when non-numeric data is being added to a table, the data must be enclosed in ____________________ quotation marks.
Answers
When non-numeric data is added to a table, the data must be enclosed in single or double quotation marks, depending on the programming language or database management system you are using. Enclosing non-numeric data in quotation marks ensures that the system correctly identifies and processes the data as a string, rather than a numeric value or a variable.
Quotation marks help differentiate between various data types in programming languages and databases. Numeric data, such as integers and floating-point numbers, can be input without any special characters. However, non-numeric data like text or characters requires the use of quotation marks to prevent errors and maintain proper data handling.
In most programming languages and database systems, single and double quotation marks are interchangeable, but it's essential to use them consistently throughout your code or query. Some systems, like SQL, may require single quotation marks specifically for enclosing non-numeric data.
It's crucial to follow the proper syntax when working with data types, as incorrect usage of quotation marks can lead to errors or incorrect data processing. Enclosing non-numeric data in quotation marks allows for proper identification and manipulation of the data, ensuring accurate and efficient operations in your programs and databases.
You can learn more about non-numeric data at: brainly.com/question/4860917
#SPJ11
Related Questions
on a network, file sharing allows users to open, view, edit, copy, and delete files from a remote device, provided that they have the proper .
Answers
On a network, file sharing allows users to perform various actions on files stored on a remote device. These actions include opening, viewing, editing, copying, and deleting files.
However, users can only perform these actions if they have the proper authorization or permissions.
Authorization or permissions determine the level of access a user has to the shared files. For example, a user may have read-only access, which means they can only open and view the files but cannot make any changes. On the other hand, a user with full access can perform all the actions mentioned above.
To gain the proper authorization, users usually need to provide valid credentials, such as a username and password. These credentials verify their identity and determine the level of access they are granted.
In summary, file sharing on a network allows users to interact with files on a remote device, but their actions are limited by the permissions assigned to them. Valid credentials are required to gain the necessary authorization.
To know more about network visit:
https://brainly.com/question/33577924
#SPJ11
you are configuring a new system, and you want to use a raid 0 array for the operating system using sata disks and a special controller card that includes a raid processor. which raid method should you use?
Answers
Performance improvements are the key benefit of disk striping and RAID 0. For instance, three hard drives would offer three times the bandwidth of a single drive if data were striped over them.
Disk striping would enable up to 600 IOPS for data reads and writes if each drive operated at a rate of 200 input/output operations per second (IOPS). Disk striping is similarly used in RAID 5, however this version offers fault tolerance for a single disk failure. Disk striping divides data into smaller units and saves the units across a number of drives by simultaneously reading from and writing to each disk. Disk striping is used in RAID 0 but there is no fault tolerance. Hard disk drive (HDD) minimums and maximums for RAID 5 groups are both three.
Learn more about disk striping here-
https://brainly.com/question/14018617
#SPJ4
The __________ sends information from a network to the internet.
Answers
Answer:
brainlest please
Answer:
Intranet
Explanation:
According to my research on information technology and hardware, I can say that based on the information provided within the question the term being described is called an Intranet. This (like mentioned in the question) is a local or restricted communications network,usually made as a private network within an organization and is created using Internet Protocol Technology.
I hope this answered your question. If you have any more questions feel free to ask away at Brainly.
Explanation:
Answer:
The 'router' sends info from a network to the internet
Explanation:
A router is a physical or virtual device that sends information contained in data packets between networks.
name any two web browsers?
Answers
Explanation:
Chrome
Opera
That's all i can get for u
Answer:
Microsoft Edge and Internet Explorer
Explanation:
the technology used for any cellular communication that is portable. Criline wirwer| Carncethtive eraiketirg intelligence Causal research Matile technoloby Question 8 is repetitive interaction between a custemer and a specific brand. Cintomer lavalty Ontomer ergagemicot Customer rewards maragement Ethical maketine Question 9 Is the communication between the company and the customer that causes a reaction an inter Custamer engagement Ountomet tewartis manasement Customer value Cistomet lovalty Question 10 customers that have needs that can be met by the company and is a viable market to serve. Cavsal sesearch Target market Prace Ethical marketing:
Answers
Customer loyalty, customer engagement, and target market are all important concepts in marketing and business.
Question 8: Customer loyalty
Question 9: Customer engagement
Question 10: Target market
Question 8 refers to the repetitive interaction between a customer and a specific brand, which is known as customer loyalty. It indicates that the customer consistently chooses and supports a particular brand.
Question 9 involves the communication between the company and the customer that elicits a reaction or response from the customer. This is referred to as customer engagement, where the customer actively interacts with the company.
Question 10 pertains to customers who have specific needs that can be fulfilled by the company and represent a viable market segment to serve. This is known as the target market, which the company aims to target and cater to with its products or services.
In conclusion, customer loyalty, customer engagement, and target market are all important concepts in marketing and business. Understanding and effectively managing these aspects can contribute to the success and growth of a company.
To know more about marketing and business visit
https://brainly.com/question/25369230
#SPJ11
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
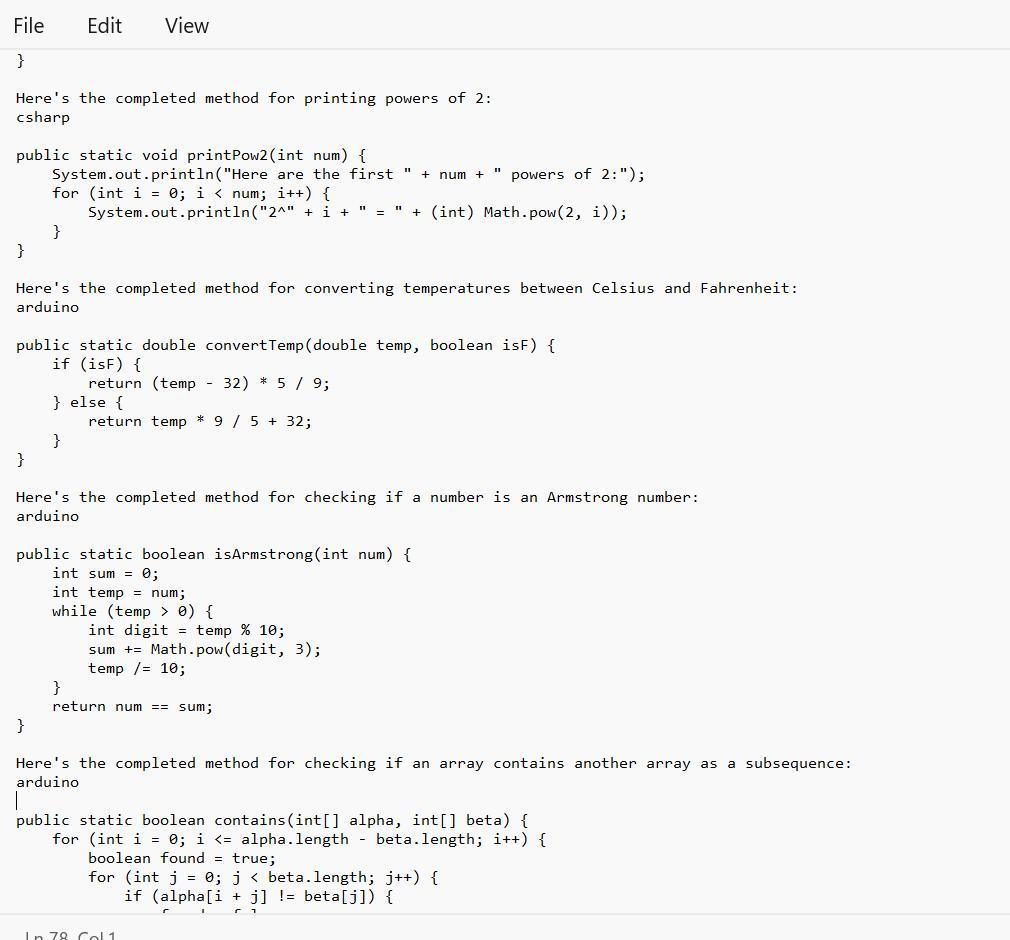
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


what was tari's total standard machine-hours allowed for last year's output?
Answers
Tari's total standard machine-hours allowed for last year's output was not provided in the question. Therefore, I cannot give a specific number for the total standard machine-hours allowed. Standard machine-hours allowed refers to the number of hours allocated for a specific task or production process based on predetermined standards.
It takes into account factors such as machine capacity, labor requirements, and materials used. Without knowing the specifics of Tari's production process and standards, it is impossible to determine the exact number of standard machine-hours allowed for last year's output. To determine the total standard machine-hours allowed for last year's output, we would need to know the following information.
Tari's production process: What is the process for creating the output? This will help determine how many machine-hours are required to complete the task. Machine capacity: How many machines are available and what is their capacity? This will help determine the number of hours that can be allocated to each machine. Labor requirements: How many workers are needed to operate the machines and perform other tasks? This will help determine how many hours of labor are required. Materials used: What materials are used in the production process? This will help determine the amount of time required to process and handle the materials. Once we have this information, we can calculate the total standard machine-hours allowed for last year's output. However, since this information was not provided in the question, we cannot give a specific answer. To answer your question regarding Tari's total standard machine-hours allowed for last year's output, I will need some more information. Specifically, the standard machine-hours per unit and the total number of units produced last year. Once you provide that information, I can help you calculate the total standard machine-hours allowed.
To know more about allowed visit:
https://brainly.com/question/27281756
#SPJ11
What is the final value of x (after this code has executed)?
int x = 0;
for (x = 0; x < 200; x++)
{
System.out.println(x);
}
Answers
Answer:
199
Explanation:
i starts at 0. One more than 0 is one. Until you get 199.
The computer is counting as seen below:
0
1
2
....
199
what added functionality does a router have that an access point does not?
Answers
A local area network is created by the router, which also controls all of the connected devices and communication. On the other hand, an access point is a sub-device of the local area network that enables more devices to be connected to the network and offers another location for devices to connect from.
A router is a device that connects several networked devices and controls traffic flow between them. It offers a number of features that an access point does not, such as:
1) Network Address Translation (NAT): NAT is a function of routers that enables a group of devices to share a single public IP address. This implies that a single connection can be used by all the devices connected to your network to access the internet.
2) DHCP Server: The Dynamic Host Configuration Protocol (DHCP) server found in routers provides IP addresses to networked devices automatically.
3) Firewall: Routers have an internal firewall that guards against illegal traffic and access to the network.
4) VLAN Support: Virtual LANs (VLANs), which let you build distinct networks on the same physical network, are supported by routers.
5) Quality of Service (QoS): QoS capabilities on routers let you prioritize network traffic depending on an application, device, or user.
On the other hand, access points are gadgets that offer wireless connectivity to a network. They lack built-in firewalls and QoS features, as well as routing functions like NAT and DHCP. Their primary duty is to give network devices wireless connectivity.
To know more about router
brainly.com/question/30074048
#SPJ4
The .quad instruction reserves ____ bits of memory in the data segment
Answers
The .quad instruction in assembly language is used to reserve 64 bits memory in the data segment of the program.
The amount of memory that is reserved is dependent on the operand that is used with the .quad instruction. In general, the .quad instruction reserves 64 bits, or 8 bytes, of memory in the data segment. This can be useful for declaring variables that require a larger amount of memory than a single byte or word, such as long integers or double-precision floating point numbers. The .quad instruction is similar to other memory allocation instructions in assembly language, such as .byte and .word, which allocate 8 and 16 bits of memory, respectively. By using these instructions, programmers can ensure that their program has the necessary amount of memory to store data and execute code.To know more about memory visit:
https://brainly.com/question/30499660
#SPJ4
Which part of the Word application window should the user go to for the following activities?
Read a document: ?
Find the name of the document: ?
Change the way a document is viewed: ?
Find help to do a certain activity on Word: ?
Go up and down to different parts of a document: ?
Determine the page number of the document: ?
