asset portfolio and identify patterns in their asset data.
What is portfolio?A portfolio is a collection of an individual's or organization's work, such as financial assets, investments, and other evidence of accomplishments. It is usually presented as a showcase of skills, accomplishments, and experiences to help an individual or organization stand out in the competitive job market.
2. Asset Tracking: This feature allows users to keep track of the location and status of assets, both in the physical and digital realms. It provides users with a comprehensive view of their asset portfolio and helps them identify any potential problems.
3. Automated Reporting: This feature allows users to generate reports in a variety of formats, such as PDFs and spreadsheets. Automated reporting helps users track asset performance and automate the process of reporting to stakeholders.
4. Risk Management: This feature helps users identify and manage potential risks associated with their assets. It provides users with a comprehensive overview of their asset portfolio and helps them develop strategies to reduce or mitigate risk.
5. Security: This feature provides users with a secure environment to store and manage their asset data. It helps users protect their asset data from unauthorized access and ensure their data is safe and secure.
To learn more about portfolio
https://brainly.com/question/25929259
#SPJ1
How is LUA different from Python?
Give an example.
Answers
This is the answer I couldn't write it here since brainly said it contained some bad word whatever.
Answer:
good old brainly think stuff is bad word even tho it is not had to use txt file since brainly think code or rblx is bad word
A Quicksort (or Partition Exchange Sort) divides the data into 2 partitions separated by a pivot. The first partition contains all the items which are smaller than the pivot. The remaining items are in the other partition. You will write four versions of Quicksort:
• Select the first item of the partition as the pivot. Treat partitions of size one and two as stopping cases.
• Same pivot selection. For a partition of size 100 or less, use an insertion sort to finish.
• Same pivot selection. For a partition of size 50 or less, use an insertion sort to finish.
• Select the median-of-three as the pivot. Treat partitions of size one and two as stopping cases.
As time permits consider examining additional, alternate methods of selecting the pivot for Quicksort.
Merge Sort is a useful sort to know if you are doing External Sorting. The need for this will increase as data sizes increase. The traditional Merge Sort requires double space. To eliminate this issue, you are to implement Natural Merge using a linked implementation. In your analysis be sure to compare to the effect of using a straight Merge Sort instead.
Create input files of four sizes: 50, 1000, 2000, 5000 and 10000 integers. For each size file make 3 versions. On the first use a randomly ordered data set. On the second use the integers in reverse order. On the third use the
integers in normal ascending order. (You may use a random number generator to create the randomly ordered file, but it is important to limit the duplicates to <1%. Alternatively, you may write a shuffle function to randomize one of your ordered files.) This means you have an input set of 15 files plus whatever you deem necessary and reasonable. Files are available in the Blackboard shell, if you want to copy them. Your data should be formatted so that each number is on a separate line with no leading blanks. There should be no blank lines in the file. Even though you are limiting the occurrence of duplicates, your sorts must be able to handle duplicate data.
Each sort must be run against all the input files. With five sorts and 15 input sets, you will have 75 required runs.
The size 50 files are for the purpose of showing the sorting is correct. Your code needs to print out the comparisons and exchanges (see below) and the sorted values. You must submit the input and output files for all orders of size 50, for all sorts. There should be 15 output files here.
The larger sizes of input are used to demonstrate the asymptotic cost. To demonstrate the asymptotic cost you will need to count comparisons and exchanges for each sort. For these files at the end of each run you need to print the number of comparisons and the number of exchanges but not the sorted data. It is to your advantage to add larger files or additional random files to the input - perhaps with 15-20% duplicates. You may find it interesting to time the runs, but this should be in addition to counting comparisons and exchanges.
Turn in an analysis comparing the two sorts and their performance. Be sure to comment on the relative numbers of exchanges and comparison in the various runs, the effect of the order of the data, the effect of different size files, the effect of different partition sizes and pivot selection methods for Quicksort, and the effect of using a Natural Merge Sort. Which factor has the most effect on the efficiency? Be sure to consider both time and space efficiency. Be sure to justify your data structures. Your analysis must include a table of the comparisons and exchanges observed and a graph of the asymptotic costs that you observed compared to the theoretical cost. Be sure to justify your choice of iteration versus recursion. Consider how your code would have differed if you had made the other choice.
