when are local variables initialized? group of answer choices local variables are initialized when the method is called. local variables are initialized with a default value before a constructor is invoked. you must initialize local variables in a method body. you must initialize local variables in the constructor.
Answers
Local Variables Initialization creates a fresh instance of the variable. It has to be of the same type as the declaration type. The string "Hello World" is used as the variable a's initial value in the code above. The assertion that follows gets the same outcome exactly.
WHY LOCAL VARIABLES ONLY?Only local variables in Java have a relatively constrained scope and lifetime. Additionally, they follow a predictable execution path that the compiler is aware of. These parameters are limited to the procedure. The compiler can quickly tell a programmer to initialise a variable before using it by identifying where the variable is declared. A programme bug could potentially occur when a variable is utilised without being initialised. Additionally, initialising each variable with its default value slows down speed. Actually, the compiler is helping to improve the programme. What should be asked is why the compiler does not assist in using a static/instance variable prior to initialization.the degree of intricacy or the variety of access points to those variables. The execution route of a method is really obvious. The variable's use can be tracked by the compiler all the way back to its declaration. The compiler cannot recognise a particular procedure for setting a value in a static or instance variable. Initialization may take place in a different application entirely, and consumption may occur elsewhere. They are given default values because there is no clear path and the path to map is not a thin line. A default value is unquestionably preferable to an uncertain or random value. These variables can have any value on them if they are not initialized, which could include
The solution to that query is the variables are not initialized, they may contain anything, from inconsequential information to sensitive information.
Learn more about Local Variables from here:
https://brainly.com/question/16978529
#SPJ4
Related Questions
Please! I need help matching this.
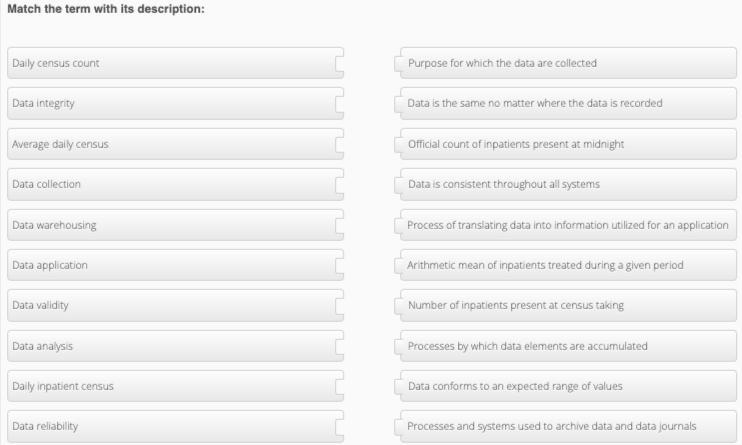
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
who invented the computer?
when was it made?
can u tell me the name of the oldest computer?
when did the first laptop come out?
Answers
Hope it helps you
pls mark my answer as brainliest
Answer:
1 and 2: Charles Babbage invented the computer (he was an English mechanical engineer and polymath) Charles Babbage was deemed the "father of the computer", he thought up and created the very first mechanical computer at the beginning of the 19th century.
3: the first computer was named the ubiquitous x86-powered workhorse of desktop and portable computing. All latest PCs are descendants of the earliest from IBM, the original model 5150 which made its first appearence in August 1981.
4: The first laptop computer available to the public was the Osborne. the Osborne Computer Corporation issued this exact model to the public in the year 1981. It ran at a large price of $1795. At the time of discharge, the screen was about five inches long and the keyboard was on the cover of the computer.
i did a lot of research for this, lol. hope it helps.
(i promise i did not plagerise)
____________ refers to having some level of control over potential secondary uses of one s personal information.
A. Information security
B. Information assurance
C. Data collection threat
D. Accessibility
E. Information privacy
Answers
E.) Information privacy refers to having some level of control over potential secondary uses of one's personal information.