Answers
Answer:
1) To read a document, in word open a document, the information contained in the document will be displayed in the document window in the document template area
2) To find the name of the document; The name of an opened word document is displayed as the document title, in the title bar
3) To change the way a document is viewed; The way a document is viewed in word can be changed from the "View" menu in the top ribbon of the opened document. The different views available includes, immersive, print layout, web layout, side to side, vertical and many more viewing options
4) To find help to do a certain activity in word can be done by either
i) Pressing the f1 key in word
ii) Selecting help icon at the top right hand corner of the file menu
iii) Typing the help request in the search dialog box at the top middle area of the screen
5) To go up and down to different parts of a document; The up, down, left and right arrow keys as well as the mouse and the page down and page up buttons can be used to navigate a document
6) The page number is displayed at the bottom left hand corner of the document
Explanation:
Answer:
Read a document: document area
Find the name of the document: title area
Change the way a document is viewed: ribbon area
Find help to do a certain activity on Word: ribbon area
Go up and down to different parts of a document: scroll bar
Determine the page number of the document: status bar
Explanation:
Which of the following functions returns the smallest number from a range of cells?
1 point
A. AVERAGE
B. MAX
C. MIN
D. SUM
Answers
Answer:
C. MIN
Explanation:
-
Which of the following is an example of academic integrity?
A. You work on each assignment mostly by yourself
B. You don't copy work or allow others to copy your work
c. You look up answers on the internet without citing the source
D. You work with close friends on assignments without instructor approval
Answers
Answer:
B. You don't copy work or allow others to copy your work
Explanation:
The example of academic integrity is that you don't copy work or allow others to copy your work. The correct option is B.
What is academic integrity?The moral code or ethical policy of academics is known as academic integrity. The R.C., regarded as the "grandfather of academic integrity," popularised the phrase.
Being honest, fair, polite, and responsible in your studies and academic work is referred to as having academic integrity.
It entails acting in accordance with these ideals both when producing your own work and engaging with that of others.
Academic integrity is the practise of doing learning, teaching, and research with the principles of honesty, trust, fairness, respect, and responsibility.
Students, teachers, researchers, and all other staff members should act honestly, take responsibility for their choices, and be fair in all aspects of their job.
Thus, the correct option is B.
For more details regarding academic integrity, visit:
https://brainly.com/question/9540934
#SPJ2
Describe what a Bank Run is.
Answers
Answer:
Explanation:
A bank run occurs when a large number of customers of a bank or other financial institution withdraw their deposits simultaneously over concerns of the bank's solvency. As more people withdraw their funds, the probability of default increases, prompting more people to withdraw their deposits.
Scrie un program care citind varstele a 2 copii afiseaza care dintre ei este cel mai mare si cu cat. Exemplu: Pentru varstele 5 si 9 se va afisa "al doilea copil e mai mare cu 4 ani"
Answers
Answer:
primul_copil = int(input("Introduceți vârsta primului copil: "))
aldoilea_copil = int(input("Introduceți vârsta celui de-al doilea copil: "))
def copilmai_mare(varsta1, varsta2):
if varsta1 > varsta2:
diferenta = varsta1 - varsta2
print("copilul mai mare este varsta1 cu diferența de vârstă de: ", diferenta )
else:
diferenta = varsta2 - varsta1
print("copilul mai mare este varsta2 cu diferența de vârstă de: ", diferenta )
copilmai_mare(primul_copil, aldoilea_copil)
Explanation:
Programul python de mai sus definește o funcție "copilmai_mare" care ia două argumente "varsta1" și "varsta2". Diferența dintre vârstele copiilor este comparată, iar cel mai mare copil și diferența sunt tipărite pe ecran.
What is bias? (Gradpoint)

Answers
Answer: The second option
Explanation:
Bias is a prejudice in favor of or against one thing, person, or group compared with another, usually in a way considered to be unfair.
Answer:
(second option) B. Bias refers to a leaning or partiality toward a particular viewpoint or perspective, which may affect the way information is presented, interpreted, or perceived. It can involve an inclination to favor one side over another, to present information in a certain light, or to downplay or ignore certain aspects.
Which command removes a selection from its original location so it can be moved to another location?
Cut
Copy
Undo
Redo
Answers
Answer:
Explanation:
Cut - Copy
b. 2 and 22
function,
13. To input a decimal you need the
a. float
b. int
C. str
d.
val
Python
Answers
Answer:
i think the answer is c so yea
3 things in terms of photography to learn about.
Answers
The three important principle in photography are;
Photography is about light. Without it, you couldn't even take images, let alone excellent ones.
The quality of light varies from one to photograph, yet it is always what gives your photographs their underlying structure. It doesn't get any more basic than that.
Most of us snap photos because something catches our attention.
Unsurprisingly, that "something" is your subject.
If you're explaining a photograph to someone else, the topic is most likely the first thing you'll mention.
Finally, the composition is the third and most important aspect of every shot.
Simply said, composition is the arrangement of the things in your shot. It includes your camera position, the connections between photo elements, and the things you accentuate, deemphasize, or altogether eliminate. Composition is the method through which you communicate your tale.
Learn more about photography:
https://brainly.com/question/30685203
#SPJ1
The typical cellphone screen can accommodate no more than 100 characters.
a. True
b. False
Answers
False, An improvement over computer instant messaging is text messaging on a cellphone or personal digital assistant.
Text messaging places an even higher emphasis on conciseness because the average cellphone screen can only hold 160 characters, and the keyboard is much less adaptable. See 5-3: Communications through electronic mail
You can read on-screen text or distinguish colours with the use of colour filters.
There are four settings that may be used to distinguish between colours. To change the filter's intensity after selecting one (apart from Grayscale), pick Intensity:
Red/Green Grayscale Filter (for Protanopia)
Red/Green Filter (for Deuteranopia)
Yellow/Blue Filter (for Tritanopia)
Select the Color Tint option to make the text on your screen easier to read. To make changes, choose Hue or Intensity.
Students who use assistive technology must make a separate request for each hardware or software item. It must be the same technology that has been requested.
Learn more about Messaging here:
https://brainly.com/question/14921620
#SPJ4
Using these Web sites for guidance, write a definition in your own words for five of the terms listed below.
gigabyte
intranet
pixel
telecommunication
modem
raster graphic
vector graphic
digital
GUI
Question # 1
Long Text (essay)
Write your definitions for the five terms of your choice.
Answers
Answer:
Gigabyte: Unit of measurement, is 10^9 bytes.
Intranet: Network that is used for sharing info, and other services.
Pixel: Creates a image, it is the smallest element on a display on a device.
Modem: Converts signals produced by a computer or another type of device.
Digital: Problem solving by any capable class device.
Explanation:
Short and simple.
Fill in the blanks to complete the “countdown” function. This function should begin at the “start” variable, which is an integer that is passed to the function, and count down to 0. Complete the code so that a function call like “countdown(2)” will return the numbers “2,1,0”.
Answers
Answer:
Check the code down below
Explanation:
You can use this code:
for i in range(5,-1,-1):
print(i)
This will print:
5
4
3
2
1
0
5 is changeable by the way!
The complete the “countdown” function. This function should begin at the “start” variable, which is an integer that is passed to the function, and count down to 0 is in the explanation part.
What is programming?The process of creating a set of instructions that tells a computer how to perform a task is known as programming.
Computer programming languages such as JavaScript, Python, and C++ can be used to create programs.
Here is the code to complete the “countdown” function:
def countdown(start):
for i in range(start, -1, -1):
print(i, end=",")
The countdown function takes an integer start as an argument and counts down from start to 0 using a for loop.
The range function is used to generate an integer sequence from start to 0, with a step size of -1. (i.e., counting backwards).
Thus, each integer in the sequence, separated by commas, is printed using the print function.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ2
all of the fields added to the form are from the customer table. because these controls are connected to a field in the database, they are called _____ controls.
Answers
The controls connected to fields in the database and added to the form are called "customer controls."
The term "customer controls" refers to the controls on a form that are directly connected to fields in the customer table of a database. These controls serve as a means of collecting and displaying information from the customer table within the form interface.
By linking these controls to specific fields in the database, any changes made through the form will be reflected in the corresponding customer records. This enables seamless data integration and ensures that the information entered or retrieved through the form is directly associated with the customer data in the database.
Examples of customer controls may include input fields for customer name, address, contact information, or dropdown menus for selecting customer categories or preferences. Overall, customer controls facilitate efficient data management and enhance the user experience by providing a direct connection between the form and the customer table in the database.
