write a c# program to control the payroll system of an
organization (application of polymorphism). Create appropriate
derived classes and implement class methods/properties/fields
Directions:
Create a
Answers
Sure! Here's an example of a C# program that demonstrates the use of polymorphism in a payroll system:
```csharp
using System;
// Base class: Employee
class Employee
{
public string Name { get; set; }
public double Salary { get; set; }
public virtual void CalculateSalary()
{
Console.WriteLine($"Calculating salary for {Name}");
// Salary calculation logic
}
}
// Derived class: PermanentEmployee
class PermanentEmployee : Employee
{
public double Bonus { get; set; }
public override void CalculateSalary()
{
base.CalculateSalary();
Console.WriteLine($"Adding bonus for {Name}");
Salary += Bonus;
}
}
// Derived class: ContractEmployee
class ContractEmployee : Employee
{
public int HoursWorked { get; set; }
public double HourlyRate { get; set; }
public override void CalculateSalary()
{
base.CalculateSalary();
Console.WriteLine($"Calculating salary based on hours worked for {Name}");
Salary = HoursWorked * HourlyRate;
}
}
// Main program
class Program
{
static void Main()
{
// Creating objects of different employee types
Employee emp1 = new PermanentEmployee { Name = "John Doe", Salary = 5000, Bonus = 1000 };
Employee emp2 = new ContractEmployee { Name = "Jane Smith", Salary = 0, HoursWorked = 160, HourlyRate = 20 };
// Polymorphic behavior: calling the CalculateSalary method on different employee objects
emp1.CalculateSalary();
Console.WriteLine($"Final salary for {emp1.Name}: {emp1.Salary}");
emp2.CalculateSalary();
Console.WriteLine($"Final salary for {emp2.Name}: {emp2.Salary}");
}
}
```
In this example, we have a base class called `Employee` with a `Name` and `Salary` property. The `CalculateSalary` method is declared as `virtual` in the base class, allowing it to be overridden in derived classes.
We have two derived classes, `PermanentEmployee` and `ContractEmployee`, which inherit from the `Employee` base class. Each derived class has its own implementation of the `CalculateSalary` method, specific to the type of employee.
In the `Main` method, we create objects of the derived classes and demonstrate polymorphism by calling the `CalculateSalary` method on different employee objects. The appropriate version of the method is automatically invoked based on the actual type of the object at runtime.
This allows us to have different salary calculation logic for different types of employees, demonstrating the power of polymorphism in the context of a payroll system.
To know more about Polymorphism refer to:
brainly.com/question/14078098
#SPJ11
Related Questions
Write an LMC program as follows instructions:
A) User to input a number (n)
B) Already store a number 113
C) Output number 113 in n times such as n=2, show 113
113.
D) add a comment with a details exp
Answers
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
The LMC program can be written as follows:
sql
Copy code
INP
STA 113
INP
LDA 113
OUT
SUB ONE
BRP LOOP
HLT
ONE DAT 1
Explanation:
A) The "INP" instruction is used to take input from the user and store it in the accumulator.
B) The "STA" instruction is used to store the number 113 in memory location 113.
C) The "INP" instruction is used to take input from the user again.
D) The "LDA" instruction loads the value from memory location 113 into the accumulator.
E) The "OUT" instruction outputs the value in the accumulator.
F) The "SUB" instruction subtracts 1 from the value in the accumulator.
G) The "BRP" instruction branches back to the "LOOP" label if the result of the subtraction is positive or zero.
H) The "HLT" instruction halts the program.
I) The "ONE" instruction defines a data value of 1.
The LMC program takes an input number (n) from the user, stores the number 113 in memory, and then outputs the number 113 n times.
To know more about LMC program visit :
https://brainly.com/question/14532071
#SPJ11
which crash recovery policy is usually implemented by today's database systems
Answers
The crash recovery policy typically implemented by today's database systems is the Write-Ahead Logging (WAL) protocol.
The Write-Ahead Logging (WAL) protocol is widely used as the crash recovery policy in modern database systems. It ensures durability and consistency of data in the event of a system crash or failure. Under the WAL protocol, any modification to the database is first recorded in a log file before being applied to the actual data pages. This log file contains a sequential record of all changes made to the database, including both the old and new values of modified data. The log entries are written to disk in a stable storage location before the corresponding data modifications are applied. This guarantees that in the event of a crash, the system can recover by replaying the log entries and restoring the database to its last consistent state.
By using the WAL protocol, database systems can provide crash recovery mechanisms that ensure data integrity and minimize the risk of data loss. The WAL protocol has become a standard practice in modern database systems due to its effectiveness in handling system failures and maintaining the reliability of the database.