Answers
The necessary conditions and procedures needed to accomplish this assignment is given below. Quicksort is an algorithm used to sort data in a fast and efficient manner.
What is the Quicksort?Some rules to follow in the above work are:
A)Choose the initial element of the partition as the pivot.
b) Utilize the same method to select the pivot, but switch to insertion sort as the concluding step for partitions that contain 100 or fewer elements.
Lastly, Utilize the same method of pivot selection, but choose insertion sort for partitions that are of a size equal to or lesser than 50 in order to accomplish the task.
Learn more about Quicksort from
https://brainly.com/question/29981648
#SPJ1
Recall your technology experience in the workplace or at home. When adopting a new technology, what specific problems were you or your employer trying to resolve?
Describe your biggest challenge in adopting new technologies based on your experience.
Share how you or your employer overcame these issues.
Answers
Answer:
Use of technology helps solve issues like file management, receipt tracking, report generation and growth tracking that often hamper employee productivity. Modern workplaces extensively rely on computer-aided tools for efficiency. These tools help cut down both the time and money needed for getting the job done.
How do you implement new technology in the workplace?
To help you streamline the process, here are steps for integrating new technology into your organization:
Identify Your Organization's Needs.
Investigate Technologies That Will Solve Problems for Your Organization.
Develop a Plan for Implementing Your New Technology.
Train Other Employees in Using the New Technology
To edit the color of the text in Word Online, choose the Font color command under what tab?
Home
Design
Page Layout
View
Answers
Answer:
Home Tab
Explanation:
Font group --- choose the arrow next to Font Color, ---- then select a color.
What is the main reason for assigning roles to members of a group?
It speeds up the time it takes to do a task.
It provides a way for the group to meet on a regular basis.
It allows one person acting in the role of the facilitator to take charge and do all the work.
It creates leadership and direction for the team, making it easier to work together for a common purpose.
Answers
Answer: it creates leadership and direction for the team, making it easier to work together for a common purpose.
Explanation:
The reason for assigning roles to members of a group is that it creates leadership and direction for the team, making it easier to work together for a common purpose.
When roles are delegated to the members of a group, each person gets his or her own part of the job or project. This makes it easier to work together and as a team. It also ensures that the project is handled well and faster as it creates a direction.
Answer:
D. It creates leadership and direction for the team, making it easier to work together for a common purpose.
Explanation:
What are the connections between the following concepts: letter frequency, avalanche effect, correlation between plaintext and ciphertext , and diffusion?
Answers
The Avalanche Effect describes how modifications to the plaintext have an impact on the ciphertext for a good cypher. When the input is only slightly altered, the algorithm generates an entirely different outcome.
Avalanche breakdown definition How does the avalanche breakdown mechanism look like in a diagram?Avalanche Breakdown: When a significant reverse voltage is put across the diode, the avalanche breakdown happens. The electric field across the junction grows when the applied reverse voltage is increased. The electrons at the junction are forced by the electric field, breaking their covalent bonds.
Which four fundamental security tenets apply to messages?Confidentiality, Integrity, Non-repudiation, and Authentication are the four primary security principles that apply to messages.
To know more about Avalanche Effect visit:-
brainly.com/question/29095928
#SPJ1
Computers are because they can perform many operations on their own with the few commands given to them
Answers
Computers are programmable because they can perform a wide range of operations on their own with just a few commands given to them. They are designed to carry out different functions through the execution of programs or software, which comprises a sequence of instructions that a computer can perform.
The instructions are expressed in programming languages, and they control the computer's behavior by manipulating its various components like the processor, memory, and input/output devices. Through these instructions, the computer can perform basic operations like arithmetic and logic calculations, data storage and retrieval, and data transfer between different devices.