Learn more about database here:
https://brainly.com/question/6447559
#SPJ11
It is frightening, and even dangerous, to come back to a dark house at the end of a working day. There are many different types of outdoor lights on the market. Emily wants the outdoor lights at her home to be on in the evenings when she comes from work. She does not want to leave the lights on all day as this will be a waste of electricity and unnecessarily expensive. She needs some type of device that detects the fading daylight. This will cause her outside house lights to switch on automatically once the correct level of darkness has been reached.
motivate what kind of system is needed?
Answers
How do i fix this? ((My computer is on))

Answers
Answer:
the picture is not clear. there could be many reasons of why this is happening. has your computer had any physical damage recently?
Answer:your computer had a Damage by u get it 101 Battery
and if u want to fix it go to laptop shop and tells him to fix this laptop
Explanation:
While importing data from a web page into excel, creating a refreshable web query is used to ______.
Answers
While importing data from a web page into excel, creating a refreshable web query is used to keep data dynamic or updatable.
Each column of your source data becomes a field you may utilize in the report when you construct a Pivot Table report. Multiple rows of information from the original data are condensed into fields. On the pivot table, click. This causes the ribbon's PivotTable Tools tab to appear. Click Field Headers in the Show group of the Analyze or Options tab to toggle between displaying and hiding field headers. Slicers are a potent tool for filtering data in Pivot Tables in Sheets. With just one click, they make it simple to update values in pivot tables and charts. The equal sign (=) usually comes first in a formula. The characters that come after the equal sign are interpreted by Excel for the Web as a formula.
Learn more about headers here-
https://brainly.com/question/15163026
#SPJ4
An instance of ________ describes programming errors, such as bad casting, accessing an out-of-bounds array, and numeric errors. RuntimeException Exception Error Throwable NumberFormatException
Answers
An instance of Runtime Exception describes programming errors, such as bad casting, accessing an out-of-bounds array, and numeric errors.
What is a runtime exception?The Runtime Exception is known to be the parent class that is often seen in all exceptions of the Java programming language that are known to crash or break down the program or application when they happen.
Therefore, An instance of Runtime Exception describes programming errors, such as bad casting, accessing an out-of-bounds array, and numeric errors.
Learn more about Runtime Exception from
https://brainly.com/question/3620278
#SPJ1
To get a GIMP file into a different format, you need to
it.
a) trace
b) optimize
c)save
d)export
Answers
Answer:
d
Explanation:
a full binary tree is a rooted tree where each leaf is at the same distance from the root and each internal node has exactly two children. inductively, a full binary tree of depth 0 is the one-node tree n, and a full binary tree of depth d 1 is a rooted tree whose two subtrees are each full binary trees of depth d. how many nodes, and how many edges, are in a full binary tree of depth d? prove your answer using the inductive definition given in this problem.
Answers
We can prove that a full binary tree of depth d has 2^(d+1) - 1 nodes and 2^d edges by induction on the depth of the tree.
A full binary tree of depth 0 has only one node, so it has 0 edges. Therefore, the formula holds for depth 0Inductive StepAssume that a full binary tree of depth k has 2^(k+1) - 1 nodes and 2^k edges. We want to show that a full binary tree of depth k+1 also satisfies the formulA full binary tree of depth k+1 can be constructed by adding two subtrees, each of depth k, to a single root node. By the inductive hypothesis, each of these subtrees has 2^(k+1) - 1 nodes and 2^k edges. Therefore, the total number of nodes in the tree of depth k+1 is:2(2^(k+1) - 1) + 1 = 2^(k+2) - 2 + 1 = 2^(k+2) - 1The extra "+1" is for the root node. Similarly, the total number of edges in the tree of depth k+1 is:2^k + (2^k - 1) + 1 = 2(2^k) = 2^(k+1)The extra "+1" is for the edge connecting the root node to its children.Therefore, by induction, a full binary tree of depth d has 2^(d+1) - 1 nodes and 2^d edges.
To learn more about induction click on the link below:
brainly.com/question/31462867
#SPJ11
A(n)
is a central computer that enables authorized users to access networked resources.
A. LAN
B. server
C. Peripheral
D. Application
Answers
Answer:
it's B -SERVER
Explanation:
on odyssey ware