Learn more about database here: https://brainly.com/question/31449145
#SPJ11
What is Hypertext Transfer Protocol?
А. The language used to build web pages
B. A set of rules that allows for exchange of information on the web
C. The language used by computers to exchange information on the web
D. A set of rules that defines what search engines can do
Answers
Answer:
B
Explanation:
Web browsers use HTTP to send and receive information to and from the web.
Answer:
The correct answer is B.
I know someone else answered this but just in case people wanted clarification, it is indeed B.
Hope this help someone :3
Incorporating, paraphrasing, restating or generating in a new form information that is already classified and marking the newly developed material consistent with the markings that apply to the source information.
Answers
This form if information is classified as Derivative Classification.
What is Derivative Classification ?Derivative classification is the act of integrating, paraphrasing, restating, or creating in new form information that has previously been classified and classifying the newly created material in accordance with the source material's classification markings.
The protection and integrity of classified information are upheld by derivative classifiers. These people need to be knowledgeable with classification management and marking procedures as well as the subject matter of the classified information.
The derivatively classified document will retain any portion markings from the original document. The remaining areas will all be clearly designated.
To learn more about Derivative Classification refer to :
https://brainly.com/question/29977853
#SPJ4
Who designed the Analytical Engine in the 1930s?
Charles Babbage
Steve Wozniak
Alan Turing
Bill Gates
Answers
Answer:
Charles BabbageExplanation:
Charles Babbage designed the Analytical Engine in the 1930s.Thank you ☺️☺️
Answer:
Charles Babbage
Explanation:
Charles Babbage designed a general-purpose calculating machine, the Analytical Engine, which is considered to be the precursor of the modern-day computer. He was never able to finish it.
- Edge 2022
what is iso14000? what is its potential impact on key stakeholders
Answers
An international standard family known as ISO 14000 offers foundations and recommendations for environmental management within organisations.
The International Organisation for Standardisation (ISO) created a collection of guidelines to assist companies and other organisations in putting in place efficient environmental management systems.
Depending on their positions and interests, different important stakeholders may experience different effects of ISO 14000. Among the possible effects are:
Organisations: ISO 14000 can assist organisations in increasing their environmental performance and efficiency, lowering their resource and waste usage, and adhering to the necessary environmental standards.Customers: Customers can be assured by ISO 14000 that an organisation has adopted sound environmental management procedures that have resulted in the creation of environmentally friendly goods and services.Thus, by advancing environmental sustainability, strengthening organisational performance, enhancing reputation, and building a culture of environmental responsibility, ISO 14000 has the potential to have a beneficial influence on important stakeholders.
For more details regarding environmental sustainability, visit:
https://brainly.com/question/4677073
#SPJ4
As you already know, a stack is a data structure realizing the so-called LIFO (Last In - First Out) model. It's easy and you've already grown perfectly accustomed to it.
Let's taste something new now. A queue is a data model characterized by the term FIFO: First In - Fist Out. Note: a regular queue (line) you know from shops or post offices works exactly in the same way - a customer who came first is served first too.
Your task is to implement the Queue class with two basic operations:
put(element), which puts an element at end of the queue;
get(), which takes an element from the front of the queue and returns it as the result (the queue cannot be empty to successfully perform it.)
Follow the hints:
use a list as your storage (just like we did in stack)
put() should append elements to the beginning of the list, while get() should remove the elements from the list's end;
define a new exception named QueueError (choose an exception to derive it from) and raise it when get() tries to operate on an empty list.
Complete the code we've provided in the editor. Run it to check whether its output is similar to ours.
Expected output
1 dog False Queue error
Answers
Using knowledge in computational language in JAVA it is possible to write a code that put() should append elements to the beginning of the list, while get() should remove the elements from the list's end; define a new exception named.
Writting the code:var Stack = function(){
this.top = null;
this.size = 0;
};
var Node = function(data){
this.data = data;
this.previous = null;
};
Stack.prototype.push = function(data) {
var node = new Node(data);
node.previous = this.top;
this.top = node;
this.size += 1;
return this.top;
};
Stack.prototype.pop = function() {
temp = this.top;
this.top = this.top.previous;
this.size -= 1;
return temp;
};
var Queue = function() {
this.first = null;
this.size = 0;
};
var Node = function(data) {
this.data = data;
this.next = null;
};
Queue.prototype.enqueue = function(data) {
var node = new Node(data);
See more about JAVA at brainly.com/question/12975450
#SPJ1

which of these is not enumerated as a motivation to create accessible web content?
Answers
Answer:
Which of what?