Additionally, computers can also run complex applications that require multiple operations to be performed simultaneously, such as video editing, gaming, and data analysis. Computers can carry out their functions without any human intervention once the instructions are entered into the system.
This makes them highly efficient and reliable tools that can perform a wide range of tasks quickly and accurately. They have become an essential part of modern life, and their use has revolutionized various industries like healthcare, education, finance, and entertainment.
For more questions on Computers, click on:
https://brainly.com/question/24540334
#SPJ8
The data structure used for file directory is called
Select one
a. process table
b. mount table
C. hash table
d file table
Answers
Data structures used for file directories typically have a hierarchical tree structure, referred to as a directory structure. The tree has a root directory, and every file in that system has a unique path.
The simplest method of implementing a directory is to use a linear list of file names with pointers to the data blocks. But another way that you can format a file directory is by using a hash table. With this method, the linear list stores the directory entries, but a hash data structure is also used. The hash table takes a value computed from the file name and return the pointer to the file name any linear list.
So I think it’s C. But I’m not 100% sure.
I hope that helps.
I am doing a customer service manual and need a toc. I can't get the numbers lined up. Can someone please help me? I am using Microsoft word

Answers
Below is a Table of Contents (TOC) for your customer service manual with aligned numbers using Microsoft Word:
Welcome StatementGetting StartedWays to Discern Customers' Needs and ConcernsTelephone Communication4.1 Transferring a Customer's Call4.2 Sending an EmailSelf-Care After the JobHow to Manage Your Time WiselyFundamental Duties of a Customer Service WorkerEnhancing Customer Impressions and SatisfactionDifference Between Verbal and Nonverbal CommunicationKey TraitsBest Speaking SpeedKnowing the Different Problems and How to Manage Them12.1 Extraordinary Customer Problems12.2 Fixing Extraordinary Customer ProblemsKnowing Customer Diversity13.1 Tactics for Serving Diverse and Multicultural CustomersKnowing How to Handle Challenging CustomersWhat is the customer service manual?Below is how you can create a Table of Contents (TOC) with aligned numbers in Microsoft Word:
Step 1: Place your cursor at the beginning of the document where you want to insert the Table of Contents.
Step 2: Go to the "References" tab in the Microsoft Word ribbon at the top of the window.
Step 3: Click on the "Table of Contents" button, which is located in the "Table of Contents" group. This will open a drop-down menu with different options for TOC styles.
Step 4: Choose the TOC style that best fits your needs. If you want aligned numbers, select a style that includes the word "Classic" in its name, such as "Classic," "Classic Word," or "Classic Format." These styles come with aligned numbers by default.
Step 5: Click on the TOC style to insert it into your document. The TOC will be automatically generated based on the headings in your document, with numbers aligned on the right side of the page.
Step 6: If you want to update the TOC later, simply right-click on the TOC and choose "Update Field" from the context menu. This will refresh the TOC to reflect any changes you made to your headings.
Note: If you're using a different version of Microsoft Word or a different word processing software, the steps and options may vary slightly. However, the general process should be similar in most word processing software that supports the creation of TOCs.
Read more about customer service here:
https://brainly.com/question/1286522
#SPJ1
See text below
I am doing a customer service manual and need a toc. I can't get the numbers lined up. Can someone please help me? I am using Microsoft word
Welcome Statement
Getting Started
Ways to discern customers' needs and concerns
Telephone communication....
Transferring a customer's call
Sending an email
Self-Care after the job
How to manage your time wisely
Fundamental duties of a Customer Service Worker
Enhancing Customer Impressions and Satisfaction
N
5
.5
6
Difference between Verbal and Nonverbal Communication
.6
Key Traits.....
.7
Best speaking speed
7
Knowing the different problems and how to manage them
Extraordinary Customer Problems
Fixing Extraordinary Customer Problems
Knowing Customer Diversity
Tactics for serving diverse and Multicultural customers
Knowing how to handle challenging customers.