Information privacy encompasses the ability of individuals to control how their personal information is collected, used, and disclosed by organizations or entities. It involves safeguarding personal data from unauthorized access, ensuring that individuals have the right to consent to the collection and use of their information, and providing mechanisms to exercise control over the sharing or selling of their data. Information privacy is essential in protecting individuals' rights and maintaining trust in the digital age where personal information is constantly being collected and processed. Measures such as data protection laws, privacy policies, consent mechanisms, and data minimization practices contribute to upholding information privacy and giving individuals the power to decide how their personal information is utilized.
learn more about Information privacy here:
https://brainly.com/question/31544382
#SPJ11
In the decision-making process, after you have chosen the right solution, what is the next step?
Answers
Answer:
Implementing the right solution.
Explanation:
There is little point in taking decisions if it stays in the paper. If the best of the possible alternatives have been identified, it must be properly implemented to accomplish the aim it was chosen for. When a decision has been made, it should be implemented, i.e. enacted, into practice. Because of poor execution, a successful decision may become ineffective. A participatory approach can be an efficient way of enforcing such decisions successfully.
True or False: While a field extends throughout space, it lessens with distance until it is undetectable. Question 21 options: True False.
Answers
Answer:
true
Explanation:
If C2=20 and D2=10 what is the result of the function = mathcal I F(C2=D2,^ prime prime Ful "Open")?
Open
Unknown
Full
10
Answers
Excel IF functions are used to test conditions.
The result of the IF function is (a) Open
The function is given as: = IF(C2 = D2, "Full","Open")
Where: C2 = 20 and D2= 10
The syntax of an Excel IF conditional statement is: = IF (Condition, value_if_true, value_if_false)
The condition is: IF C2 = D2
The values of C2 and D2 are: 20 and 10, respectively.
This means that, 20 does not equal 10.
So, the value_if_false will be the result of the condition.
In other words, the result of the IF function is (a) Open
Read more about Excel functions at:
https://brainly.com/question/10307135
If you had an idea for a new software company, what would be the best approach to help make it a successful business?
-develop a business plan to describe how to maintain and grow revenues
-go back to school to get a degree in IT business administration
- hire employees who understand the software development industry
-seek out financial support for venture capital, angel investors and grants
Answers
Answer:
a
Explanation:
Two adjacent vertices can be part of the same MIS. True or False
Answers
The statement "Two adjacent vertices can be part of the same MIS" is false. A maximum independent set (MIS) is defined as a set of vertices in a graph such that no two vertices in the set are adjacent. In other words, each vertex in the MIS has no direct connections to any other vertex in the set. This is why it is called an independent set.
If two adjacent vertices were to be part of the same MIS, it would contradict the definition of an MIS because adjacent vertices have an edge connecting them. Therefore, if one vertex is in the MIS, its adjacent vertex cannot be included in the same MIS.
To illustrate this concept, let's consider a simple example of a graph with four vertices, A, B, C, and D. If A and B are adjacent vertices and part of the same MIS, then C and D cannot be in the MIS because they are adjacent to A and B. Therefore, an MIS in this graph could be either {A, C} or {B, D}.
In conclusion, two adjacent vertices cannot be part of the same MIS as an MIS is defined as a set of vertices with no direct connections to each other.
To learn more about, adjacent
https://brainly.com/question/31458050
#SPJ11
MIS:
False. Two adjacent vertices can be part of the same MIS.
What is the device used for the calculations of payment and balancing the accounts record s
Answers
Analyze the following output public class Test{ public static void main(String args[]){ int[] x={1,2,3,4}; //here declare array x with 1 2 3 4 int[] y=x; //here copy the x array into y array x=new int[2]; //here reintilized the array size which is 2 for(int i=0;i<.length;i++){ //here now array length is 2 it iterates 2 times System.out.print(x[i]+" ");
Answers
Answer:
The C language code is a class called Test that accepts an array, duplicates it, reinitializes the first array to the first two items of the previous array, and loops through the array to print both items.
Explanation:
public class Test{
public static void main(String args[]){
int[] x={1,2,3,4}; //here declare array x with 1 2 3 4
int[] y=x; //here copy the x array into y array
x=new int[2]; //here reintilized the array size which is 2
for(int i=0;i<.length;i++){ //here now array length is 2 it iterates 2 times
System.out.print(x[i]+" ");
}
}
The router is physically located in a server room that requires an ID card to gain access. You've backed up the router configuration to a remote location in an encrypted file. You access the router configuration interface from your notebook computer by connecting it to the console port on the router. You've configured the management interface with a username of admin and a password of password. What should you do to increase the security of this device
Answers
Explanation:
the best thing to do is to create a personal password with a two time passcode for better security of the device
Is a website with a top level domain of .org automatically trustworthy, or does its content need to be evaluated?
Answers
A website with a top-level domain of .org does not automatically guarantee trustworthiness, and its content should be evaluated.
The top-level domain .org is commonly associated with organizations, including non-profit entities. While many reputable and trustworthy organizations use the .org domain, it does not serve as a guarantee of credibility or reliability. It is essential to evaluate the content and credibility of the website itself, considering factors such as the source of information, author credentials, references, and overall reputation.
Websites with a .org domain can vary widely in terms of quality, accuracy, and trustworthiness. Just like any other website, it is crucial to critically assess the information presented, verify sources, and consider additional factors to determine the website's reliability. Relying solely on the domain extension is not sufficient to judge the credibility of the content.
You can learn more about website at
https://brainly.com/question/28431103
#SPJ11
You have just been hired by a large organization which uses many different AWS services in their environment. Some of the services which handle data include: RDS, Redshift, ElastiCache, DynamoDB, S3, and Glacier. You have been instructed to configure a web application using stateless web servers. Which services can you use to handle session state data
Answers
Answer:
Elasticache and DynamoDB
Explanation:
The session data can be stored on Elasticache and DynamoDB
ElastiCache is the best fit for front end data stores thereby ensuring a high performance with extremely high request rates and/or low latency requirements
What is true about the dilation?
On a coordinate plane, the image rectangle has points (0, 0), (0, 8), (9, 8), (8, 0). The pre-image has points (0, 0), (0, 2.5), (3, 2.5), (3, 0).
It is a reduction with a scale factor between 0 and 1.
It is a reduction with a scale factor greater than 1.
It is an enlargement with a scale factor between 0 and 1.
It is an enlargement with a scale factor greater than 1.
Answers
Hey hey hey! I recently took the test and the answer is D | (• ◡•)|
Answer:
The answer is A
Explanation:
Trust me I promise you its A
I chose D and got it wrong
model of social relations, individuals go through life embedded in a personal network of individuals to whom they give and from whom they receive social support.
Answers
According to the social convoy theory of social relationships, people live their lives as part of a personal network of people to whom they provide support and from whom they receive it.
What is the meaning of social convoy?The people that travel with us on the road of life are referred to as the social convoy. At every stage of development, this social grouping is a crucial component of successful adjustment and wellbeing.
As one matures and develops, they rely on these interactions and connections because all are social beings. Social convoy is a network of friends that travel through life with us and support us through both good and difficult times.
Learn more about social convoy from here:
https://brainly.com/question/7318152
#SPJ1
The complete question has been attached in text form:
In the social ______ model of social relations, individuals go through life embedded in a personal network of individuals to whom they give and from whom they receive social support.
Which file is usually the first file to be displayed when you navigate to a website?
1. home.html
2. Index.html
3. Template.html
4. Starter.html
Answers
Answer:
3. template.html
Explanation:
In the Percentage of Receivables method we first: Select an answer and submit. For keyboard navigation, use the up/down arrow keys to select an answer. a Use Accounts Receivable to estimate the ending balance for the allowance for doubtful accounts b Use Accounts Receivable to estimate the bad debt expense c Use Accounts Receivable to estimate the percentage of Net Credit Sales we won't collect on. d Use Net Credit Sales to estimate the percentage of Accounts Receivable we won't collect on.
Answers
In the Percentage of Receivables method, we use Accounts Receivable to estimate the ending balance for the allowance for doubtful accounts. This method helps us determine how much of the outstanding receivables may not be collected.
Determine the total amount of Accounts Receivable at the end of the accounting period. This includes all outstanding customer invoices. Calculate the estimated percentage of Net Credit Sales that will not be collected. Net Credit Sales refers to the total amount of sales made on credit, minus any sales returns and allowances.
Multiply the Accounts Receivable balance by the estimated percentage of Net Credit Sales we won't collect on. This gives us the estimated ending balance for the allowance for doubtful accounts.
To know more about Percentage visit:
https://brainly.com/question/32197511
#SPJ11
which term describes a process in which different stages are repeated when necessary
A. interface
B. prototype
C. recursive
D. troubleshoot
Answers
Answer:
I believe it B, because you need to test a prototype over and over to get it right.
Explanation:
Answer:
Recurcive would be the correct answer
Damia is a student working as a manager in a retail business. Her monthly income is RM4000, and she plans to enrol as an IT student in the Bachelor of Information Technology (BIT) programme at SEGi University. As she prepares to enrol, she comes across numerous specialisations such as computer networking, graphic design, and software engineering. However, each of these specialities requires separate laptop specifications. Find one laptop that Damia can make the most of. The laptops must meet the following specifications: - the laptops should have sufficient storage capacity for software and data. - the laptops should have the processing capability to support the delivery of the educational courses. - the network can be either a wired or a wireless network. For this part, you must recommend TWO (2) laptop computers that Damia could use for her educational courses. You must compare the offered laptops in terms of CPU architecture and functions, speed and memory characteristics, storage type and capacity, cost and benefits, pros and drawbacks, and why they could be used to achieve the desired solution. You can include a comparison of graphic cards, battery life, display screen, laptop weight, warranty, and so on to further illustrate why you would recommend certain laptops to the company. Based on the study, you may then recommend which laptop you believe would be best for Damia to utilise for the various courses.
Answers
Based on the given requirements, I would recommend Dell XPS 15 for Damia's educational courses in the Bachelor of Information Technology (BIT) program.
How to explain the informationCPU Architecture and Functions: The Dell XPS 15 can be configured with either an Intel Core i7 or i9 processor, providing powerful processing capabilities for running resource-intensive software and applications.
Speed and Memory Characteristics: It offers a high-speed processor and can be equipped with up to 32GB of RAM, ensuring smooth multitasking and efficient program execution.
Storage Type and Capacity: The laptop can be configured with PCIe solid-state drive (SSD) storage options, providing fast read/write speeds and ample storage capacity for software and data. A recommended configuration would be 512GB or 1TB SSD.
Learn more about computer on
https://brainly.com/question/24540334
#SPJ4
Creating compelling visuals for presentations requires people to learn what new tools?
A: gaming software
B: language translation software
C: design software
D: audio recording software
Answers
Creating compelling visuals for presentations requires people to learn what new tools "design software" (Option C)
What is a design software?Design software is used to produce, modify, and examine various forms of graphics and pictures, such as photography, 3D design, and the front end of websites.
Presentation software is a type of application software that enables users to build a presentation of ideas by connecting text, graphics, and audio/video. The presentation presents a tale or supports a speech or information presentation.
Although presentation software is classified as either business presentation software or general multimedia authoring software, the majority of presentation software applications already include tools that enable users to access both professional-looking business powerpoint presentation and general multimedia presentations.
A presentation program is another name for presentation software.
Learn more about presentation:
https://brainly.com/question/27326303
#SPJ1
Ask the user to enter a sentence. If the sentence has any mention of dog, tell the user (once) Dogs are cute. If the sentence has any mention of taco, tell the user (once) Tacos are tasty. Change each mention of dog to puppy. Change each mention of taco to burrito. Print the new sentence. Capitalization matters! For example, if theres a mention of Dog (note where the capital letter is), it should be changed to Puppy (note where the capital letter is). You will only need to look for mentions of dog, Dog, taco, and Taco. The plural forms are allowed but the final output for dog / Dog will not be grammatically correct, and this is ok. See sample output.
Answers
Answer:
Theses puppies are so cute!
Theses burritos are so yummy!
Would you like a taste of this delicious taco dog?
Explanation:
there you go plz may i have a brainilist??
What is the MINIMUM number of paths that would need to be broken to prevent Computing Device A from connecting with Computing Device E? a) 1 b) 2 c) 3 d) 4
Answers
Answer:
The answer is "Option c".
Explanation:
In the given question the device A is connected by 3 wires, contributing all of them, which also includes several connector paths. When all the wires of A are broken down, and if all of this leaves no routes that can be used. Even so, if it is done to E, it's also linked to four different routes. Its solution would've been C because its value will be the MINIMUM.
Answer:
c
Explanation:
Wireless communication requires the use of a ________ signal to ________ the message so it can be sent at a preassigned _________.
Answers
Wireless communication requires the use of a modulated signal to encode the message so it can be sent at a preassigned frequency.
In wireless communication systems, information is transmitted through the air using electromagnetic waves. These waves are created by varying or modulating a specific characteristic of the carrier signal, such as its amplitude, frequency, or phase. This process, known as modulation, is essential for converting the original message, which can be in the form of voice, data, or multimedia content, into a format suitable for wireless transmission.
The preassigned frequency is crucial in maintaining an organized and efficient communication system. Each wireless device operates within a specific frequency range, which is allocated by regulatory bodies like the Federal Communications Commission (FCC) or International Telecommunication Union (ITU). This allocation ensures that different communication services can coexist without causing interference with one another.
Modulation techniques, such as Amplitude Modulation (AM), Frequency Modulation (FM), or Phase Modulation (PM), are used to represent the message in the carrier signal. These techniques allow the message to be efficiently transmitted over long distances with minimal loss of quality. At the receiving end, a process called demodulation is used to extract the original message from the modulated carrier signal.
know more about Amplitude Modulation here:
https://brainly.com/question/10060928
#SPJ11
The coordinates that determine the position of an element in space are expressed as:
A. Different Shapes
B. 1, 2, 3
C. X, Y, Z
D. L, T, P
Answers
Answer:
xyz
Explanation:
think of it like a graph, you graph on the x, y, and z coordinates
Technician A says shims installed on the back of the brake pad correct pad alignment.
Technician B says the pad wear indicator creates a high frequency sound to warn the driver that
service is required.
Who is right?
Select the correct option and click NEXT.
O A only
OB only
OBoth A and B
ONeither A nor B
Answers
Technician A is right. Shims installed on the back of the brake pad are used to correct pad alignment.
Why is this so?They help ensure proper fitment and reduce noise or vibration caused by misalignment.
On the other hand, Technician B's statement about the pad wear indicator creating a high-frequency sound to warn the driver of required service is incorrect.
The pad wear indicator is designed to make a noise when the brake pads have worn down to a specific level, indicating the need for replacement. Therefore, the correct option is "A only."
Learn more about brake pads at:
https://brainly.com/question/31867050
#SPJ1
explain paper based system, web based system, early
personal computer technology and
electronic database base systems in 20 mins please
Answers
A paper-based system is a method of organizing and storing information using physical documents such as paper files, folders, and cabinets. In this system, data is recorded and stored on paper documents, which are then manually sorted, filed, and retrieved when needed.
Early personal computer technology refers to the early stages of personal computer development and usage. In the 1970s and 1980s, personal computers were introduced to the market, enabling individuals to have their own computer at home or in the office. These early personal computers were typically standalone devices that stored data on floppy disks or hard drives.
Electronic database-based systems are methods of organizing and storing information using electronic databases. In this system, data is stored and managed using specialized software that allows for efficient storage, retrieval, and manipulation of data.
To know more about organizing visit:
brainly.com/question/28363906
#SPJ11
during a managers meeting, maritza rolled her eyes three times, made a cynical remark, and slammed her notebook down on the table. maritza could be described as a
Answers
During the meeting, Maritza displayed behavior that suggests she may be feeling frustrated or disengaged.
What causes disengagement?Disengagement can be caused by various factors, including:
Lack of recognition or appreciation for workPoor communication or lack of feedback from managementInadequate training or development opportunitiesRolling her eyes, making a cynical remark, and slamming her notebook down on the table are all nonverbal cues that indicate she may be expressing a negative attitude or emotion. It's possible that she disagrees with what was said or is unhappy with the way the meeting is being conducted. However, it's important to note that these behaviors alone do not provide enough information to fully understand Maritza's thoughts or emotions.
Find out more on disengagement here: https://brainly.com/question/13534298
#SPJ1
The Euclidean algorithm - The Euclidean algorithm provides a wonderful way to
calculate the greatest common factor of 2 numbers. The greatest common factor,
which is the largest number that divides evenly into 1 or more numbers, is useful
for reducing fractions. The Euclidean algorithm works by dividing 1 number by
the other and finding the remainder. The 2 numbers are redefined, and then the
process is repeated. The process ends when the remainder is equal to 0.
Following is the pseudo code for the algorithm. In c++ use 145 and 87 to test your
program. The program will find the largest common factor of the numbers (the
answer should be 29).
Answers
The largest common factor of the numbers GCF (145, 87) is 29 when remainder R = 0, the GCF is the divisor, b, in the equation. GCF = 29.
How to Find the GCF Using Euclid's Algorithm?Do the division a ÷ b = c with remainder R given two whole integers where an is bigger than b.
Replace a with b, then R, and repeat the division.
Step 2 should be repeated until R=0.
When R=0, the greatest common factor, GCF, is the divisor, b, in the final equation.
Because the greatest common factor (GCF) and greatest common divisor (GCD) are interchangeable, the Euclidean Algorithm approach may also be used to discover the GCD.
145 ÷ 87 = 1 R 58 (145 = 1 × 87 + 58)
87 ÷ 58 = 1 R 29 (87 = 1 × 58 + 29)
58 ÷ 29 = 2 R 0 (58 = 2 × 29 + 0)
When remainder R = 0, the GCF is the divisor, b, in the last equation. GCF = 29
Since the remainder is zero, the algorithm stops and therefore, the GCF (145, 87) is 29.
To learn more about Euclid's Algorithm here:
https://brainly.com/question/13443044
#SPJ1
What elements does the array list contain after the following code is executed? int [] list ={2,18,6,−4,5,1};for (int i=0;i< list.length; i++)list [i]= list [i]+( list [i]/ list [θ]); \}
Answers
The correct answer is The code initializes an integer array list with six values: 2, 18, 6, -4, 5, and 1. The code then iterates through each element of the array using a for loop and updates the value of each element based on the following formula: list[i] = list[i] + (list[i] / list[θ]).
Note that the variable θ is not defined in the code, so it would cause a compilation error. Assuming that θ should have been initialized to 0, the code would result in a division by zero error at the last element of the array, since list[0] is equal to 2 and list[0] / list[θ] would result in a division by zero.
list[0] = 2 + (2 / list[0]) = 3
list[1] = 18 + (18 / list[0]) = 27
list[2] = 6 + (6 / list[0]) = 9
list[3] = -4 + (-4 / list[0]) = -6
list[4] = 5 + (5 / list[0]) = 7
list[5] = 1 (since the division by zero would cause an error)
If we assume that θ has been initialized to 0, then the code would update the array list as follows: Therefore, the updated array would contain the values {3, 27, 9, -6, 7, 1}.
To learn more about array click on the link below:
brainly.com/question/13950463
#SPJ4
Enter a formula in cell C13 to look up the registration fee for the first vehicle. Use the vehicle type in cell C4 as the Lookup_value argument. Use the RegistrationFees named range as the Table_array argument. The registration fees are located in column 2 of the data table. Require an exact match.
Answers
The formula that depicts the registration fee on the computer is Formula at C13 : =VLOOKUP(C4,Data!$B$10:$C$17,2,0)
How to illustrate the information?A computer program is a sequence or set of instructions in a programming language for a computer to execute.
Computer programs are one component of software, which also includes documentation and other intangible components. A computer program in its human-readable form is called source code
In this case, enter a formula in cell C13 to look up the registration fee for the first vehicle.
Then, one can use the vehicle type in cell C4 as the Lookup_value argument and then use the RegistrationFees named range as the Table_array argument.
Learn more about computer on:
https://brainly.com/question/24540334
#SPJ1