Explanation:
Question 1 of 10
Which step happens first after a switch receives a message that includes a
MAC address?
OA. The switch receives a reply from the message's receiving device.
B. The switch sends the message to a random device on the
network.
OC. The switch looks up the receiving device's MAC address in a
switching table.
OD. The switch forwards the message to the port of the receiving
device.
SUBMIT
Answers
The step that happens first after a switch receives a message that includes a MAC address is that "The switch looks up the receiving device's MAC address in a switching table." (Option C)
What is a MAC Address?
A media access control (MAC) address is a one-of-a-kind identifier assigned to a network interface controller for use as a network address in intra-network communications. This is a widespread use in most IEEE 802 networking technologies, such as Ethernet, Wi-Fi, and Bluetooth.
What is a switch?
A network switch is a piece of networking gear that links devices on a computer network by receiving and forwarding data to the target device using packet switching.
Learn more about MAC Addresses:
https://brainly.com/question/24812654
#SPJ1
what is the range of values used whe setting velocity?
A. 0% to 100%
B. -100% to 100%
C. 0% to 200%
D. -100% to 200%
Answers
Answer:
A. 0% to 100%
Explanation:
Velocity can be defined as the rate of change in displacement (distance) with time. Velocity is a vector quantity and as such it has both magnitude and direction.
Mathematically, velocity is given by the equation;
\( Velocity = \frac{distance}{time} \)
The range of values used when setting velocity is 0% to 100%.
Hence, when working on a virtual reality (VR) robot, you should use a range of 0% to 100% to the set the value of velocity. This range of values are used to denote the rate at which the robot moves i.e its forward and backward motion (movement).
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
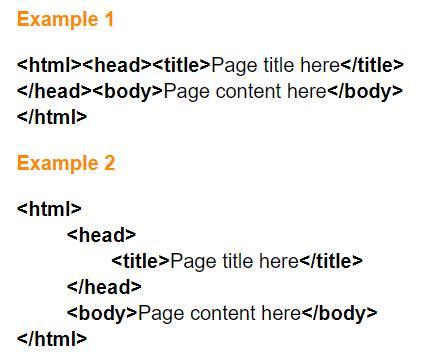
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
George took a photograph of a guitarist while he was playing a slow, somber song. Which technical aspect of photography has he used to convey
this emotion?
Answers
The technical aspect of photography that George has used to convey the slow, somber emotion of the guitarist's playing is the use of shutter speed. By using a slow shutter speed, George has captured a longer exposure time, allowing the camera to capture the motion of the guitarist's hands as he plays the guitar, creating a sense of movement and flow. The resulting image would likely show blurred motion, conveying the emotion of the slow, somber song being played.
- I Hope This Helps! :)
• Please Give Brainliest
in cell D19, write a formula that contains the difference between cells D18 and E18
ans the numbers in D18 and E18 are 9 and 7

Answers
In the Microsoft Excel sheet, cell D19, you can write the formula =D18-E18 to calculate the difference between cells D18 and E18.
What is the rationale for the above response?The rationale for this formula is that it subtracts the value in cell E18 from the value in cell D18, giving the difference between the two numbers. In this case, with 9 in cell D18 and 7 in cell E18, the formula will evaluate to 2, which is the difference between the two numbers.
Excel formulas are important because they allow users to perform calculations and analyze data in a spreadsheet. They save time and effort by automating repetitive tasks, and they provide a quick and easy way to make decisions based on data.
Learn more about Excel Formula:
https://brainly.com/question/29280920
#SPJ1
What is the meaning of unwanted software?.
Answers
Unwanted software are programs that alter the Windows experience without your consent or control. This can take the form of modified browsing experience, lack of control over downloads and installation, misleading messages, or unauthorized changes to Windows settings
Discuss briefly four types of websites and the criteria you will use to evaluate the content of a website
Answers
Answer: I would look at who made it, what date it was published, what it is about and if it says .gov, .com or etc.
Explanation:
In five to ten sen
sentences, describe the procedure for sending an e-mail message.
Answers
Answer:
Explanation:
Pre-Steps: Click the "Compose" button near the top left corner of your screen. Then a window titled "New Message" should pop up.
1. Type who you are sending it to in the "To ____ column."
2. Type the subject - make it as specific as possible. I use the following template for writing a subject:
Event - Reason for sending - How you know them
EX: If you are sending a email to your teacher you could put:
Per 6 Biology - Help for homework - Student.
3. Next, type the message. This step varies depending on why you are sending the message. I say formality is always a should in any case. Sound crisp and mature
4. Send it. Be sure you read over the email before sending and make sure the email makes sense. Use proper grammar and the editor tool for spelling.