Sure! Here's a Table of Contents (TOC) for your cu
How is QA done in agile projects
Answers
200+300-500.
Explanation:
rjfnvkfjfhfofgfohgighghgiggh
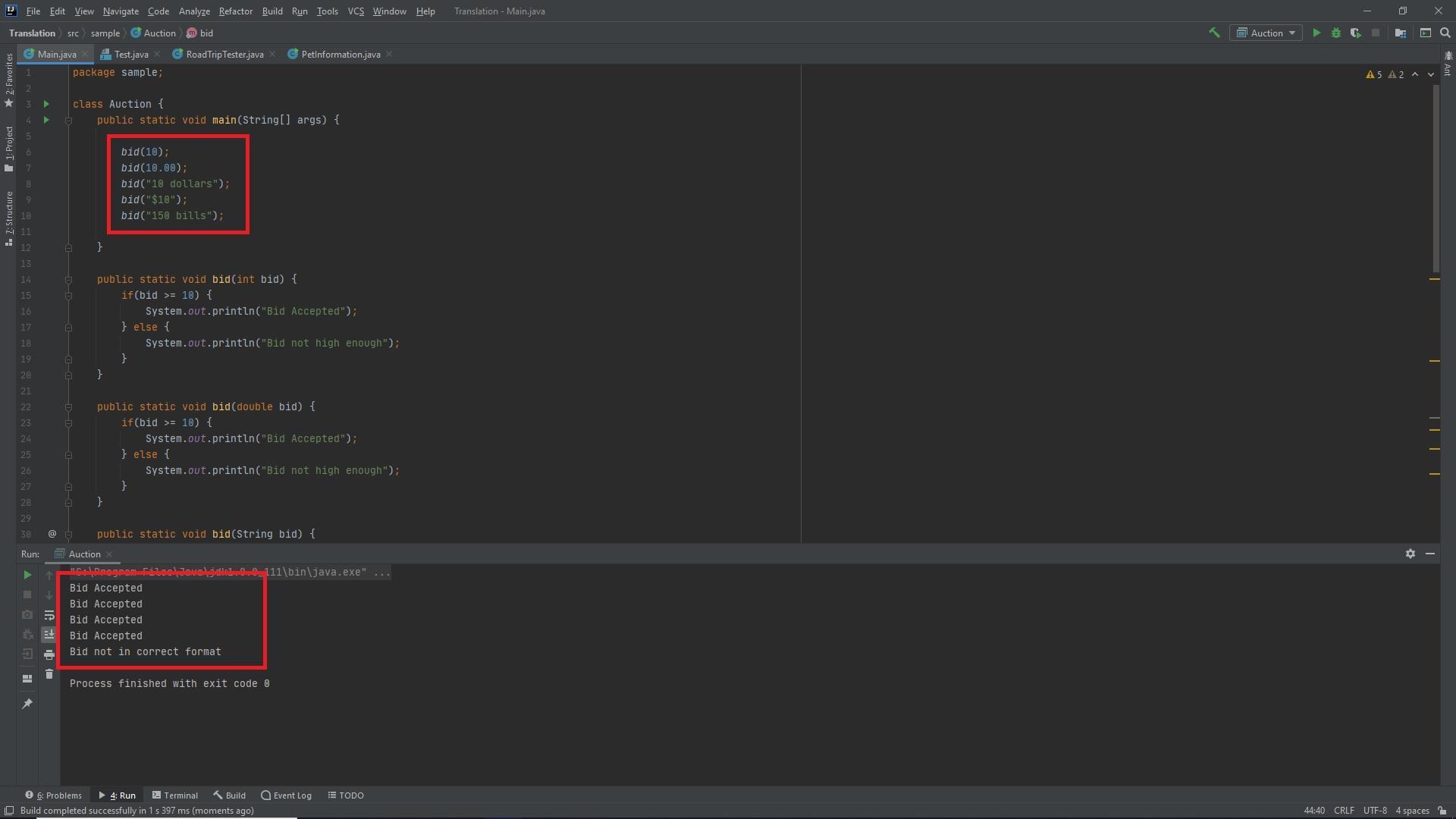
Create a program named Auction that allows a user to enter an amount bid on an online auction item. Include three overloaded methods that accept an int, double, or string bid. Each method should display the bid and indicate whether it is over the minimum acceptable bid of $10. If the bid is greater than or equal to $10, display Bid accepted. If the bid is less than $10, display Bid not high enough. If the bid is a string, accept it only if one of the following is true: It is numeric and preceded with a dollar sign. It is numeric and followed by the word dollars. Otherwise, display a message that says Bid was not in correct format. Grading When you have completed your program, click the Submit button to record your score.
Answers
Answer:
Explanation:
The following code is written in Java and creates the overloaded methods as requested. It has been tested and is working without bugs. The test cases are shown in the first red square within the main method and the output results are shown in the bottom red square...
class Auction {
public static void main(String[] args) {
bid(10);
bid(10.00);
bid("10 dollars");
bid("$10");
bid("150 bills");
}
public static void bid(int bid) {
if(bid >= 10) {
System.out.println("Bid Accepted");
} else {
System.out.println("Bid not high enough");
}
}
public static void bid(double bid) {
if(bid >= 10) {
System.out.println("Bid Accepted");
} else {
System.out.println("Bid not high enough");
}
}
public static void bid(String bid) {
if (bid.charAt(0) == '$') {
if (Integer.parseInt(bid.substring(1, bid.length())) > 0) {
System.out.println("Bid Accepted");
return;
} else {
System.out.println("Bid not in correct Format");
return;
}
}
int dollarStartingPoint = 0;
for (int x = 0; x < bid.length(); x++) {
if (bid.charAt(x) == 'd') {
if (bid.substring(x, x + 7).equals("dollars")) {
dollarStartingPoint = x;
} else {
break;
}
}
}
if (dollarStartingPoint > 1) {
if (Integer.parseInt(bid.substring(0, dollarStartingPoint-1)) > 0) {
System.out.println("Bid Accepted");
return;
} else {
System.out.println("Bid not in correct format");
return;
}
} else {
System.out.println("Bid not in correct format");
return;
}
}
}
Alice's public key, and sends back the number R encrypted with his private key. Alice decrypts the message and verifies that the decrypted number is R. Are the identities of Alice and Bob verified in this protocol?
Answers
There are different kinds of keys. The identities of Alice and Bob are verified in this protocol.
What is public and private key in SSL?These keys are known to be a kind of related pair of text files and they are often made together as a pair if one makes their Certificate Signing Request (CSR).
Note that the private key is different file that is often used in the encryption/decryption of data so as to sent a file between one's server and the connecting clients.
Learn more about public/private key from
https://brainly.com/question/8782374
I need help solving this, please. (Do not know if this is allowed but I definitely need help.)
You work as an IT manager for Bower Industries, a Web hosting company that provides off-site Web hosting for online businesses. Your current service level agreement promises customers 24/7 server availability; however, in the unlikely event of a server outage, you need to gauge the economic impact.
Based on your current user base, you estimate a cost of $1,500 an hour in customer refunds if an outage were to occur.
Your assistant has attempted to create a one-variable data table to estimate further the economic impact of outages between one and five hours in length.
Unfortunately, the one-variable data table is not returning the correct results due to an error in the input values.
You will correct the error and add existing range names to the Total Cost for Outage formula.
Finally, you will create a custom number format for cell E3.
Open e06d1NetworkOutage and save it as e06d1NetworkOutage_LastFirst.
Delete the inaccurate values in the range E4:E12.
Apply the pre-existing range names to the worksheet.
Enter a reference to the Total Cost for Outage (cell B6) in cell E3.
Create a one-variable data table to detail the sensitivity of expense based on an outage range of one to five hours based on half-hour increments.
Add a Custom number format to cell E3 to display the word Cost.
Create a footer with your name, the sheet name code, and the file name code.
Save and close the file. Submit e06d1NetworkOutage_LastFirst.

Answers
Answer:
hi sorry, this is excel right?
Explanation:
Give me two reasons why return statements are used in code.
Answers
And it can give a certain value to send back so it can be used elsewhere in your code
Explanation:
The C language return statement ends function execution and ... the calling function at the point immediately following the call. ... For more information, see Return type.
2.) Using Constants and Variables to create a Program (10 points)
You are going to write out a program below that will help calculate the total amount of money made per
week, based on a 5 day work week and making $8 per hour.
You will need to create (2) Constant variables
You will need to create (3) variables
Answers
Using Constants and Variables to create a Program is given below.
How to create the program# Establish constant values
DAYS_PER_WEEK = 5
HOURLY_WAGE = 8
# Introduce changeable parameters
hours_worked = 0
daily_earnings = 0
total_earnings = 0
# Ask user regarding hours labored each day
for day in range(1, DAYS_PER_WEEK + 1):
hours_worked = int(input(f"How many hours did you work on day {day}? "))
daily_earnings = hours_worked * HOURLY_WAGE
total_earnings += daily_earnings
# Display aggregate income for the week
print(f"You made a total of ${total_earnings} this week.")
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Write a function (getResults) that returns the Fahrenheit equivalents of Celsius temperatures. The function will have the Celsius as the parameter.
The formula for converting a temperature from Celsius to Fahrenheit is
F = 9C + 32
5
F
where F is the Fahrenheit temperature, and C is the Celsius temperature.
Your function returns the Fahrenheit equivalent. (Python)

Answers
Here's a Python function that converts a temperature from Celsius to Fahrenheit using the formula F = 9/5 * C + 32:
The Python Codedef getResults(celsius):
fahrenheit = (9/5 * celsius) + 32
return fahrenheit
You can call this function with a Celsius temperature to get the Fahrenheit equivalent:
>>> getResults(0)
32.0
>>> getResults(100)
212.0
>>> getResults(-40)
-40.0
Note that the function assumes that the input temperature is in Celsius. If you pass in a temperature in Fahrenheit, the result will be incorrect.
Read more about python programming here:
https://brainly.com/question/26497128
#SPJ1
What are some ways technology has changed the way people live
Answers
Answer:
Multiple ways.
Explanation:
Here are some examples. Modern people relay on technology alot! It shapes our lives. Like now you can order something without moving from you place using your smartphone. When you need a spare part for a lego for example you can now just 3D print it without buying another one. See plenty of ways. Looks around you and find more examples.
create a randomly generated password (must include uppercase, lowercase and numbers) and write it to a text file
Answers
Using Random password generator, You can create a randomly generated password including uppercase, lowercase and numbers, For example 6druBh28P$Q. And to write it into a text file, just paste this in notepad and save as .txt and you're done.
What is a password?In practically all digital and computing appliances, a password is one of the most popular access control methods. The majority of the time, a person must enter both in order to access a system, network, or other password-protected area.
Passwords are typically used in conjunction with user names. The majority of programmes and services require users to create their own passwords, which are typically unique for each system or service they use.
A password should have at least one uppercase, one number, and one special character, and should be eight to 24 characters long in accordance with good security practises. The use of words is common, but it is not advisable because they can be predicted or cracked more easily.
Learn more about password
https://brainly.com/question/15569196
#SPJ4
a stop watch is used when an athlete runs why
Answers
Explanation:
A stopwatch is used when an athlete runs to measure the time it takes for them to complete a race or a specific distance. It allows for accurate timing and provides information on the athlete's performance. The stopwatch helps in evaluating the athlete's speed, progress, and overall improvement. It is a crucial tool for coaches, trainers, and athletes themselves to track their timing, set goals, and analyze their performance. Additionally, the recorded times can be compared to previous records or used for competitive purposes,such as determining winners in races or setting new records.
you can support by rating brainly it's very much appreciated ✅