5. Click the blue send button. You can also click the down arrow key to schedule send, which makes the email send automatically at a specific time. If you click it, a window will pop up, in which you can pick the date and time for the email to send.
6. Once you are finished sending, your sent email and the replies (if any) from the recipients should appear in the "Sent" folder in the toolbar near the left of your screen.
Hope this helped!
What make appertizer look healthier?
Answers
Answer:
Fruits, vegetables or drinks but it needs to be fruit wise in order to be healthier
a information flow relates to the information that is produced by a company and sent along to another organization
Answers
That's correct! Information flow refers to the movement of information within and between organizations.
In a business context, this could include communication between different departments or teams within the same company, as well as communication with external partners, suppliers, or customers. Effective information flow is essential for ensuring that all relevant parties have access to the information they need to make informed decisions and carry out their work effectively.
In addition to internal information flow, organizations also engage in information exchange with external entities, such as suppliers, customers, partners, or regulatory bodies. This external information flow involves sharing information related to orders, sales, market trends, industry standards, compliance, and other relevant aspects.
It's important for organizations to establish effective communication channels, information systems, and protocols to facilitate smooth information flow, ensure accuracy and reliability of information, and enhance overall organizational efficiency and effectiveness.
So, while information flow is crucial for organizations, it primarily refers to the movement of information within the organization rather than specifically between organizations.
Learn more about Information flow refers to the movement from
https://brainly.com/question/29734722
#SPJ11
Does white space have visual weight? Yes or No
Answers
Answer:
no. (more info below)
Explanation:
white space appears to have no visual weight because it's seen as empty. Every body put in the room will appear to be heavier because of the volume surrounding it.
hope this helped!
Answer:
no
Explanation:
it's because it appears to be empty.
1) Lux Corporation has issued 2,500 shares of common stock and 500 shares of preferred stock for a lump sum of $95,000 cash.Instructions (a) Give the entry for the issuance assuming the par value of the common stock was $8 and the fair value $28, and the par value of the preferred stock was $35 and the fair value $65. (Each valuation is on a per share basis and there are ready markets for each stock.) (b) Give the entry for the issuance assuming the same facts as (a) above except the preferred stock has no ready market and the common stock has a fair value of $30 per share.
Answers
The journal entry for Lux Corporation's issuance of 2,500 shares of common stock and 500 shares of preferred stock, assuming common stock par value of $8 and fair value of $28, and preferred stock par value of $35 and fair value of $65, would be:
Common Stock: $70,000
Paid-in Capital in Excess of Par: $62,500
Preferred Stock: $30,000
In the first step, we determine the total par value of the common stock and the preferred stock by multiplying the number of shares issued by their respective par values. For the common stock, it would be 2,500 shares x $8 = $20,000, and for the preferred stock, it would be 500 shares x $35 = $17,500.In the second step, we calculate the amount of paid-in capital in excess of par for each stock. This is done by subtracting the par value from the fair value of each stock. For the common stock, it would be $28 - $8 = $20 per share, and since 2,500 shares were issued, the total amount would be $20 x 2,500 = $50,000. For the preferred stock, it would be $65 - $35 = $30 per share, and since 500 shares were issued, the total amount would be $30 x 500 = $15,000.Finally, we record the journal entry by debiting the appropriate accounts and crediting the corresponding accounts. The common stock and preferred stock accounts are debited for their respective par values, while the paid-in capital in excess of par accounts are credited for the difference between the fair value and par value of each stock.Learn more about common stock
brainly.com/question/11453024
#SPJ11
another word for Arithmetic Logic Unit
Answers
Answer:
ALU
Explanation:
just to say it faster than having to say it...
Answer:
ALU
Explanation:
ALU is a functional part of CPU which perform arithmetic and logical operations.
GIVING BRAINLIEST!
1. The Monte Carlo method uses ___________ for computer simulations
2. The Monte Carlo method was first developed during World War II to test __________
Answers
In 1993, Gordon et al. published the first use of a Monte Carlo resampling procedure in Bayesian statistical inference in their important work.
What Monte Carlo method uses for computer?In forecasting and decision-making, the Monte Carlo approach is a computerized mathematical tool that enables humans to statistically account for risk.
A mathematical method called Monte Carlo Simulation creates random variables to model the risk or uncertainty of a particular system.
Therefore, The Monte Carlo method uses mathematics for computer simulations. The Monte Carlo method was first developed during World War II to test decision improve making.
Learn more about Monte Carlo here:
https://brainly.com/question/15350591
#SPJ1
Drag each tile to the correct box.
Classify the benefits and drawbacks of doing business on the internet.
cheaper to set up and run a business
access to a large amount of customer
information
difficult to verify the quality of products
BENEFITS
risk of cyberattacks
attracts investments from a larger number of
sources
can drive small enterprises out of business
DRAWBACK

Answers
Answer:
Explanation:
Benefits
Cheaper to set up and run a business.
Access to a large amount of customer information
Attracts investments from a larger number of sources.
Drawbacks
Can drive small enterprises out of business.
Risk of Cyberattacks
difficult to verify the quality of products
Given a system, it would need a time to access register, b time to access cache, and c time to access memory. If one-level paging without cache is utilized for user process memory management, when CPU wants to fetch an instruction, the effective access time is
Answers
The effective access time for one-level paging without cache is `a+b+c`
When CPU wants to fetch an instruction and one-level paging without cache is utilized for user process memory management, the effective access time is given by the formula;`
Effective access time= a + (1-p) (b+c)`
where;a = time to access register
b = time to access cache
c = time to access memory
p = probability of finding page in cache
(1-p) = probability of page fault
For one-level paging, all user process pages are stored in the memory (the page table is also stored in memory) because there is no cache. This means that the probability of finding a page in cache (p) is zero since there is no cache.
Therefore the formula above can be simplified to;
`Effective access time = a + (1-0) (b+c)` `= a + b + c`
Hence the effective access time for one-level paging without cache is `a+b+c`.
Learn more about paging https://brainly.com/question/32389411
#SPJ11
Select the correct text in the passage.
Which software development agreement helps distribute risks between the software developer, client, and third parties?
Software developers and clients make software development agreements that legally define duties, payment, and ownership. Unless the developer is the client's employee, the software developer owns the copyright of the software Software development agreements also delineat
maintenance tasks in terms of validity, time, and criteria. These include as UPDATES, UPGRADES, WARRANTIES, and SUPPORT SERVICES.
The options for this question are the capitalized words: updates, upgrades, warranties, support services
Answers
Answer:
support services
Explanation:
!! please help !!
What is a nameable container used for organizing and storing data?

Answers
Answer:
Variable
Explanation:
Variable is a container for storing the data. In any programming language, a variable is used to store the data or the value that is used in the program for execution
Answer:
D. Varaible
Explanation:
A top investment bank is in the process of building a new Forex trading platform. To ensure high availability and scalability, you designed the trading platform to use an Elastic Load Balancer in front of an Auto Scaling group of On-Demand EC2 instances across multiple Availability Zones. For its database tier, you chose to use a single Amazon Aurora instance to take advantage of its distributed, fault-tolerant, and self-healing storage system. In the event of system failure on the primary database instance, what happens to Amazon Aurora during the failove
Answers
Answer:
Following are the solution to the given question:
Explanation:
Initially, Aurora will try and establish a new DB instance in the same AZ as the previous example. When Aurora can do it, he will try to create a new DB instance in another AZ.
Aurora will try and construct a new DB instance in the same disponibility zone as the original example if there is not an Amazon Aurora Replica (i.e. single instance) that does not execute Aurora Serverless. The replacement of the original example was better managed and may not work if there is, for example, an issue that impacts broadly the entire Access Service.
which buffer system is the best choice to create a buffer with ph=7.30 ?
Answers
The best buffer system for creating a buffer with a pH of 7.30 is the bicarbonate buffer system, which is one of the most important buffer systems in the human body.
This system consists of a weak acid, carbonic acid (H₂CO₃), and its conjugate base, bicarbonate ion (HCO₃⁻). The bicarbonate buffer system maintains a pH close to 7.4 in the blood, which is crucial for proper physiological functioning.
To create a buffer with a pH of 7.30, you can adjust the concentrations of carbonic acid and bicarbonate ion using the Henderson-Hasselbalch equation. By doing so, you can achieve a slightly more acidic environment while maintaining the buffering capacity of the bicarbonate buffer system.
Learn more about buffer at:
https://brainly.com/question/14007876
#SPJ11
Complete the sentence.
involves placing a device on the network that captures all the raw data in the network traffic to try to find something valuable
A. Dumpster diving
B. Packet sniffing
C. Social engineering
D. Phishing
Answers
Answer:
D. Phishing
Explanation:
Answer: B. Packet sniffing
Explanation:
right on edge
Jemima has finished formatting her main headings. She now wants to format her two subheadings. She wants to apply the format of her first subheading, not the format of the main heading, to the second subheading. Which feature of Word would help her to complete this task efficiently?
Answers
Answer:
the Format Painter feature
Answer:
the format painter feature
Explanation: